Efficient Data Security through Visual Security and Stegnography Schemes
Keywords:
Lifting wavelet transform, Reversible data hiding, Adaptive LSB replacement, Chaos encryptionAbstract
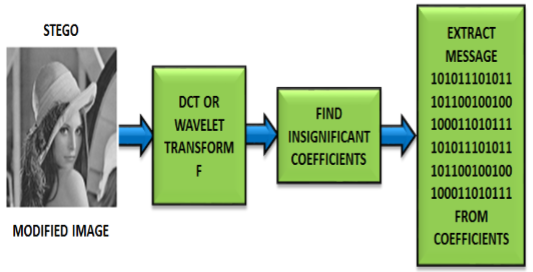
In this paper an information preservation upgrade framework is proposed for secure correspondence depending on reversible information covering through encoded pictures with reserve room method. This was actualized on real RGB picture under hold room method for multi scale disintegration. The Blue color was selected for concealing secure content information. The picture is diffused into local blocks and discrete wavelet is utilized to identify the estimation of gritty coefficients. The estimation part is scrambled by utilizing chaos based encryption technique. The suggested encryption system uses keys for image encoding in addition to improving the security of data bearer confidentiality by making the data challenging to access for any gatecrasher with an arbitrary technique. After encrypting the image, the information hider will disguise a mystery data into an itemized coefficient which are held prior to encryption. Despite encryption accomplishes certain safety impacts, it makes the mystery informations muddled and insignificant. The framework is as further improved with encoded messages by utilizing a symmetrical key technique. That is why our safety method is also known as reverse information covering. The art of secret correspondence involves hiding the current information in another medium. The method of information concealment uses flexible LSB calculations to hide a secret data bits in jumbled image. The mysterious data is removed in an information recovery setup by using the appropriate key to select the encoded pixel and separate the information. By utilizing the decoding key, the picture and extricated content info will be removed from encryption to get a first data. At last the effectiveness of the proposed encryption and information concealing method is examined dependent on picture and information recuperation.
Downloads
References
J. Zhou, W. Sun, L. Dong, X. Liu, O.C. Au and Y.Y. Tang, “Secure reversible image data hiding over encrypted domain via key modulation”, IEEE transactions on circuits and systems for video technology. Vol. 26, No. 3, pp. 441–452, 2015.
W. Zhang, H. Wang, D. Hou and N. Yu, “Reversible data hiding in encrypted images by reversible image transformation”, IEEE Transactions on multimedia, Vol. 18, No. 8, pp.1469-1479, 2016.
X. Zhang, “Reversible data hiding in encrypted image”, IEEE signal processing letters. Vol. 18, No. 4, pp.255-258, 2011.
X. Zhang, J. Long, Z. Wang and H. Cheng, “Lossless and reversible data hiding in encrypted images with public-key cryptography”, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 26, No. 9, pp.1622–1631, 2015.
M. J. Traum, J. Fiorentine. (2021). Rapid Evaluation On-Line Assessment of Student Learning Gains for Just-In-Time Course Modification. Journal of Online Engineering Education, 12(1), 06–13. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/45
Z. Qian, X. Zhang and S. Wang, “Reversible data hiding in encrypted JPEG bit stream”, IEEE transactions on multimedia, Vol. 16, No. 5, p.1486-1491, 2014.
Z. Qian and X. Zhang, “Reversible data hiding in encrypted images with distributed source encoding”, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 26, No. 4, pp.636-646, 2015.
F. Peng, Z.X. Lin, X. Zhang and M. Long, “Reversible data hiding in encrypted 2D vector graphics based on reversible mapping model for real numbers”, IEEE transactions on information forensics and security, Vol. 14, No. 9, pp.2400-2411, 2019.
Chauhan, T., and S. Sonawane. “The Contemplation of Explainable Artificial Intelligence Techniques: Model Interpretation Using Explainable AI”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 4, Apr. 2022, pp. 65-71, doi:10.17762/ijritcc.v10i4.5538.
Z. Qian, H. Xu, X. Luo and X. Zhang, “New framework of reversible data hiding in encrypted JPEG bit streams”, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 29, No. 2, pp.351-362, 2018.
Y.C. Chen, T.H. Hung, S.H. Hsieh and C.W. Shiu, “A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic algorithms”, IEEE Transactions on Information Forensics and Security, Vol. 14, No. 12, pp.3332-3343, 2019.
H. Ge, Y. Chen, Z. Qian and J. Wang, “A high capacity multi-level approach for reversible data hiding in encrypted images”, IEEE Transactions on Circuits and Systems for Video Technology, Vol. 29, No. 8, pp.2285-2295, 2018.
F. Ernawan, D. Ariatmanto and A. Firdaus, "An improved image watermarking by modifying selected DWT-DCT coefficients”, in IEEE Access, Vol. 9, pp. 45474-45485, 2021.
F. A. Jassim, “A novel steganography algorithm for hiding text in image using five modulus methods”, arXiv preprint, 2013.
K. Muhammad, J. Ahmad, N.U. Rehman, Z. Jan, R.J. Qereshi “A secure cyclic steganographic technique for color images using randomization”, Tech J Univ Eng Technol Taxila Pakistan Vol. 19, pp. 57–64, 2014.
Joy, P., Thanka, R., & Edwin, B. (2022). Smart Self-Pollination for Future Agricultural-A Computational Structure for Micro Air Vehicles with Man-Made and Artificial Intelligence. International Journal of Intelligent Systems and Applications in Engineering, 10(2), 170–174. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/1743
K. Muhammad, J. Ahmad, H. Farman, M. Zubair, “A novel image steganographic approach for hiding text in color images using HSI color model”, Middle-East J Sci Res, 2014.
M. Karim “A new approach for LSB based image steganogra-phy using secret key”, 14th International Conference on Computer and Information Technology, pp 286–291, 2011
K. Muhammad, M. Sajjad, I. Mehmood, S. Rho and S. W. Baik, “A novel magic LSB substitution method (M-LSB-SM) using multi-level encryption and achromatic component of an image”, Multimedia Tools and Applications, Vol. 75, No. 22, pp. 14867-14893, 2016.
E. H. Rachmawanto and C. A. Sari, “Secure image steganography algorithm based on DCT with OTP encryption”, Journal of Applied Intelligent System, Vol. 2, No. 1, pp.1-11, 2017
D. Bandyopadhyay, K. Dasgupta, J. K. Mandal and P. Dutta, “A novel secure image steganography method based on Chaos theory in spatial domain”, International Journal of Security, Privacy and Trust Management (IJSPTM), Vol. 3, No. 1, pp.11-22, 2014.
Garg, D. K. . (2022). Understanding the Purpose of Object Detection, Models to Detect Objects, Application Use and Benefits. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(2), 01–04. https://doi.org/10.17762/ijfrcsce.v8i2.2066
P. K. Dhar, A. Kaium and T. Shimamura, “Image steganography based on modified LSB substitution method and data mapping”, International Journal of Computer Science and Network Security, Vol. 18, No. 3, pp. 155-160, 2018.
M. Juneja and P. S. Sandhu, “A new approach for information security using an improved steganography technique”, Journal of Information Processing Systems, Vol. 9. No. 3, pp.405-424, 2013.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





