Securing IoT system Access Control using Blockchain-Based Approach
Keywords:
IoT, cloud computing, blockchain, access controlAbstract
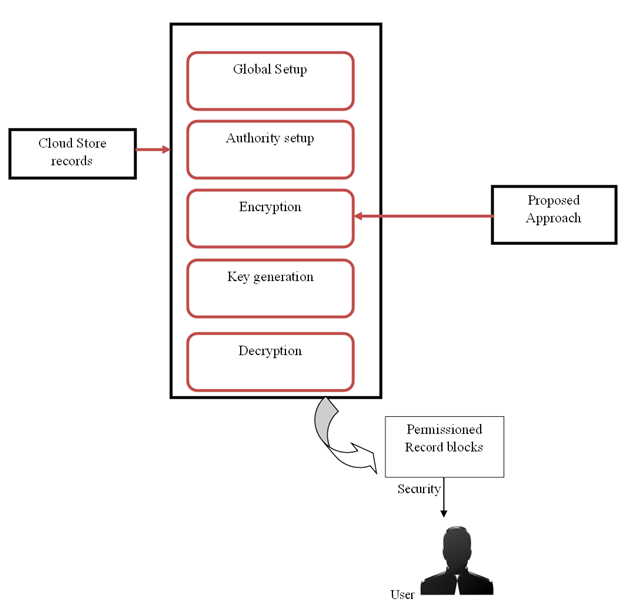
There are many reasons to be concerned about the safety and privacy of the Internet of Things (IoT), given its decentralised design and rapid growth. Controlling who can enter a building is a pressing concern. Centralized systems have low scalability and availability, which could cause a bottleneck in performance. This study introduces a novel approach to controlling the distribution of lightweight, decentralised, secure access management of an Internet of Things (IoT) system by combining a multi-agent system and a blockchain. To protect IoT access control and facilitate secure communication between local IoT devices, the proposed method proposes the development of Blockchain Managers (BCMs). In addition, the innovation enables safe connections between fog nodes, Internet of Things gadgets, and cloud servers.
Downloads
References
Zhao, Z., Zhou, H., Li, C., Tang, J., Zeng, Q. Deepemlan: deep embedding learning for attributed networks. Inf. Sci. 543, 382–397 (2021)
Pooranian Z, Shojafar M, Garg S, Taheri R, Tafazolli R (2021) LEVER: secure Deduplicated cloud storage with EncryptedTwo-party interactions in cyber-physical systems. IEEE Transact Industrial Informatics. https://doi.org/10.1109/TII.2020.3021013
Narendra, M. Research Reveals the Most Vulnerable IoT Devices. Available online: https://gdpr.report/news/2019/06/12 /research-reveals-themost-vulnerable-iot-devices/ (accessed on 11 January 2021).
NTT Innovation Institute. Mandatory Access Control over IoT Communications. Available online: https://labevent.ecl.ntt.co.jp/ forum2017/elements/pdf_eng/03/C-18_e.pdf (accessed on 16 November 2020).
Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in Internet of Things: Challenges and Solutions. Yingyong Kexue Xuebao/J. Appl. Sci. 2020, 38, 22–33. [CrossRef]
Saad M, et al. (2020) Exploring the Attack Surface of Blockchain: A Comprehensive Survey, IEEE Communications Surveys & Tutorials, 22(3):1977–2008
Chen, C.H., Lu, C.Y., Lin, C.B.: An intelligence approach for group stock portfolio optimization with a trading mechanism. Knowl. Inf. Syst. 62(1), 287–316 (2020)
Liu Y, Yu F, Li X, Ji H, Leung VM (2020) Blockchain and machine learning for Communications and networking systems. IEEE Commun Survey Tutorials 22(2):1392–1431. https://doi.org/10.1109/COMST.2020.2975911
Zhao, Z., Zhang, X., Zhou, H., Li, C., Gong, M., Wang, Y.: Hetnerec: Heterogeneous network embedding based recommendation. Knowl. Based Syst. 204, 106218 (2020)
Fu X, Yu FR, Wang J, Qi Q, Liao J (2019) Resource Allocation for Blockchain-Enabled Distributed Network Function Virtualization (NFV) with Mobile Edge Cloud (MEC), IEEE INFOCOM 2019. In: IEEE conference on computer Communications workshops (INFOCOM WKSHPS), Paris, France, pp 1–6
Belotti M, Bozic N, Pujolle G et al (2019) A Vademecum on Blockchain Technologies: When, Which and How. IEEE Commun Surveys Tutorials 21(4):3796–3838. https://doi.org/10.1109/COMST.2019.2928178
Ali M, Vecchio M, Pincheira M, Dolui K, Antonelli F, Rehman M (2019) Applications of Blockchains in the Internet of Things: A Comprehensive Survey. IEEE Commun Survey Tutorials 21(2):1676–1717
Ravidas, S.; Lekidis, A.; Paci, F.; Zannone, N. Access control in Internet-of-Things: A survey. J. Netw. Comput. Appl. 2019, 144, 79–101. [CrossRef]
Gao, W.; Hatcher, W.G.; Yu, W. A survey of blockchain: Techniques, applications, and challenges. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018. [CrossRef]
Aldowah, H.; Rehman, S.U.; Umar, I. Security in Internet of Things: Issues, Challenges and Solutions. In International Conference of Reliable Information and Communication Technology; Springer: Cham, Switzerland, 2018; pp. 396–405.
Ourad, A.Z.; Belgacem, B.; Salah, K. Using blockchain for IOT access control and authentication management. In International Conference on Internet of Things 2018 June; Springer: Cham, Switzerland, 2018; pp. 150–164.
Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a Novel Privacy-Preserving Access Control Model Based on Blockchain Technology in Iot. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Springer: Cham, Switzerland, 2017; pp. 523–533. [CrossRef]
Ouaddah, A.; Mousannif, H.; Elkalam, A.A.; Ouahman, A.A. Access control in the Internet of Things: Big challenges and new opportunities. Comput. Netw. 2017, 112, 237–262. [CrossRef]
Ahmed, E.; Yaqoob, I.; Hashem, I.A.T.; Khan, I.; Ahmed, A.I.A.; Imran, M.; Vasilakos, A.V. The role of big data analytics in Internet of Things. Comput. Netw. 2017, 129, 459–471. [Google Scholar] [CrossRef]
Kshetri, N. Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
Moin, S.; Karim, A.; Safdar, Z.; Safdar, K.; Ahmed, E.; Imran, M. Securing IoTs in distributed blockchain: Analysis, requirements and open issues. Future Gener. Comput. Syst. 2019, 100, 325–343. [Google Scholar] [CrossRef]
Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
Global, T.F. History of Blockchain. 2019. Available online: https://www.tradefinanceglobal.com/blockchain/history-of-blockchain/ (accessed on 22 November 2020).
Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–36. [Google Scholar]
The 5 Best Blockchain Platforms for Enterprises and What Makes Them A Good Fit. 2019. Available online: https://medium.com/swishlabs/the-5-best-blockchain-platforms-for-enterprises-and-what-makes-them-a-good-fit-1b44a9be59d4 (accessed on 7 September 2021).
Lu, Y. The blockchain: State-of-the-art and research challenges. J. Ind. Inf. Integr. 2019, 15, 80–90. [Google Scholar] [CrossRef]
Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





