Networks Cyber Security Model by Using Machine Learning Techniques
Keywords:
Cyber security, Network Monitoring, GMM, AI in cyber security, cyber-attackAbstract
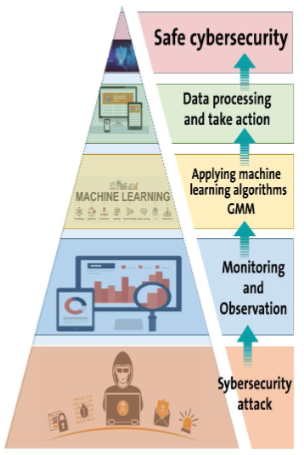
Since artificial intelligence relies on learning just like humans, it is useful to use these algorithms to address cyber-attacks, which represent the greatest concerns for network users, especially companies and institutions, as a result of the dire consequences of these attacks such as large material losses and the leakage or falsification of important data. The methods used to detect cyber-attacks are slow or they detect attacks after their occurrence and then analyze them and issue reports. In this research, we propose a conceptual framework that contains new rules that are used along with the previous rules for the purpose of creating a network monitoring tool in order to counteract cyber-attacks in real-time by relying on artificial intelligence algorithms such as classification and prediction based on user behavior. GMM algorithm has been suggested in this paper because of its efficiency in comparison with the commonly used algorithms in this sector like k-means it depends on behavioral similarities, not on distance.
Downloads
References
M. Harini and M. D. Reddy, “Optimal location and sizing of distributed generation units for maximum loss reduction using Teaching Learning Based Optimization through Matlab GUI,” Int. Conf. Electr. Electron. Signals, Commun. Optim. EESCO 2015, 2015, doi: 10.1109/EESCO.2015.7253906.
M. Qiu, K. Gai, B. Thuraisingham, L. Tao, and H. Zhao, “Proactive usercentric secure data scheme using attribute-based semantic access controls for mobile clouds in financial industry,” Futur. Gener. Comput. Syst., 2016.
W. Ahmad, J. Sunshine, C. Kastner, and A. Wynne, “Enforcing Fine-Grained Security and Privacy Policies in an Ecosystem within an Ecosystem,” 3rd Int. Work. Mob. Dev. Lifecycle, pp. 28 – 34, 2015.
T. M. Mbelli and B. Dwolatzky, “Cyber Security, a Threat to Cyber Banking in South Africa: An Approach to Network and Application Security,” Proc. - 3rd IEEE Int. Conf. Cyber Secur. Cloud Comput. CSCloud 2016 2nd IEEE Int. Conf. Scalable Smart Cloud, SSC 2016, pp. 1–6, 2016, doi: 10.1109/CSCloud.2016.18.
M. F. Alrifaie, Z. H. Ahmed, A. S. Hameed, and M. L. Mutar, “Using Machine Learning Technologies to Classify and Predict Heart Disease,” Int. J. Adv. Comput. Sci. Appl., vol. 12, no. 3, pp. 123–127, 2021, doi: 10.14569/IJACSA.2021.0120315.
M. F. Alrifaie, O. A. Ismael, A. S. Hameed and M. B. Mahmood, "Pedestrian and Objects Detection by Using Learning Complexity-Aware Cascades," 2021 2nd Information Technology To Enhance e-learning and Other Application (IT-ELA), 2021, pp. 12-17, doi: 10.1109/IT-ELA52201.2021.9773589.
B. S. Sagar, S. Niranjan, N. Kashyap, and D. N. Sachin, “Providing cyber security using artificial intelligence - A survey,” Proc. 3rd Int. Conf. Comput. Methodol. Commun. ICCMC 2019, no. Iccmc, pp. 717–720, 2019, doi: 10.1109/ICCMC.2019.8819719.
U. Adhikari, T. Morris, and S. Pan, “Wams cyber-physical test bed for power system, cybersecurity study, and data mining,” IEEE Trans. Smart Grid, vol. 8, no. 6, pp. 2744–2753, 2017.
M. Wu, Z. Song, and Y. B. Moon, “Detecting cyber-physical attacks in cybermanufacturing systems with machine learning methods,” J. Intell. Manuf., pp. 1–13, 2017.
K. V. K. V. Mohana and S. H.N., “Data Security using Genetic Algorithm and Artificial Neural Network,” Int. J. Sci. Eng. Res., vol. 5, no. 2, pp. 543–548, 2014.
R. Mittu and Willliam F. Lawless, “Human Factors in Cybersecurity and the Role for AI,” Found. Auton. Its Threat. From Individ. to Interdepend. Pap. from 2015 AAAI Spring Symp., pp. 39–43, 2015.
A. P. Veiga, “Application of Artificial Intelligence (AI) to Network Security,” ITEC 625 – Inf. Syst. Infrastruct., 2018.
T. Enn, “Conflict, Artificial Intelligence in Cyber Defense,” 2011 3rd Int. Conf. Cyber, 2011.
S. Xiaokui, Y. Danfeng, and R. Naren, “Unearthing Stealthy Program Attacks Buried in Extremely Long Execution Paths,” Proc. 22nd ACM SIGSAC Conf. Comput. Commun. Secur., 2015.
J. Yu, Q. Wan, Q. Liu, X. Chen, and Z. Li, A novel ship detector based on gaussian mixture model and K-means algorithm, vol. 842. Springer International Publishing, 2019. doi: 10.1007/978-3-319-98776-7_72.
C. Chen, “A performance evaluation of machine learning-based streaming spam tweets detection,” IEEE Trans. Comput. Soc. Syst., vol. 2, no. 3, pp. 65–76, 2015.
J. Zhang, Y. Xiang, Y. Wang, W. Zhou, Y. Xiang, and Y. Guan, “Network traffic classification using correlation information,” IEEE Trans. Parallel Distrib. Syst., vol. 20, no. 1, pp. 104–117, 2013.
S. Laazizi, J. Ben Azzouz and A. Jemai, "cybclass: classification approach for cybersecurity in industry 4.0," 2022 IEEE 9th International Conference on Sciences of Electronics, Technologies of Information and Telecommunications (SETIT), 2022, pp. 378-384, doi: 10.1109/SETIT54465.2022.9875643.
J. C. Acosta, S. Medina, J. Ellis, L. Clarke, V. Rivas and A. Newcomb, "Network Data Curation Toolkit: Cybersecurity Data Collection, Aided-Labeling, and Rule Generation," MILCOM 2021 - 2021 IEEE Military Communications Conference (MILCOM), 2021, pp. 849-854, doi: 10.1109/MILCOM52596.2021.9653049.
C. Latinopoulos, N. Daina and J. W. Polak, "Trust in IoT-enabled mobility services: Predictive analytics and the impact of prediction errors on the quality of service in bike sharing," Living in the Internet of Things: Cybersecurity of the IoT - 2018, 2018, pp. 1-7, doi: 10.1049/cp.2018.0044.
B. Bokan and J. Santos, "Managing Cybersecurity Risk Using Threat Based Methodology for Evaluation of Cybersecurity Architectures," 2021 Systems and Information Engineering Design Symposium (SIEDS), 2021, pp. 1-6, doi: 10.1109/SIEDS52267.2021.9483736.
Xiaokui Shu, Danfeng Yao, and Naren Ramakrishnan. “Unearthing Stealthy Program Attacks Buried in Extremely Long Execution Paths.” Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, 2015.
Y. Rong and Y. Liu, "Staged text clustering algorithm based on K-means and hierarchical agglomeration clustering," 2020 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), 2020, pp. 124-127, doi: 10.1109/ICAICA50127.2020.9182394.
A. Nugraha, M. Arista Harum Perdana, H. Agus Santoso, J. Zeniarja, A. Luthfiarta and A. Pertiwi, "Determining The Senior High School Major Using Agglomerative Hierarchial Clustering Algorithm," 2018 International Seminar on Application for Technology of Information and Communication, 2018, pp. 225-228, doi: 10.1109/ISEMANTIC.2018.8549834.
S. H. Shihab, S. Afroge and S. Z. Mishu, "RFM Based Market Segmentation Approach Using Advanced K-means and Agglomerative Clustering: A Comparative Study," 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), 2019, pp. 1-4, doi: 10.1109/ECACE.2019.8679376.
Y. Zhou, A. Rangarajan and P. D. Gader, "A Gaussian mixture model representation of endmember variability for spectral unmixing," 2016 8th Workshop on Hyperspectral Image and Signal Processing: Evolution in Remote Sensing (WHISPERS), 2016, pp. 1-5, doi: 10.1109/WHISPERS.2016.8071802.
Z. Lei, H. Yan, C. Liu, M. Ma and Y. Yang, "Two-Path GMM-ResNet and GMM-SENet for ASV Spoofing Detection," ICASSP 2022 - 2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2022, pp. 6377-6381, doi: 10.1109/ICASSP43922.2022.9746163.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Farah Abbas Obaid Sari, Ali Abdulkarem Habib Alrammahi, Asaad Shakir Hameed, Haiffa Muhsan B. Alrikabi, Abeer A. Abdul–Razaq, Huda Karem Nasser, Mohammed F. AL-Rifaie

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





