A Study on Supply Chain Management System Using Blockchain and IoT Technology
Keywords:
Blockchain, Internet of Things, Security, Privacy-assisted information exchange frameworkAbstract
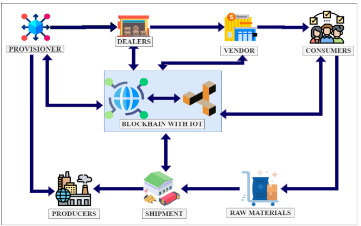
The Internet-of-Things (IoT) expanded rapidly, resulting in many services, software products, and electrical devices integrated with sensors. It is associated with protocols that are currently under development. Blockchain technology serves as the foundation for most IoT-based applications, and it must be adaptable and widely disseminated to guarantee their survival. Blockchain-based IoT has several limitations due to its resource-constrained nature, including security, scalability, traceability, efficiency, and network throughput. The suggested method in this paper is a Privacy-assisted Information Exchange Framework (P-IEF), an integrated security mechanism that detects suspicious activities in sensor nodes and locates them on a blacklist. This approach is a centered digital ledger procedure that ensures the privacy of all nodes and ensures that the data can be validated without modifying any node, and there is no need for a third party to secure data. The simulation analysis shows trust measures and open challenges, and research difficulties examined in IoT environments. The privacy-assisted information exchange framework has achieved a security ratio of 98.25 %, a scalability ratio of 97.15 %, traceability rate of 98.54%, efficiency rate of 99.01 %, and network throughput ratio of 97.19 % outperforms compared with other approaches.
Downloads
References
H. Liu, Y. Zhang and T. Yang, “Blockchain-enabled security in electric vehicles cloud and edge computing,” IEEE Network, Vol.4, No. 32(3) pp. 78-83, Jun 2018. DOI: 10.1109/MNET.2018.1700344
M. Abdel-Basset, R. Mohamed, K. Sallam and M. Elhoseny, “A novel decision-making model for sustainable supply chain finance under uncertainty environment,” Journal of Cleaner Production, Vol. 1;269:122324, Oct 2020. DOI:https://doi.org/10.1016/j.jclepro.2020.122324
S. Yousuf and D. Svetinovic, “Blockchain technology in supply chain management: Preliminary study,” In2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS) IEEE, Vol.22 (pp. 537-538) Oct 2019. DOI: 10.1109/IOTSMS48152.2019.8939222
Y. Luo, Q. Wei, Q. Ling and B.Huo, “Optimal decision in a green supply chain: Bank financing or supplier financing,” Journal of Cleaner Production, Vol.20;271:122090, Oct 2020. DOI:https://doi.org/10.1016/j.jclepro.2020.122090
Yang, J.-P. . “A Novel Storage Virtualization Scheme for Network Storage Systems”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 1, Jan. 2022, pp. 08-13, doi:10.17762/ijritcc.v10i1.5514.
SK. Sahu, DP. Mohapatra, JK. Rout, KS. Sahoo and AK.Luhach, “An Ensemble-Based Scalable Approach for Intrusion Detection Using Big Data Framework,” Big Data, Vol. 1;9(4):303-21, Aug 2021. DOI:https://doi.org/10.1089/big.2020.0201
DJ. Samuel and F.Cuzzolin, “Unsupervised anomaly detection for a Smart Autonomous Robotic Assistant Surgeon (SARAS) using a deep residual autoencoder,” arXiv preprint arXiv:2104.11008-22. Apr 2021. DOI: 10.1109/LRA.2021.3097244
Chaudhary, D. S. . (2022). Analysis of Concept of Big Data Process, Strategies, Adoption and Implementation. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(1), 05–08. https://doi.org/10.17762/ijfrcsce.v8i1.2065
J. Su, X. Chu and S.Kadry, “Internet-of-Things-Assisted Smart System 4.0 Framework Using Simulated Routing Procedures,” Sustainability, Vol. 12(15):6119, Jan 2020. DOI:https://doi.org/10.3390/su12156119
Saraireh, J., & Joudeh, H. (2022). An Efficient Authentication Scheme for Internet of Things. International Journal of Communication Networks and Information Security (IJCNIS), 13(3). https://doi.org/10.17762/ijcnis.v13i3.3422
K. Seyhan, TN. Nguyen, S. Akleylek and K.Cengiz, “Lattice-based cryptosystems for the security of resource-constrained IoT devices in post-quantum world: a survey,” Cluster Computing, Vol. 13:1-20, Aug 2021. DOI:https://doi.org/10.1007/s10586-021-03380-7
G. Amudha, “Dilated Transaction Access and Retrieval: Improving the Information Retrieval of Blockchain-Assimilated Internet of Things Transactions,” Wireless Personal Communications, Vol. 6:1-21, Feb 2021. DOI:https://doi.org/10.1007/s11277-021-08094-y
Linda R. Musser. (2020). Older Engineering Books are Open Educational Resources. Journal of Online Engineering Education, 11(2), 08–10. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/41
J. Gao, H. Wang and H. Shen, “Task failure prediction in cloud data centers using deep learning,” IEEE Transactions on Services Computing, Vol. 11, May 2020. DOI: 10.1109/TSC.2020.2993728
F. Wang, N. Yang, PM. Shakeel and V. Saravanan, “Machine learning for mobile network payment security evaluation system,” Transactions on Emerging Telecommunications Technologies, Vol. 28:e4226, Jan 2021. DOI:https://doi.org/10.1002/ett.4226
BS. Rawal, G. Manogaran and M. Hamdi, “Multi-Tier Stack of Block Chain with Proxy Re-Encryption Method Scheme on the Internet of Things Platform,” ACM Transactions on Internet Technology (TOIT), Vol. 22(2):1-20, Oct 2021. DOI:https://doi.org/10.1145/3421508
G. Amudha and P. Narayanasamy, “Distributed location and trust based replica detection in wireless sensor networks,” Wireless Personal Communications, Vol. 102(4):3303-21, Oct 2018. DOI:https://doi.org/10.1007/s11277-018-5369-2
K. Seyhan, TN. Nguyen, S. Akleylek, K. Cengiz and SH.Islam, “Bi-GISIS KE: Modified key exchange protocol with reusable keys for IoT security,” Journal of Information Security and Applications, Vol. 1;58:102788, May 2021. DOI:https://doi.org/10.1016/j.jisa.2021.102788
XY. Liu, H. Yang, J. Gao and C. Wang, “FinRL: Deep reinforcement learning framework to automate trading in quantitative finance,” Available at SSRN 3955949, Vol. 4, Nov 2021. DOI:https://doi.org/10.48550/arXiv.2111.09395
G. Manogaran, J. Ngangmeni, J. Stewart, DB. Rawat and TN. Nguyen, “Deep Learning-based Concurrent Resource Allocation for Enhancing Service Response in Secure 6G Network-in-Box Users using IIoT,” IEEE Internet of Things Journal. Vol. 12, Oct 2021. DOI: 10.1109/JIOT.2021.3119336
R. Rajakumar, K. Sekaran, CH. Hsu and S.Kadry, “Accelerated grey wolf optimization for global optimization problems,” Technological Forecasting and Social Change, Vol. 1;169:120824, Aug 2021. DOI:https://doi.org/10.1016/j.techfore.2021.120824
AA. Abd EL-Latif, B. Abd-El-Atty, SE. Venegas-Andraca and W.Mazurczyk, “Efficient quantum-based security protocols for information sharing and data protection in 5G networks,” Future Generation Computer Systems, Vol. 1;100:893-906, Nov 2019. DOI:https://doi.org/10.1016/j.future.2019.05.053
S. Dey, S. Pal and V.Saravanan, “Computational Offloading with Deep Supervised Learning for Edge enabled IoT,” InTechnological Advances in Science, Medicine and Engineering Conference 2021, Vol. 18, Jun 2021. DOI: 10.1109/JIOT.2020.2981557
M. Hader, A. El-Mhamedi, A. Abouabdellah, “Blockchain Integrated ERP for a Better Supply Chain Management,” In2021 The 8th International Conference on Industrial Engineering and Applications (Europe), Vol. 8 (pp. 193-197), Jan 2021. DOI:10.1109/ICIEA49774.2020.9102084
C. Jiang and C. Ru, “Application of Blockchain Technology in Supply Chain Finance. In2020 5th International Conference on Mechanical,” Control and Computer Engineering (ICMCCE) , Vol. 25 (pp. 1342-1345), Dec 2020. IEEE. DOI: 10.1109/ICMCCE51767.2020.00294
SR. Niya, D. Dordevic, AG. Nabi and T. Mann, “Stiller B. A platform-independent, generic-purpose and blockchain-based supply chain tracking,” In2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC) , Vol. 14 (pp. 11-12), May 2019. IEEE. DOI: 10.1109/BLOC.2019.8751415
Y. Yue and X.Fu, “Research on Medical Equipment Supply Chain Management Method Based on Blockchain Technology,” In2020 International Conference on Service Science (ICSS), Vol. 24 (pp. 143-148), Aug 2020. IEEE. DOI: 10.1109/ICSS50103.2020.00030
M. Hölbl, M. Kompara, A. Kamišalić and L.Nemec Zlatolas, “A systematic review of the use of blockchain in healthcare,” Symmetry. Vol. 10(10):470, Oct 2018. DOI:https://doi.org/10.3390/sym10100470
NN. Ahamed, TK. Thivakaran and P.Karthikeyan, “Perishable Food Products Contains Safe in Cold Supply Chain Management Using Blockchain Technology,” In2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), (Vol. 1, pp. 167-172), Mar 2021. IEEE. DOI: 10.1109/ICACCS51430.2021.9442057
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





