Data Leakage Detection in Cloud Computing Environment Using Classification Based on Deep Learning Architectures
Keywords:
cybersecurity, data leakage detection, cloud computing, data classification, deep learningAbstract
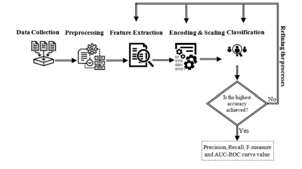
Insider threats are hostile actions that a legitimate employee of a company could commit. For both commercial and governmental enterprises, insider threats pose a significant cybersecurity risk since they have a considerably greater potential to harm an organization's assets than external attacks. The majority of currently utilised insider threat methodologies concentrated on identifying common insider attack scenarios. This research propose novel technique in data leakage detection in cloud computing based on data classification using deep learning architectures. Here the input data has been collected as network data and processed for noise removal, smoothening. The classification has been done based on Generative Regression kernel SVM. The experimental findings have been calculated in terms of RMSE, SNR, F-1 score, recall, accuracy, and precision. The proposed model offers practical approaches to deal with potential bias and class imbalance issues in order to design a system that effectively detects insider data leaking. Proposed technique attained accuracy of 97%, precision of 92%, recall of 67%, F-1 score of 66%, RMSE 62% and SNR of 61%.
Downloads
References
Okochi, P. I., Okolie, S. A., & Odii, J. N. (2021). An improved data leakage detection system in a cloud computing environment. World Journal of Advanced Research and Reviews, 11(2), 321-328.
Gupta, I., Mittal, S., Tiwari, A., Agarwal, P., & Singh, A. K. (2022). TIDF-DLPM: Term and Inverse Document Frequency based Data Leakage Prevention Model. arXiv preprint arXiv:2203.05367.
Gupta, I., & Singh, A. K. (2022). A Holistic View on Data Protection for Sharing, Communicating, and Computing Environments: Taxonomy and Future Directions. arXiv preprint arXiv:2202.11965.
Mayuranathan, M., Saravanan, S. K., Muthusenthil, B., & Samydurai, A. (2022). An efficient optimal security system for intrusion detection in cloud computing environment using hybrid deep learning technique. Advances in Engineering Software, 173, 103236.
Singh, P., & Ranga, V. (2021). Attack and intrusion detection in cloud computing using an ensemble learning approach. International Journal of Information Technology, 13(2), 565-571.
Gupta, R., Saxena, D., & Singh, A. K. (2021). Data security and privacy in cloud computing: concepts and emerging trends. arXiv preprint arXiv:2108.09508.
Chhabra, S., & Singh, A. K. (2022). A Comprehensive Vision on Cloud Computing Environment: Emerging Challenges and Future Research Directions. arXiv preprint arXiv:2207.07955.
Al-Shehari, T., & Alsowail, R. A. (2021). An insider data leakage detection using one-hot encoding, synthetic minority oversampling and machine learning techniques. Entropy, 23(10), 1258.
Alshammari, S. T., & Alsubhi, K. (2021). Building a reputation attack detector for effective trust evaluation in a cloud services environment. Applied Sciences, 11(18), 8496.
Chaudhary, H., Chaudhary, H., & Sharma, A. K. (2022). Optimized Genetic Algorithm and Extended Diffie Hellman as an Effectual Approach for DOS-Attack Detection in Cloud. International Journal of Software Engineering and Computer Systems, 8(1), 69-78.
Wang, X., Pan, Z., Zhang, J., & Huang, J. (2021). Detection and elimination of project engineering security risks from the perspective of cloud computing. International Journal of System Assurance Engineering and Management, 1-9.
Sharma, A., Singh, U. K., Upreti, K., & Yadav, D. S. (2021, October). An investigation of security risk & taxonomy of Cloud Computing environment. In 2021 2nd International Conference on Smart Electronics and Communication (ICOSEC) (pp. 1056-1063). IEEE.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Rajashekhargouda C. Patil, Ajay Kumar, Narmadha T., M. Suganthi, Akula VS Siva Rama Rao, Rajesh A.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





