Implementation Patterns of Natural Language Processing Using Pre-Trained Deep Learning Models
Keywords:
Deep Learning, Pre-Trained Deep Learning Models, Natural Language ProcessingAbstract
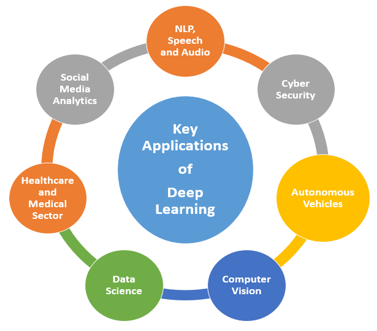
When it comes to computer programming, Natural Language Processing (NLP) is all about creating computers that can read and respond to information in the same way that humans do, and then generate their text or speech in response. "Natural language processing" is an area of artificial intelligence (AI) that aims to give computers the ability to understand written and spoken language in the same way humans do (NLP). Using a combination of computational linguistics and statistics, machine learning, and deep learning models, NLP uses a set of programmable rules to describe human language. When text and voice data are combined, computers may 'understand' human language, including the speaker's or writer's intent and emotion, in the form of text or audio data. To put it another way, NLP is the driving force behind computer systems that translate text across languages, respond to spoken commands, and summaries massive volumes of information quickly—even in real-time. When it comes to voice-activated GPS, digital assistants, speech-to-text software, and customer support chatbots, you've utilized NLP as a consumer. Improved operational efficiency, increased employee productivity, and simplified mission-critical business operations are all benefits of using NLP in corporate solutions. Assorted deep learning systems for NLP analytics and research aspects are presented in the manuscript.
Downloads
References
I. Lauriola, A. Lavelli, and F. Aiolli, "An introduction to deep learning in natural language processing: Models, techniques, and tools," Neurocomputing, vol. 470, pp. 443-456, 2022.
R. Haque, N. Islam, M. Islam, and M. M. Ahsan, "A comparative analysis on suicidal ideation detection using NLP, machine, and deep learning," Technologies, vol. 10, no. 3, p. 57, 2022.
S. S. Sundaram, S. Gurajada, M. Fisichella, and S. S. Abraham, "Why are NLP Models Fumbling at Elementary Math? A Survey of Deep Learning based Word Problem Solvers," arXiv preprint arXiv:.15683, 2022.
R. A. Azeez, M. K. Abdul-Hussein, M. S. Mahdi, "Design a system for an approved video copyright over cloud based on biometric iris and random walk generator using watermark technique," Periodicals of Engineering Natural Sciences, vol. 10, no. 1, pp. 178-187, 2022.
T. H. Jasim, S. A. Abed, and A. Ghazi, "Concepts Of Bi-supra Topological Space Via graph Theory," Wasit Journal of Computer and Mathematics Sciences, vol. 1, no. 2, 2022.
K. H. K. Al-Saedi, "Implementation Patterns of AquaSim for Simulation of Underwater Acoustic Wireless Sensor Networks," Wasit Journal of Computer and Mathematics Science, pp. 84-92, 2021.
K. Koskenniemi, Two-level morphology: A general computational model for word-form recognition and production. University of Helsinki, Department of General Linguistics Helsinki, Finland, 1983.
A. K. Joshi and S. Weinstein, "Control of Inference: Role of Some Aspects of Discourse Structure-Centering," in IJCAI, 1981, pp. 385-387.
R. a. M. A. a. Abdul Hadi M. Alaidi, Haider TH. Salim ALRikabi, Ibtisam A. Aljazaery, Saif Hameed Abbood, "Dark web illegal activities crawling and classifying using data mining techniques," International Journal of Interactive Mobile Technologies (iJIM), vol. 16, no. 10, 2022.
A. S. Mohamad, "Machine Learning Empowered Software Prediction System," Wasit Journal of Computer and Mathematics Sciences, vol. 1, no. 3, pp. 52-61, 2022.
Y. S. Mezaal, D. A. Hammood, and M. H. Ali, "OTP encryption enhancement based on logical operations," in 2016 Sixth International Conference on Digital Information Processing and Communications (ICDIPC), 2016: IEEE, pp. 109-112.
I. A. Aljazaery, and A. H. M. Alaidi, "Encryption of Color Image Based on DNA Strand and Exponential Factor," International Journal of Online Biomedical Engineering, vol. 18, no. 3, pp. 101-113, 2022.
S. A. Diwan, S. Perumal, and A. J. Fatah, "Complete security package for USB thumb drive," Computer Engineering and Intelligent System, 2014.
H. T. ALRikabi and H. T. Hazim, "Enhanced Data Security of Communication System Using Combined Encryption and Steganography," International Journal of Interactive Mobile Technologies, vol. 15, no. 16, 2021.
J. Kh-Madhloom, "Dynamic Cryptography Integrated Secured Decentralized Applications with Blockchain Programming," Wasit Journal of Computer and Mathematics Sciences, vol. 1, no. 2, pp. 21-33, 2022.
G. Guida and G. Mauri, "Evaluation of natural language processing systems: Issues and approaches," Proceedings of the IEEE, vol. 74, no. 7, pp. 1026-1035, 1986.
H. Al-ogaili and A. M. Shadhar, "the Finger Vein Recognition Using Deep Learning Technique," Wasit Journal of Computer and Mathematics Sciences, vol. 1, no. 2, pp. 1-11, 2022.
H. Salim, J. S. Qateef, A. M. Alaidi, and R. M. Al_airaji, "Face Patterns Analysis and recognition System based on Quantum Neural Network QNN," International Journal of Interactive Mobile Technologies (iJIM), vol. 16, no. 9, 2022.
S. Khairy, and H. Salim, "The Detection of Counterfeit Banknotes Using Ensemble Learning Techniques of AdaBoost and Voting," International Journal of Intelligent Engineering and Systems, vol. 14, no. 1, pp. 326-339, 2021.
H. Tauma. and H. ALRikabi, "Secure Chaos of 5G Wireless Communication System Based on IOT Applications," International Journal of Online and Biomedical Engineering(iJOE), vol. 18, no. 12, pp. 89-102, 2022.
M. H. Abd, "Dynamic Data Replication for Higher Availability and Security," Wasit Journal of Computer and Mathematics Science, pp. 31-42, 2021.
Y. Goldberg, "A primer on neural network models for natural language processing. ArXiv," arXiv preprint arXiv:.00726, 2015.
I. Goodfellow, Y. Bengio, and A. Courville, Deep learning. MIT press, 2016.
R. Jozefowicz, O. Vinyals, M. Schuster, N. Shazeer, and Y. Wu, "Exploring the limits of language modeling," arXiv preprint arXiv:.02410, 2016.
H. Verma, "Internet of Robotics Things (IoRT) Based Integration of Robotic Applications for Advanced Research," Wasit Journal of Computer and Mathematics Science, pp. 9-16, 2021.
E. Charniak, "Parsing as language modeling," in Proceedings of the 2016 Conference on Empirical Methods in Natural Language Processing, 2016, pp. 2331-2336.
O. Vinyals, Ł. Kaiser, T. Koo, S. Petrov, I. Sutskever, and G. Hinton, "Grammar as a foreign language," Advances in neural information processing systems, vol. 28, 2015.
A. Turchin and L. F. Florez Builes, "Using natural language processing to measure and improve quality of diabetes care: a systematic review," Journal of Diabetes Science Technology, vol. 15, no. 3, pp. 553-560, 2021.
T. Winograd, "Procedures as a representation for data in a computer program for understanding natural language," MASSACHUSETTS INST OF TECH CAMBRIDGE PROJECT MAC, 1971.
R. C. Schank and R. P. Abelson, Scripts, plans, goals, and understanding: An inquiry into human knowledge structures. Psychology Press, 2013.
M. Johnson, "How the statistical revolution changes (computational) linguistics," in Proceedings of the EACL 2009 Workshop on the Interaction between Linguistics and Computational Linguistics: Virtuous, Vicious or Vacuous?, 2009, pp. 3-11.
P. Resnik, "Four revolutions," Language Log, February, vol. 5, 2011.
M. Trabelsi, P. Kakosimos, and H. Komurcugil, "Mitigation of grid voltage disturbances using quasi-Z-source based dynamic voltage restorer," in 2018 IEEE 12th International Conference on Compatibility, Power Electronics and Power Engineering (CPE-POWERENG 2018), 2018: IEEE, pp. 1-6.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





