Optimized Maxout Classifier for Detection of DDoS Attack in SDN
Keywords:
Software-Defined Networking, DDoS Attack Detection, Coot Algorithm, Deep Maxout, SMI-CA ModelAbstract
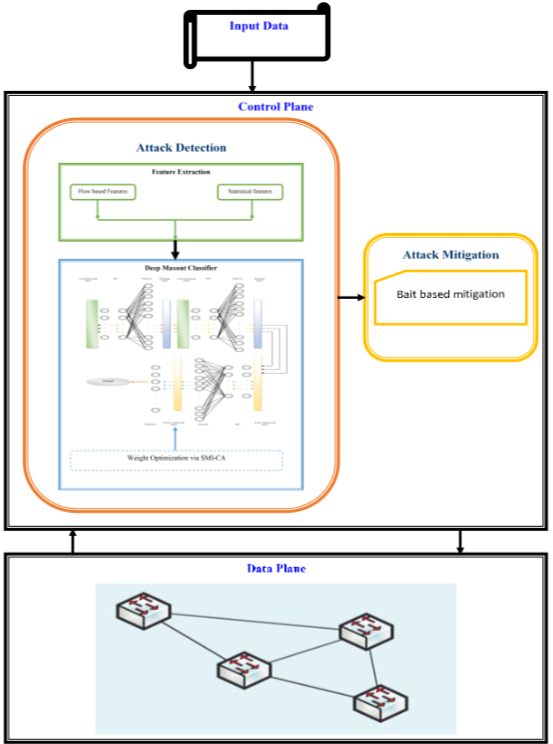
The SDN has increased its focus, and the notion of network control has offered an efficient network-oriented DDoS protection in addition to many DDoS assault methods. More information about the network might be influenced by the centralized SDN controller, and SDN framework helps in identifying DDoS assaults using various methods. The simulation dataset for this work was generated by constructing SDN on the Mininet emulator. To construct the dataset and train the deep learning algorithm, the unique features are logged into a csv file. Further, detection is done using Optimized Deep Max out classifier. In addition, the weights of Deep Max out classifier are chosen via Sine Map Insisted CA (SMI-CA) model. If any attack is found, Bait oriented mitigation is made for relieving from attacks. As last step, analysis is done to portray the effectiveness of adopted model. The model used in the paper is further evaluated using the newly released dataset CICDDoS2019 along with the simulation dataset. Result shows that the Deep Maxout classifier has a very low false alarm rate and can classify traffic with the greatest testing accuracy of 96.5% for the CICDoS2019 dataset and 95.1% for the simulation dataset.
Downloads
References
N. Ravi and S. M. Shalinie, "Learning-Driven Detection and Mitigation of DDoS Attack in IoT via SDN-Cloud Architecture," IEEE Internet of Things Journal, vol. 7, no. 4, pp. 3559-3570, April 2020, doi: 10.1109/JIOT.2020.2973176.
J. A. Pérez-Díaz, I. A. Valdovinos, K. -K. R. Choo and D. Zhu, "A Flexible SDN-Based Architecture for Identifying and Mitigating Low-Rate DDoS Attacks Using Machine Learning," IEEE Access, vol. 8, pp. 155859-155872, 2020, doi: 10.1109/ACCESS.2020.3019330.
S. Dong and M. Sarem, "DDoS Attack Detection Method Based on Improved KNN With the Degree of DDoS Attack in Software-Defined Networks," in IEEE Access, vol. 8, pp. 5039-5048, 2020, doi: 10.1109/ACCESS.2019.2963077.
Krishna, P. R. ., and P. . Rajarajeswari. “EapGAFS: Microarray Dataset for Ensemble Classification for Diseases Prediction”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 8, Aug. 2022, pp. 01-15, doi:10.17762/ijritcc.v10i8.5664.
K. S. Sahoo et al., "An Evolutionary SVM Model for DDOS Attack Detection in Software Defined Networks," in IEEE Access, vol. 8, pp. 132502-132513, 2020, doi: 10.1109/ACCESS.2020.3009733.
S. Haider et al., "A Deep CNN Ensemble Framework for Efficient DDoS Attack Detection in Software Defined Networks," in IEEE Access, vol. 8, pp. 53972-53983, 2020, doi: 10.1109/ACCESS.2020.2976908.
Y. Yu, L. Guo, Y. Liu, J. Zheng and Y. Zong, "An Efficient SDN-Based DDoS Attack Detection and Rapid Response Platform in Vehicular Networks," in IEEE Access, vol. 6, pp. 44570-44579, 2018, doi: 10.1109/ACCESS.2018.2854567.
M. A. Aladaileh, M. Anbar, I. H. Hasbullah, Y. -W. Chong and Y. K. Sanjalawe, “Detection Techniques of Distributed Denial of Service Attacks on Software-Defined Networking Controller–A Review," in IEEE Access, vol. 8, pp. 143985-143995, 2020, doi: 10.1109/ACCESS.2020.3013998.
K. S. Sahoo et al., "An Evolutionary SVM Model for DDOS Attack Detection in Software Defined Networks," in IEEE Access, vol. 8, pp. 132502-132513, 2020, doi: 10.1109/ACCESS.2020.3009733.
Z. Abou El Houda, L. Khoukhi and A. Senhaji Hafid, "Bringing Intelligence to Software Defined Networks: Mitigating DDoS Attacks," in IEEE Transactions on Network and Service Management, vol. 17, no. 4, pp. 2523-2535, Dec. 2020, doi: 10.1109/TNSM.2020.3014870.
M. P. Novaes, L. F. Carvalho, J. Lloret and M. L. Proença, "Long Short-Term Memory and Fuzzy Logic for Anomaly Detection and Mitigation in Software-Defined Network Environment," in IEEE Access, vol. 8, pp. 83765-83781, 2020, doi: 10.1109/ACCESS.2020.2992044.
B. Wang, Y. Sun and X. Xu, "A Scalable and Energy-Efficient Anomaly Detection Scheme in Wireless SDN-Based mMTC Networks for IoT," in IEEE Internet of Things Journal, vol. 8, no. 3, pp. 1388-1405, 1 Feb.1, 2021, doi: 10.1109/JIOT.2020.3011521.
T. V. Phan, T. G. Nguyen, N. -N. Dao, T. T. Huong, N. H. Thanh and T. Bauschert, "DeepGuard: Efficient Anomaly Detection in SDN With Fine-Grained Traffic Flow Monitoring," in IEEE Transactions on Network and Service Management, vol. 17, no. 3, pp. 1349-1362, Sept. 2020, doi: 10.1109/TNSM.2020.3004415.
Y. Xu, H. Sun, F. Xiang and Z. Sun, "Efficient DDoS Detection Based on K-FKNN in Software Defined Networks," in IEEE Access, vol. 7, pp. 160536-160545, 2019, doi: 10.1109/ACCESS.2019.2950945.
Ghazaly, N. M. . (2022). Data Catalogue Approaches, Implementation and Adoption: A Study of Purpose of Data Catalogue. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(1), 01–04. https://doi.org/10.17762/ijfrcsce.v8i1.2063
B. Wang, Y. Sun and X. Xu, "Loose Game Theory Based Anomaly Detection Scheme for SDN-Based mMTC Services," in IEEE Access, vol. 7, pp. 139350-139357, 2019, doi: 10.1109/ACCESS.2019.2943056.
Bawany, N.Z., Shamsi, J.A. & Salah, K. DDoS Attack Detection and Mitigation Using SDN: Methods, Practices, and Solutions. Arab J Sci Eng 42, 425–441 (2017).
Wani, A., Revathi, S. DDoS Detection and Alleviation in IoT using SDN (SDIoT-DDoS-DA). J. Inst. Eng. India Ser. B 101, 117–128 (2020). https://doi.org/10.1007/s40031-020-00442-z
Bhushan, K., Gupta, B.B. Distributed denial of service (DDoS) attack mitigation in software defined network (SDN)-based cloud computing environment. J Ambient Intell Human Comput 10, 1985–1997 (2019). https://doi.org/10.1007/s12652-018-0800-9
Harikrishna, P., Amuthan, A. SDN-based DDoS Attack Mitigation Scheme using Convolution Recursively Enhanced Self Organizing Maps. Sādhanā 45, 104 (2020). https://doi.org/10.1007/s12046-020-01353-x
Sahoo, K.S., Panda, S.K., Sahoo, S. et al. Toward secure software-defined networks against distributed denial of service attack. J Supercomput 75, 4829–4874 (2019). https://doi.org/10.1007/s11227-019-02767-z
Mousavi, S.M., St-Hilaire, M. Early Detection of DDoS Attacks Against Software Defined Network Controllers. J Netw Syst Manage 26, 573–591 (2018). https://doi.org/10.1007/s10922-017-9432-1
https://www.kaggle.com/code/accountstatus/maxout-network-vs-normal-cnn/notebook
IrajNaruei, FarshidKeynia, "A new optimization method based on COOT bird natural life model", Expert Systems With Applications, vol. 183, 2021.
B. R. Rajakumar, "Impact of Static and Adaptive Mutation Techniques on Genetic Algorithm", International Journal of Hybrid Intelligent Systems, vol. 10, no. 1, pp. 11-22, 2013, DOI: 10.3233/HIS-120161.
B. R. Rajakumar, "Static and Adaptive Mutation Techniques for Genetic algorithm: A Systematic Comparative Analysis", International Journal of Computational Science and Engineering, vol. 8, no. 2, pp. 180-193, 2013, DOI: 10.1504/IJCSE.2013.053087.
S. M. Swamy, B. R. Rajakumar and I. R. Valarmathi, “Design of Hybrid Wind and Photovoltaic Power System using Opposition-based Genetic Algorithm with Cauchy Mutation”, IET Chennai Fourth International Conference on Sustainable Energy and Intelligent Systems (SEISCON 2013), Chennai, India, Dec. 2013, DOI: 10.1049/ic.2013.0361
Paithane, P. M., & Kakarwal, D. (2022). Automatic Pancreas Segmentation using A Novel Modified Semantic Deep Learning Bottom-Up Approach. International Journal of Intelligent Systems and Applications in Engineering, 10(1), 98–104. https://doi.org/10.18201/ijisae.2022.272
Aloysius George and B. R. Rajakumar, "APOGA: An Adaptive Population Pool Size based Genetic Algorithm", AASRI Procedia - 2013 AASRI Conference on Intelligent Systems and Control (ISC 2013), vol. 4, pp. 288-296, 2013, DOI: https://doi.org/10.1016/j.aasri.2013.10.043.
Ahmed Cherif Megri, Sameer Hamoush, Ismail Zayd Megri, Yao Yu. (2021). Advanced Manufacturing Online STEM Education Pipeline for Early-College and High School Students. Journal of Online Engineering Education, 12(2), 01–06. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/47
B. R. Rajakumar and Aloysius George, "A New Adaptive Mutation Technique for Genetic Algorithm", In proceedings of IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), pp. 1-7, Dec 18-20, Coimbatore, India, 2012, DOI: 10.1109/ICCIC.2012.6510293.
Mukund B. Wagh and Dr. Gomathi N, "Improved GWO-CS Algorithm-Based Optimal Routing Strategy in VANET", Journal of Networking and Communication Systems, Vol.2,No.1, pp.34-42,2019.
Sadashiv Halbhavi B,Kodad S F,Ambekar S K,Manjunath D, "Enhanced Invasive Weed Optimization Algorithm with Chaos Theory for Weightage based Combined Economic Emission Dispatch", Journal of Computational Mechanics, Power System and Control, Vol.2,No.3, pp.19-27,2019.
Amolkumar Narayan Jadhav,Gomathi N, "DIGWO: Hybridization of Dragonfly Algorithm with Improved Grey Wolf Optimization Algorithm for Data Clustering", Multimedia Research, Vol.2,No.3, pp.1-11,2019.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





