A Generic Framework for Sharing Data Using Attribute Based Cryptography in Hybrid Cloud
Keywords:
No keywordsAbstract
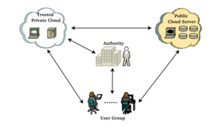
Now a days, large organizations are re-appropriating their information to the public cloud. But we should be cautious and improve the security about the data which is being shared. Maintaining the confidentiality among this public data is a major concern. To accomplish this a hybrid cloud Computing was intended to help safe & proficient contribution of information. Private cloud capacities go about as extension among clients & public cloud. As the organizations expand and create the hybrid Cloud requirement that can securely monitor information in clouds by entering interest. By providing online record sharing on the internet, the hybrid cloud has successfully met the needs of business customers. It offers an adaptable and versatile administrative environment. This property has made the hybrid cloud as mainstream administration in all businesses. This Work presents another plan of secure information sharing structure utilizing Proper cryptography for active assembly in hybrid cloud environment, which has the following features: Improved development of Ciphertext-Policy Attribute-Based Encryption through assigning ability of mutually encryption/decoding computation from client. Efficient access control through protection safeguarding highlights in cloud, In the client side decrease of calculations.
Downloads
References
S. U. Khan and N. Ullah, “Challenges in the adoption of hybrid cloud: an exploratory study using systematic literature review,” J. Eng., vol. 2016, no. 5, pp. 107–118, 2016, doi: 10.1049/joe.2016.0089.
K. Bakshi, “Secure hybrid cloud computing: Approaches and use cases,” IEEE Aerosp. Conf. Proc., pp. 1–8, 2014, doi: 10.1109/AERO.2014.6836198.
A. Gordon, “The Hybrid Cloud Security Professional,” IEEE Cloud Comput., vol. 3, no. 1, pp. 82–86, 2016, doi: 10.1109/MCC.2016.21.
J. K. Wang and X. Jia, “Data security and authentication in hybrid cloud computing model,” 2012. doi: 10.1109/GHTCE.2012.6490136.
M. Raza, A. Imtiaz, and U. Shoaib, “A review on security issues and their impact on hybrid cloud computing environment,” Int. J. Adv. Comput. Sci. Appl., vol. 10, no. 3, pp. 353–357, 2019, doi: 10.14569/IJACSA.2019.0100346.
N. M. Reddy, G. Ramesh, S. B. Kasturi, D. Sharmila, G. Gopichand, and L. T. Robinson, “Secure data storage and retrieval system using hybridization of orthogonal knowledge swarm optimization and oblique cryptography algorithm in cloud,” Appl. Nanosci., 2022, doi: 10.1007/s13204-021-02174-y.
G. Aryotejo, D. Y. Kristiyanto, and Mufadhol, “Hybrid cloud: Bridging of private and public cloud computing,” J. Phys. Conf. Ser., vol. 1025, no. 1, pp. 0–7, 2018, doi: 10.1088/1742-6596/1025/1/012091.
N. Thirupathi, K. Madhavi, G. Ramesh, and K. Sowmya Priya, “Data Storage in Cloud Using Key-Policy Attribute-Based Temporary Keyword Search Scheme (KP-ABTKS),” in Lecture Notes in Networks and Systems, vol. 98, 2020. doi: 10.1007/978-3-030-33846-6_67.
M. Pirretti, P. Traynor, P. McDaniel, and B. Waters, “Secure attribute-based systems,” J. Comput. Secur., vol. 18, no. 5, pp. 799–837, 2010, doi: 10.3233/JCS-2009-0383.
A. Balu and K. Kuppusamy, “An expressive and provably secure Ciphertext-Policy Attribute-Based Encryption,” Inf. Sci. (Ny)., vol. 276, no. subaward 641, pp. 354–362, 2014, doi: 10.1016/j.ins.2013.12.027.
P. Dileep Kumar Reddy, R. Praveen Sam, and C. Shoba Bindu, “Optimal blowfish algorithm-based technique for data security in cloud,” Int. J. Bus. Intell. Data Min., vol. 11, no. 2, pp. 171–189, 2016, doi: 10.1504/IJBIDM.2016.081605.
and M. Z. Yingjie Xia, Li Kuang, “A hierarchical access control scheme in cloud using hhecc,” J. Phys. A Math. Theor., vol. 44, no. 8, pp. 1689–1699, 2011, doi: 10.1088/1751-8113/44/8/085201.
Y. Zhu, H. Hu, G.-J. Ahn, Y. Han, and S. Chen, “Collaborative Integrity Verification in Hybrid Clouds,” no. May 2014, 2012, doi: 10.4108/icst.collaboratecom.2011.247089.
S. Belguith, N. Kaaniche, A. Jemai, M. Laurent, and R. Attia, “PAbAC: A privacy preserving attribute based framework for fine grained access control in clouds,” ICETE 2016 - Proc. 13th Int. Jt. Conf. E-bus. Telecommun., vol. 4, pp. 133–146, 2016, doi: 10.5220/0005968201330146.
B. Waters, “Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 6571 LNCS, no. subaward 641, pp. 53–70, 2011, doi: 10.1007/978-3-642-19379-8_4.
N. Eltayieb, P. Wang, A. Hassan, R. Elhabob, and F. Li, “ASDS: Attribute-based secure data sharing scheme for reliable cloud environment,” Secur. Priv., vol. 2, no. 2, p. e57, Mar. 2019, doi: 10.1002/spy2.57.
X. Lu, Z. Pan, and H. Xian, “An efficient and secure data sharing scheme for mobile devices in cloud computing,” J. Cloud Comput., vol. 9, no. 1, 2020, doi: 10.1186/s13677-020-00207-5.
J. Bethencourt, A. Sahai, and B. Waters, “Ciphertext-policy attribute-based encryption,” Proc. - IEEE Symp. Secur. Priv., pp. 321–334, 2007, doi: 10.1109/SP.2007.11.
Z. Zhou, D. Huang, S. Member, and Z. Wang, “Ef fi cient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption,” IEEE Trans. Comput., vol. 64, no. 1, pp. 126–138, 2015.
S. T. Ali and B. B. Amberker, “A dynamic constant size attribute-based group signature scheme with attribute anonymity,” Int. J. Inf. Privacy, Secur. Integr., vol. 1, no. 4, p. 312, 2013, doi: 10.1504/ijipsi.2013.058207.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





