Detection and Verification of Cloned Profiles in Online Social Networks Using MapReduce Based Clustering and Classification
Keywords:
Cloned profile detection, identity cloning attack, online social networks, parallel k-means, parallel SVM, mapreduceAbstract
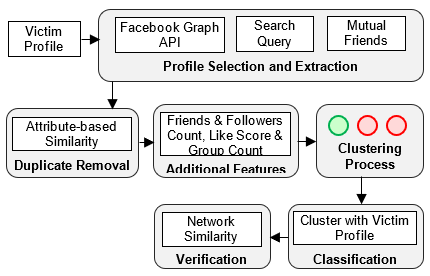
The use of online social networks has become an unavoidable part of today's humans’ life. The augmented usage of these online social networks has also increased the misusage through spreading spam messages, false reviews and fake news. Fake accounts are one such method in which attackers clone the profiles of innocent victims to harm them and damage their reputations. In some situations, fake accounts are also created to steal money from other users. In recent days, the detection of such cloned or fake profiles has perceived a wide range of attention from researchers. However, the existing methods lack accuracy and precision in detecting cloned profiles. In this paper, an effort has been made to identify the cloned profiles using clustering and classification process. The method collects the fake and possible cloned profiles and computes the additional relationship attributes for performing cloned profile detection. The parallel k-means clustering is carried out to group the suspicious profiles that are similar to the real ones. Then the parallel SVM classification is applied to the cluster in which the real profile is grouped. Finally, the classification results are verified using the attribute and network similarity measure. The various stages of the proposed model are implemented using the MapReduce framework which is more suitable for big data. The experimental analysis and results indicate that the proposed model has better performance than other competitors with an accuracy and precision of 98.19% and 98.96% for the MIB twitter dataset and 98.90% and 99.17% for the synthetic dataset created for the study.
Downloads
References
C. C. Yang, S. M. Holden, M. D. Carter, and J. J. Webb, “Social media social comparison and identity distress at the college transition: A dual-path model,” Journal of Adolescence, vol. 69, pp. 92-102, 2018.
A. K. Jain, S. R. Sahoo, and J. Kaubiyal, “Online social networks security and privacy: comprehensive review and analysis,” Complex & Intelligent Systems, vol. 7, no. 5, pp. 2157-2177, 2021.
T.R. Soomro, and M.Hussain, “Social Media-Related Cybercrimes and Techniques for Their Prevention,” Appl. Comput. Syst, vol. 24, pp.9-17, 2019.
J.Johnson, “Global digital population”, https://www.statista.com/statistics/617136/digitalpopulation-worldwide. Jan 27 2021.
A. Homsi, J. Al Nemri, N. Naimat, , H.A. Kareem, M. Al-Fayoumi, and M.A. Snober, “Detecting Twitter Fake Accounts using Machine Learning and Data Reduction Techniques”, In DATA, pp. 88-95, 2021.
J. Heidemann, M. Klier, and F. Probst, “Online social networks: A survey of a global phenomenon”, Computer networks, vol.56, no.18, pp. 3866-3878, 2012.
K .Kaur, and P.Kumar, “Social media: a blessing or a curse? Voice of owners in the beauty and wellness industry”, The TQM Journal, 2021.
P. Patel, K. Kannoorpatti, B. Shanmugam, S. Azam, and K.C. Yeo, “A theoretical review of social media usage by cyber-criminals”, in 2017 International Conference on Computer Communication and Informatics (ICCCI), IEEE, pp. 1-6, 2017.
S. Maniraj, P. Harie Krishnan, G. T. Surya, and R. Pranav, “Fake Account Detection using Machine Learning and Data Science”, International Journal of Innovative Technology and Exploring Engineering (IJITEE), vol. 9, no. 1, 2019.
M. Zabielski, Z. Tarapata, R. Kasprzyk, and K. Szkółka, "Profile cloning detection in online social networks," Computer Science and Mathematical Modelling, 2016.
L. Bilge, T. Strufe, D. Balzarotti, and E. Kirda, “All your contacts are belong to us: automated identity theft attacks on social networks," in Proceedings of the 18th international conference on World wide web, ACM, pp. 551–560, 2009.
L. Jin, H. Takabi, J.B. Joshi, “Towards active detection of identity clone attacks on online social networks”, in Proceedings of the first ACM conference on Data and application security and privacy, pp. 27-38, February 2011.
M. Conti, R. Poovendran, and M. Secchiero, “Fakebook: Detecting fake profiles in on-line social networks”, presented in IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, pp. 1071-1078 , August 2012.
S. Gurajala, J.S. White, B. Hudson, B.R. Voter, and J.N. Matthews, “Profile characteristics of fake Twitter accounts”, Big Data and Society, vol. 3, pp. 2053951716674236, 2016.
P. Sowmya and Chatterjee, “Detection of Fake and Cloned Profiles in Online Social Networks”, Proceedings 2019: Conference on Technologies for Future Cities (CTFC), March 2019.
S.S Bama, and A. Saravanan, “Efficient classification using average weighted pattern score with attribute rank-based feature selection”, International Journal of Intelligent Systems and Applications, vol. 11, no. 7, pp .29, 2019.
A. Saravanan, S. S. Bama, S. Kadry, and L.K.Ramasamy, “A new framework to alleviate DDoS vulnerabilities in cloud computing”, International Journal of Electrical & Computer Engineering, vol. 9, no. 5, 2019.
S. Sathya Bama, M.I. Ahmed, and A. Saravanan, “A Mathematical Approach for Filtering Junk E-Mail Using Relevance Analysis”, Asia Pacific Journal of Research, vol. 1, no. 35, 2016.
A. Rauf, S. Khusro, S. Mahfooz, and R. Ahmad, ”A Robust System Detector for Clone Attacks on Facebook Platform”, Journal of Research, vol.13, no.4, pp. 71-80, 2016.
P. Bródka, M. Sobas, and H. Johnson, “Profile cloning detection in social networks”, in 2014 European Network Intelligence Conference, pp. 63-68, September 2014.
N. Kumar, and P. Dabas, “Detection and Prevention of Profile Cloning in Online Social Networks”, in 2019 5th International Conference on Signal Processing, Computing and Control (ISPCC), pp. 287-291, October 2019.
G. Kontaxis, I. Polakis, S. Ioannidis, and E.P. Markatos, “Detecting social network profile cloning”, in 2011 IEEE international conference on pervasive computing and communications workshops (PERCOM Workshops), pp. 295-300, March 2011.
A.N. Hakimi, S. Ramli, , M. Wook, N. Mohd Zainudin, N.A. Hasbullah, N. Abdul Wahab, and N.A. Mat Razali, “ Identifying Fake Account in Facebook Using Machine Learning”, in International Visual Informatics Conference”, pp. 441-450, Springer, Cham, November,2019.
S.R. Sahoo, B.B Gupta,” Fake profile detection in multimedia big data on online social networks”, International Journal of Information and Computer Security, vol. 12, no. 2-3, pp.303-331.
Y. Elyusufi, Z. Elyusufi, and M.H.A Kbir, “Social networks fake profiles detection based on account setting and activity”, in Proceedings of the 4th International Conference on Smart City Applications, pp. 1-5, October,2019.
S. Kiruthiga, and A. Kannan, “Detecting cloning attack in Social Networks using classification and clustering techniques”, in 2014 International Conference on Recent Trends in Information Technology, pp. 1-6, April 2014.
S. Ranjana, R. Sathian, and M.D. Kamalesh, “ Fake Profile Detection in Facebook”, In International Conference on Emerging Trends and Advances in Electrical Engineering and Renewable Energy, pp. 725-732, Springer, Singapore, 2020, March.
C.R Liyanage, and S.C. Premarathne, “Clustered Approach for Clone Detection in social media”, International Journal of Advanced Science Engineering Information technology, vol. 11, no. 1, pp. 99-104, 2021.
S.S. Bama, M.I. Ahmed, and A. Saravanan, “A mathematical approach for mining web content outliers using term frequency ranking”, Indian Journal of Science and Technology, vol. 8, no. 14, pp.1-5, 2015.
A. ElAzab,“Fake accounts detection in twitter based on minimum weighted feature. World Academy of Science, Engineering and Technology”, International Journal of Computer, Electrical, Automation, Control and Information Engineering, vol. 10, no. 1, pp. 13-18, 2016.
M.Y. Kharaji, and F.S. Rizi, “An iac approach for detecting profile cloning in online social networks”, International Journal of Network Security & Its Applications, vol. 6, no.1, pp. 75-90, 2014.
M.B. Albayati, and A.M. Altamimi, “An empirical study for detecting fake Facebook profiles using supervised mining techniques”, Informatica, vol. 43, no. 1, pp. 77–86.03, 2019.
M.B. Albayati, and A.M. Altamimi, “Identifying Fake Facebook Profiles Using Data Mining Techniques”, Journal of ICT Research & Applications, vol. 13, no. 2, pp. 107-117, 2019.
Singh, and Banerjee, “Fake (Sybil) Account Detection Using Machine Learning”, Proceedings of International Conference on Advancements in Computing & Management (ICACM), Available at SSRN:https://ssrn.com/abstract=3462933 or http://dx.doi.org/10.2139/ssrn.3462933, October 2, 2019.
F. Ajesh, S.U. Aswathy, F.M. Philip, and V. Jeyakrishnan , “A hybrid method for fake profile detection in social network using artificial intelligence”, Security Issues and Privacy Concerns in Industry 4.0 Applications, pp.89-112, 2021.
M. Zare, S.H. Khasteh, and S. Ghafouri, “Automatic ICA detection in online social networks with PageRank”, Peer-to-Peer Networking and Applications, vol. 13 no.5, 1297-1311, 2020.
M. Suriakala, and S. Revathi, “Privacy protected system for vulnerable users and cloning profile detection using data mining approaches”, in 2018 Tenth International Conference on Advanced Computing (ICoAC), pp. 124-132, December, 2018.
A. Zaman, M.A. Siddique, and Y. Morimoto, “Finding key persons on social media by using MapReduce skyline”, International Journal of Networking and Computing, vol.7, no.1, pp.86-104, 2017.
W. Zhao, H. Ma, and Q. He, “Parallel k-means clustering based on mapreduce”, In IEEE international conference on cloud computing, pp. 674-679, Springer, Berlin, Heidelberg, 2009 December.
X. Hou, “An improved k-means clustering algorithm based on hadoop platform”, In The International Conference on Cyber Security Intelligence and Analytics, pp. 1101-1109, Springer, Cham, 2019, February.
F.O. Çatak, and M.E. Balaban, “A MapReduce-based distributed SVM algorithm for binary classification”, Turkish Journal of Electrical Engineering and Computer Sciences, vol. 24, no. 3, pp. 863-873, 2020.
MySafeFriend: http://apps.facebook.com/mysafefriend. Accessed: 2012- 01-10.
J. Weaver, P. Tarjan, “Facebook linked data via the graph API. Semantic Web”, vol. 4, no. 3, pp. 245-250, 2013.
S. Cresci, R. Di Pietro, M. Petrocchi, A. Spognardi, and M. Tesconi, “Fame for sale: Efficient detection of fake Twitter followers”, Decision Support Systems, vol. 80, pp. 56-71, 2015.
S. Cresci, R. Di Pietro, M. Petrocchi, A. Spognardi, and M. Tesconi, "A Fake Follower Story: improving fake accounts detection on Twitter," 2014.
G. Stringhini, C. Kruegel, and G. Vigna, “Detecting spammers on social networks”, in Proceedings of the 26th annual computer security applications conference, pp. 1-9, December 2010.
F. Ahmed, and M. Abulaish, “A generic statistical approach for spam detection in online social networks”, Computer Communications, vol. 36, no. 10-11, pp. 1120-1129, 2013.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





