An Evaluation of Sybil Attack’s Detection Approaches in Vehicular Ad-Hoc Networks (VANETs)
Keywords:
: Vehicular, Ad-Hoc Networks (VANETs), Sybil attacks, Social Networks, WSNAbstract
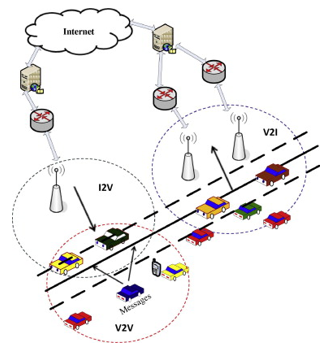
Vehicular ad hoc networks (VANETs) are being used and progressively promoted for traffic control and accident prevention. A malicious node can be manufactured to be several vehicle nodes in a Sybil attack. It is generally agreed that vehicular ad hoc networks (VANETs) must rely heavily on peer-to-peer correspondence and malignant data traffic with the ultimate goal of achieving execution goals. The Sybil attack undermines attacks in which the aggressor deceives different nodes by the same incorrect ID or copy ID of the clients aware of the nodes in the WSN. Sybil attacks are named after an anecdotal personality with issues of dissociative uniqueness. The web-based social networking is under Sybil’s attack, and it affects the entire system. By multiplying deceptive profiles using false characteristics, Sybil attacks are attacks against informal online organizations’ reputations. In online social networks, bogus profiles have become a continuous and evolving danger. The line between the physical and online worlds is getting obscured as organizations and individuals grasp social networks. So, distinguishing, countering, and containing counterfeit records on online networks is critical. We collected datasets and performed a simulation to detect Sybil attacks. A dataset, which contains 1048576 records, is selected. A big data issue is a large dataset, so it was divided into chunks. The partitioned datasets are 11, and for detecting a Sybil attack, each is simulated. For detecting Sybil attacks in the network, a methodology is proposed. Sybil attacks have been detected by checking the similarity of each node’s attributes to existing nodes.
Downloads
References
M. Soni and A. Jain, "Secure Communication and Implementation Technique for Sybil Attack in Vehicular Ad-Hoc Networks," in 2018 Second International Conference on Computing Methodologies and Communication (ICCMC), 2018, pp. 539-543: IEEE.
M. Maleknasab Ardakani, M. A. Tabarzad, and M. A. Shayegan, "Detecting sybil attacks in vehicular ad hoc networks using fuzzy logic and arithmetic optimization algorithm," The Journal of Supercomputing, pp. 1-33, 2022.
K. Hussain, S. J. Hussain, N. Jhanjhi, and M. Humayun, "SYN flood attack detection based on bayes estimator (SFADBE) for MANET," in 2019 International Conference on Computer and Information Sciences (ICCIS), 2019, pp. 1-4: IEEE.
C. Iwendi, M. Uddin, J. A. Ansere, P. Nkurunziza, J. Anajemba, and A. K. Bashir, "On Detection of Sybil Attack in Large-Scale VANETs Using Spider-Monkey Technique," IEEE Access, vol. 6, pp. 47258-47267, 2018.
S. S. Sefati and S. G. Tabrizi, "Detecting sybil attack in vehicular ad-hoc networks (vanets) by using fitness function, signal strength index and throughput," Wireless Personal Communications, vol. 123, no. 3, pp. 2699-2719, 2022.
N. K. Chaubey and D. Yadav, "Detection of Sybil attack in vehicular ad hoc networks by analyzing network performance," International Journal of Electrical & Computer Engineering (2088-8708), vol. 12, no. 2, 2022.
Z. Helmi, R. Adriman, T. Y. Arif, H. Walidainy, and M. Fitria, "Sybil Attack Prediction on Vehicle Network Using Deep Learning," Jurnal RESTI (Rekayasa Sistem Dan Teknologi Informasi), vol. 6, no. 3, pp. 499-504, 2022.
M. S. Naveed and M. H. Islam, "Detection of Sybil Attacks in Vehicular Ad hoc Networks Based on Road Side Unit Support," Int. J. Sci. Eng. Res, vol. 6, no. 2, pp. 817-827, 2015.
S. A. Asra, "Security issues of Vehicular Ad Hoc Networks (VANET): A Systematic Review," TIERS Information Technology Journal, vol. 3, no. 1, pp. 17-27, 2022.
D. Singh and M. Kaur, "Mitigation of Sybil Attack Using Location Aware Nodes in VANET," International Journal of Science and Research (IJSR), vol. 4, no. 11, 2015.
H. Kaur and P. Bansal, "Efficient Detection & Prevention of Sybil Attack in VANET," International Journal of Innovative Science, Engineering & Technology, vol. 2, no. 9, 2015.
M. Khalil and M. A. Azer, "Sybil attack prevention through identity symmetric scheme in vehicular ad-hoc networks," in Wireless Days (WD), 2018, 2018, pp. 184-186: IEEE.
S. S. Vinayagam and V. Parthasarathy, "A secure restricted identity-based proxy re-encryption based routing scheme for sybil attack detection in peer-to-peer networks," Journal of Computational and Theoretical Nanoscience, vol. 15, no. 1, pp. 210-221, 2018.
M. Jain and R. Saxena, "VANET: Security Attacks, Solution and Simulation," in Proceedings of the Second International Conference on Computational Intelligence and Informatics, 2018, pp. 457-466: Springer.
A. Balaram and S. Pushpa, "Sybil attack resistant location privacy in VANET," International Journal of Information and Communication Technology, vol. 13, no. 4, pp. 389-406, 2018.
G. K. Rajbahadur, A. J. Malton, A. Walenstein, and A. E. Hassan, "A Survey of Anomaly Detection for Connected Vehicle Cybersecurity and Safety," in 2018 IEEE Intelligent Vehicles Symposium (IV), 2018, pp. 421-426: IEEE.
I. Bhardwaj and S. Khara, "An Analytic Study of Security Solutions for VANET," International Journal of Computer Applications, vol. 132, no. 10, pp. 1-7, 2015.
M. B. Shareh, H. Navidi, H. H. S. Javadi, and M. HosseinZadeh, "Preventing Sybil attacks in P2P file sharing networks based on the evolutionary game model," Information Sciences, vol. 470, pp. 94-108, 2019.
A. N. Upadhyaya and J. Shah, "Attacks on VANET Security," International Journal of Computer Engineering & Technology (IJCET), pp. 8-19.
M. Alimohammadi and A. A. Pouyan, "Sybil attack detection using a low cost short group signature in VANET," in Information Security and Cryptology (ISCISC), 2015 12th International Iranian Society of Cryptology Conference on, 2015, pp. 23-28: IEEE.
P. Rawat and S. Sharma, "Review on sybil attack in vehicular ad hoc network," International Journal of Science, Engineering and Technology Research (IJSETR) Volume, vol. 5.
S. Rakhi and K. Shobha, "Performance Analysis of an Efficient Data-Centric Misbehavior Detection Technique for Vehicular Networks," in International Conference on Computer Networks and Communication Technologies, 2019, pp. 321-331: Springer.
L. B. Imran, M. Farhan, R. M. A. Latif, and A. Rafiq, "Design of an IoT based warfare car robot using sensor network connectivity," in Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, 2018, pp. 1-8.
L. B. Imran, R. M. A. Latif, M. Farhan, and T. Tariq, "Real-time simulation of smart lighting system in smart city," International Journal of Space-Based and Situated Computing, vol. 9, no. 2, pp. 90-98, 2019.
R. M. A. Latif, M. Farhan, L. B. Imran, K. Manzoor, T. Tariq, and H. Raza, "Real-Time Simulation of IoT Based Smart Home System and Services Using RFID," KIET Journal of Computing and Information Sciences, vol. 2, no. 2, pp. 12-12, 2019.
S. M. Muzammal, R. K. Murugesan, and N. Jhanjhi, "A Comprehensive Review on Secure Routing in Internet of Things: Mitigation Methods and Trust-based Approaches," IEEE Internet of Things Journal, 2020.
R. M. Waseem, F. Z. Khan, M. Ahmad, A. Naseem, N. Jhanjhi, and U. Ghosh, "Performance Evaluation of AOMDV on Realistic and Efficient VANet Simulations," Wireless Personal Communications, pp. 1-20, 2021.
M. Saleh, N. Jhanjhi, A. Abdullah, and R. Saher, "Proposing Encryption Selection Model for IoT Devices Based on IoT Device Design," in 2021 23rd International Conference on Advanced Communication Technology (ICACT), 2021, pp. 210-219: IEEE.
R. Mishra, A. Singh, and R. Kumar, "VANET security: Issues, challenges and solutions," in Electrical, Electronics, and Optimization Techniques (ICEEOT), International Conference on, 2016, pp. 1050-1055: IEEE.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Muhammad Iqbal Younis, Rana M. Amir Latif, Izharul Haq, N. Z. Jhanjhi, Abdul Karim

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





