Secured Data Transmission in IoT using Homomorphic Encryption
Keywords:
IOT systems, CGAN technologyAbstract
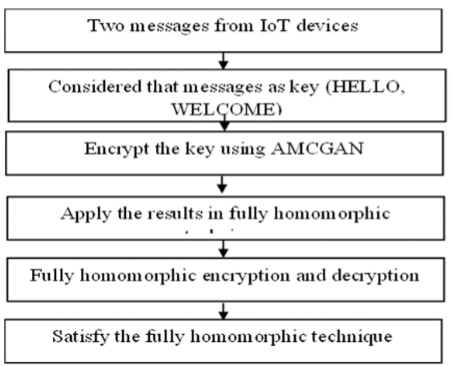
The IoT systems transfer highly sensitive data in a network and majority of the people needs IoT technology in real time applications like smart home, smart health care etc., A number of security algorithms exists to protect the IoT systems but with some time complexity. Deep learning is considered to be an efficient technique to analyze threats and respond to attacks and security incidents instantly and accurately. Conditional Generative Adversarial Network (CGAN) is one of the deep learning technique that protects data based on conditions created by generator and discriminator models. CGANs are useful for getting features of choice in generated data. This work use the CGAN feasibility to controllable the data encryption and decryption part in GAN network. This work solve the time complexity issues using Algebraic Matrix in Conditional GAN (AMCGAN) and Fully Homomorphic Encryption (FHE) algorithm. The advantage of using algebraic matrix is to reduce the time complexity and input complexity in cryptography process. It performs both addition and multiplication at the same time, and can compute any operation instantly. There are many encryption techniques used to encrypt the data but the same time they have more time to decrypt the result. Because the mathematical evaluation are complex to derived in encryption part and otherwise. So, this work considered to address the time complexity problem by solving the easiest mathematical derivations in encryption and decryption part. Also we noticed that the fully homomorphic encryption algorithm have less encryption time compared to Chaotic Algorithm and it has minimal time complexity than existing algorithms such as RSA algorithm.
Downloads
References
Hyeontaek Oh Gyu Myoung Lee, Sangdon Park And Jun Kyun Choi Hwanjo Heo), “Personal Data Trading Scheme for Data Brokers in IoT Data Marketplaces”, IEEE Access. 2019
Fangchao YuLi WangXianjin FangYouwen Zhang , “The Defense of Adversarial Example with Conditional Generative Adversarial Networks”, Security and Communication Networks.2020
Juan E. Tapia, Claudia , “ArellanoSoft-biometrics encoding conditional GAN for synthesis of NIR periocular images”, Future Generation Computer Systems.2019
Bulla, P. . “Traffic Sign Detection and Recognition Based on Convolutional Neural Network”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 4, Apr. 2022, pp. 43-53, doi:10.17762/ijritcc.v10i4.5533.
Vanitha, D. D. . (2022). Comparative Analysis of Power switches MOFET and IGBT Used in Power Applications. International Journal on Recent Technologies in Mechanical and Electrical Engineering, 9(5), 01–09. https://doi.org/10.17762/ijrmee.v9i5.368
K Thiagarajan, P Balasubramanian, J Nagaraj, J Padmashree “Encryption and decryption algorithm using algebraic matrix approach”, IOP Conf. Series: Journal of Physics: Conf. Series 1000.2018
Sarah Shihab Hamad, Ali Makki Sagheer “Public Key Fully Homomorphic Encryption”, Journal of Theoretical and Applied Information Technology 96(7), 1924-1934.2018
Weiru Wang, Yanfen Gan, Chi‑Man Vong, Chuangquan Chen “Homo‑ELM: fully homomorphic extreme learning machine”,. Int. J. Mach. Learn. & Cyber, 11, 1531–1540.2020
Delu Huang, Jianjun Wang , “High-capacity reversible data hiding in encrypted image based on specific encryption process”, Signal Processing: Image Communication, 80.2020
Lizhi Xiong, Danping Dong, Zhihua Xia And Xianyi Chen , “High-Capacity Reversible Data Hiding for Encrypted Multimedia Data With Somewhat Homomorphic Encryption”, IEEE Access, vol. 6, pp. 60635-60644.2018
Zhaoqing Pan, Weijie Yu, Xiaokai Yi, Asifullah Khan, Feng Yuan, and Yuhui Zheng Recent Progress on Generative Adversarial Networks (GANs): A Survey: IEEE Access, Vol.7.2019
Ahmed Cherif Megri, Sameer Hamoush, Ismail Zayd Megri, Yao Yu. (2021). Advanced Manufacturing Online STEM Education Pipeline for Early-College and High School Students. Journal of Online Engineering Education, 12(2), 01–06. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/47
Singh, S. . (2022). Unconditionally G ?odel Degeneracy for Quasi-Meager, Smooth Moduli. International Journal on Recent Trends in Life Science and Mathematics, 9(1), 28–36. https://doi.org/10.17762/ijlsm.v9i1.139
Baes, A. M. M. ., Adoptante, A. J. M. ., Catilo, J. C. A. ., Lucero, P. K. L. ., Peralta, J. F. P., & de Ocampo, A. L. P. (2022). A Novel Screening Tool System for Depressive Disorders using Social Media and Artificial Neural Network. International Journal of Intelligent Systems and Applications in Engineering, 10(1), 116–121. https://doi.org/10.18201/ijisae.2022.274
Xiaopu Zhang, Shuai Zhan, Jun Lin, Feng Sun, Xi Zhu, Yang Yang, Xunqian Tong, And Hongyuan Yang , “An Efficient Seismic Data Acquisition Based on Compressed Sensing Architecture with Generative Adversarial Networks”, IEEE access, Vol. 7.2019
Ghazaly, N. M. . (2022). Data Catalogue Approaches, Implementation and Adoption: A Study of Purpose of Data Catalogue. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(1), 01–04. https://doi.org/10.17762/ijfrcsce.v8i1.2063
Decheng Wu, Hailin Cao, Dian Li, And Shizhong Yang , “Energy-Efficient Reconstruction Method for Transmission Lines Galloping With Conditional Generative Adversarial Network”, IEEE Access, vol. 8, pp. 17310-17319.2020
Tushar Vyavahare, Darshana Tekade, Saurabh Nayak, N Suresh kumar and S S Blessy Trencia Lincy , “Enhanced rearrangement technique for secure data transmission: case study credit card process”, IOP Conf. Series: Materials Science and Engineering, 263 (4).2019
Hao Ye, Le Liang, Member, Geoffrey Ye Li, Fellow, and Biing-Hwang Juang , “Deep Learning-Based End-to-End Wireless Communication Systems with Conditional GANs as Unknown Channels”, IEEE Transactions on Wireless Communications, Vol. 19, No. 5.2020
Enju Xu, Yu Zhan, Zheng Wang, Baocang Wang And Yuan Ping , “Attack and Improvement on a Symmetric Fully Homomorphic Encryption Scheme”, IEEE Access. vol. 7, pp. 68373-68379,2019
Mohammed Aledhari, Marianne Di Pierro Mohamed Hefeida & Fahad Saeed , “ A Deep Learning-Based Data Minimization Algorithm for Fast and Secure Transfer of Big Genomic Datasets”, IEEE transactions on big data.2017
Farooq Shaikh and Elias Bou-Harb , “IoT Threat Detection Leveraging Network Statistics and GAN.2019
Akshay Mehrotra and Ambedkar Dukkipati , “Generative Adversarial Residual Pairwise Networks for One Shot Learning”, Computer Vision and Pattern Recognition.2017
Swaminathan.s, Ramasamy.k, Srinivasan.A, AB2IG – an Efficient Crypto System, ,Far East Journal off Electronics and Communications 16:171-78,DOI:10.17654/EC03010171, April 2016
S. Swaminathan;A. Karthick;S. Suganya, A secure and robust crypto system based on unique dynamic key generation scheme, Fifth International Conference on Computing, Communications and Networking Technologies (ICCCNT),IEEE,Year: 2014
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





