Efficient Intrusion Detection Using Deep Learning Approaches
Keywords:
Intrusion Detection, Deep Learning, Accuracy, Network Attacks, AccuracyAbstract
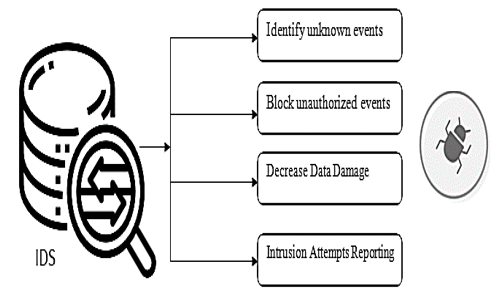
The main element in life is privacy, even in usual day-to-day life or in the world of the cloud. The major idea which is beyond the IDS concepts in a system is to discontinue the unknown events occurring from the surrounding or between the systems. It is suggested that the IDS be sent at two focuses. As there is a firewall securing the host organization or the private organization, it is smarter to put the IDS behind the firewall. The IDS sent can work effectively and search for suspicious events inside the organization. The attacks come from outside the host organization, or from the web that is attempting to send information to the host system. This research work can help in constructing IDS, using deep learning methods such as XGBoost, and MLP that can watch out for the information entering an organization and all the while sort out the unauthorized events. Among the two methods, MLP produces a better result in terms of accuracy value of about 89.5% compared to XG Boost algorithm which is 88% respectively.
Downloads
References
Arnaldo Gouveia1 & Miguel Correia(2019),” Network Intrusion Detection with XGBoost”, IEEE Transaction August 2019.
T. Chandrakala, S. Nirmala Sugirtha Rajini, K. Dharmarajan & K. Selvam(2021), “Implementation Of Data Mining And Machine Learning In The Concept Of Cybersecurity To Overcome Cyber Attack", Turkish Journal of Computer and Mathematics Education Vol.12 No. 12, pp. 4561-4571.
Sukhpreet Singh Dhaliwal, Abdullah-Al Nahid & Robert Abbas(2018), “Effective Intrusion Detection System Using XGBoost”, Information MDPI, Vol. 9, pp. 1024.
K. Anuradha, S. Nirmala SugirthaRajini, T.Bhuvaneswari & Viji Vinod (2020), “TCP /SYN Flood of Denial of Service (DOS) Attack UsingSimulation “, Test Engineering & Management, January - February 2020 ISSN: 0193 - 4120 Page No. 14553 – 14558.
Parag Verma; Shayan Anwar, Shadab Khan & Sunil B Mane(2018), “Network Intrusion Detection Using Clustering and Gradient Boosting “, 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), pp. 1-7,
K. Anuradha & S. Nirmala Sugirtha Rajini(2020), Analysis of Machine Learning Algorithm in IoT Security Issues and Challenges", Jour of Adv Research in Dynamical & Control Systems Vol. 11, 09-Special Issue, pp. 1030-1034.
Hui Jiang, Zheng He, Gang Ye & Huyin Zhang(2020), “Network Intrusion Detection Based on PSO-Xgboost Model”, IEEE Access, pp. 58392 – 58401.
Madhuri R. Yadav & Prashant Kumbharkar(2014), “Intrusion Detection System with FGA and MLP Algorithm”, International Journal of Engineering Research & Technology (IJERT) Vol. 3, No. 2, pp. 2431-2435.
K.Pavani & A.Damodaram(2013), “ Intrusion Detection Using Mlp For Manets “, Third International Conference on Computational Intelligence and Information Technology (CIIT 2013). doi:10.1049/cp.2013.2626, pp. 440-444.
Mehdi Moradi & Mohammad Zulkernine, "A Neural Network-Based System for Intrusion Detection and Classification of Attacks", https://citeseerx.ist.psu.edu/, pp. 1-6.
De Almeida Florencio, F., Moreno Ordonez, E. D., Teixeira Macedo, H., Paiva De Britto Salgueiro, R. J., Barreto Do Nascimento, F., & Oliveira Santos, F. A. (2018) “Intrusion Detection via MLP Neural Network Using an Arduino Embedded System” VIII Brazilian Symposium on Computing Systems Engineering (SBESC), PP. 190-195.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





