Deep Learning Based User Identity Management Protocol for Improving Security in Cloud Communication
Keywords:
Deep learning, SCIM, Security, Cloud ComputingAbstract
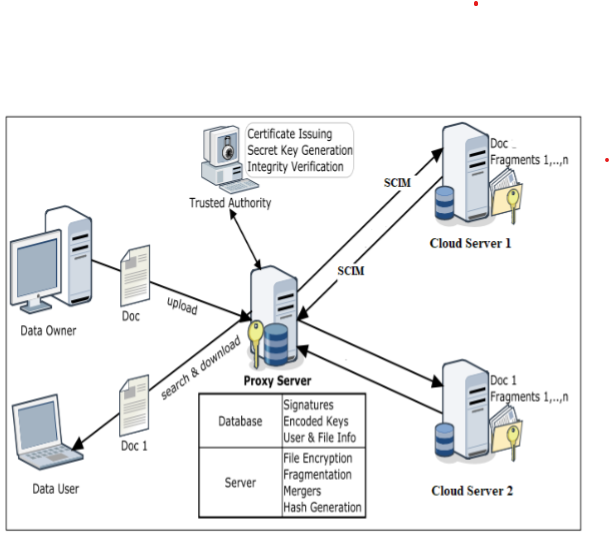
These instructions Deep learning (DL) based methods for communication protocol design have recently been explored inside the cloud computing paradigm. These learning-based systems can eliminate the need for manual protocol parameter tuning. To this purpose, we present a new DL-based framework for designing and evaluating networking protocols in a methodical manner. The suggested user identity management protocols, System for Cross-domain Identity Management (SCIM) is used to safeguard cloud computing clients and providers. Deep learning techniques employing SCIM were used to improve security and scalability. By preventing unwanted users from gaining access to the service/facility, the suggested deep Learning with SCIM would secure customers/cloud service providers' infrastructure and safeguard data at all levels, which is crucial for cloud computing facilities.
Downloads
References
A. Zeroual, M. Amroune, M. Derdour, A. Meraoumia, A. Bentahar Deep authentication model in Mobile Cloud Computing, 3rd International Conference on Pattern Analysis and Intelligent Systems (PAIS), IEEE (2018), pp. 1-4, 10.1109/PAIS.2018.8598508URL: https://ieeexplore.ieee.org/document/8598508/
Y. Wang, T. Nakachi, H. Ishihara, Edge and Cloud-aided Secure Sparse Representation for Face Recognition2019 27th European Signal Processing Conference, IEEE (2019), pp. 1-5, 10.23919 / EUSIPCO.2019.8903137.
Boyapati, B. ., and J. . Kumar. “Parasitic Element Based Frequency Reconfigurable Antenna With Dual Wideband Characteristics for Wireless Applications”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 6, June 2022, pp. 10-23, doi:10.17762/ijritcc.v10i6.5619.
Grance, T. and Jansen, W. (2011), Guidelines on Security and Privacy in Public Cloud Computing, Special Publication, National Institute of Standards and Technology, Gaithersburg, MD, [online], https://doi.org/10.6028/NIST.SP.800-144.
I. Indu, P.M. Rubesh Anand, Vidhyacharan Bhaskar, Identity and access management in cloud environment: Mechanisms and challenges, Engineering Science and Technology, an International Journal, Volume 21, Issue 4, 2018, Pages 574-588, ISSN 2215-0986, https://doi.org/10.1016/j.jestch.2018.05.010.
Gupta, D. J. . (2022). A Study on Various Cloud Computing Technologies, Implementation Process, Categories and Application Use in Organisation. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(1), 09–12. https://doi.org/10.17762/ijfrcsce.v8i1.2064
Rajkumar, N & Kannan, E. Deep learning-based key transmission (DLKT) protocol for secured group communication in cloud. Soft Computing, 2021, 25. 1-13. 10.1007/s00500-021-05959-z.
Annappaiah, Dinesha & Agrawal, V.K. (2012). Multi-level Authentication Technique for Accessing Cloud Services. 10.1109/ICCCA.2012.6179130.
Chen, Xiang & Xu, Lijun & Wei, Hua & Shang, Zhongan & Tingyu, Zhang & Zhang, Linghao. (2019). Emotion Interaction Recognition Based on Deep Adversarial Network in Interactive Design for Intelligent Robot. IEEE Access. 7. 1-1. 10.1109/ACCESS.2019.2953882.
Joy, P., Thanka, R., & Edwin, B. (2022). Smart Self-Pollination for Future Agricultural-A Computational Structure for Micro Air Vehicles with Man-Made and Artificial Intelligence. International Journal of Intelligent Systems and Applications in Engineering, 10(2), 170–174. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/1743
Tariq, Muhammad Imran, Memon, Nisar Ahmed, Ahmed, Shakeel et al., A Review of Deep Learning Security and Privacy Defensive Techniques, Mobile Information Systems, Hindawi, 2020, https://doi.org/10.1155/2020/6535834.
R. Cai, H. Li, S. Wang, C. Chen and A. C. Kot, "DRL-FAS: A Novel Framework Based on Deep Reinforcement Learning for Face Anti-Spoofing," in IEEE Transactions on Information Forensics and Security, vol. 16, pp. 937-951, 2021, doi: 10.1109/TIFS.2020.3026553.
Sally Fouad Shady. (2021). Approaches to Teaching a Biomaterials Laboratory Course Online. Journal of Online Engineering Education, 12(1), 01–05. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/43
Shengmin Xu , Guomin Yang , Yi Mu & Robert H Deng 2018, ‘Secure Fine-Grained Access Control and Data Sharing for Dynamic Groups in the Cloud’, IEEE Transactions on Information Forensics and Security, Vol. 13, No. 8, pp. 2101-2113.
Sumagita M, Riadi I, Soepomo JP, Warungboto U (2018) Analysis of secure hash algorithm (SHA) 512 for encryption process on web based application. Int J Cyber-Secur Digital for (IJCSDF) 7(4):373–381.
Ahmad, N., Cloud Computing: Technology, security issues and solutions. In Anti-Cyber Crimes (ICACC), 2017 2nd International Conference on. IEEE, 2017.
AlZadjali, A. M., A. H. Al-Badi, and S. Ali, An analysis of the security threats and vulnerabilities of cloud computing in oman. In Intelligent Networking and Collaborative Systems (INCOS), 2015 International Conference on. IEEE, 2015.
Jian Shen, Tianqi Zhou , Xiaofeng Chen , Jin Li & Willy Susilo 2018, ‘Anonymous and Traceable Group Data Sharing in Cloud Computing’, IEEE Transactions on Information Forensics and Security, Vol. 13, No. 4, pp. 912-925.
Yue Zhang , Jia Yu , Rong Hao , Cong Wang & Kui Ren 2018, ‘Enabling Efficient User Revocation in Identity-based Cloud Storage Auditing for Shared Big Data’, IEEE Transactions on Dependable and Secure Computing, pp. 1-13.
Mazhar Ali , Revathi Dhamotharan , Eraj Khan , Samee U Khan , Athanasios V Vasilakos ,Keqin Li & Albert Y Zomaya 2017, ‘SeDaSC: Secure Data Sharing in Clouds, IEEE Systems Journal , Vol. 11, No. 2, pp. 395-404.
Sebastian Graf, Patrick Lang, Stefan, A, Hohenadel & Marcel Waldvogel 2012, ‘Versatile Key Management for Secure Cloud Storage’, IEEE 31st Symposium on Reliable Distributed Systems, USA, pp. 469-474.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





