Neural Network Optimization-Based Facial Geometric Key Homomorphic Cloud Security
Keywords:
Encryption, Facial Features, Algorithm, RecognitionAbstract
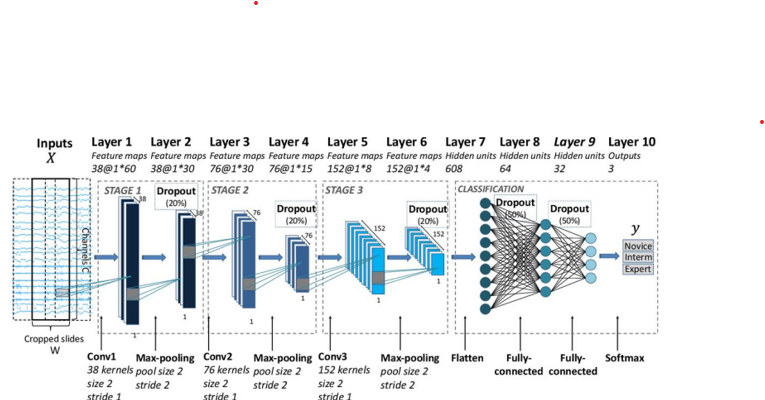
In the modern day, cloud computing has become an essential component of technological and individual interactions with computing devices. The majority of cloud platforms use conventional encryption techniques for device authentication, whereas the cloud services that are still useful offer consumers older protocol for device authentication. The face authentication protocol described in this work will provide a facial geometric point that will serve as the encryption key. The method was created as a multi-stage implementation of the interdependent facial recognition algorithms. The fuzzy neural inference algorithm, which forms the basis of the first sequence of the algorithm, is used to implement face verification of users and the input of each person into a tracking sheet. The second method involved facial geometric point mapping of a face for the recognition of deep facial features using a convolution neural network (CNN) using a VGG19-based architecture. A facial geometric point-based facial network was created based on the algorithm, and each unique face was given a label. The process added the ability to recognize numerous faces in a single image. The third approach makes use of a cloud authentication system that is based on face geometric point identification. Based on facial geometry points that will be used as input for the encryption cypher, this method generates a dynamic encryption key. In order to encrypt the file, these facial geometric points, which are calculated based on the number of regions that were detected on a particular face, are given a dynamically assigned value and input to the key of the specific algorithm. These geometric points will also be used to decrypt the file.
Downloads
References
Nitin Chauhan; Laxmi Ahuja; Sunil Kumar Khatri2018 International Conference.“Secure Data in Cloud Computing Using Face Detection and Fingerprint”.
IEEE Symposium “Cloud-Vision: Real-time face recognition using a mobile-cloudlet-cloud acceleration architecture”Tolga Soyata; Rajani Muraleedharan; Colin Funai; Minseok Kwon; Wendi Heinzelman
“Cloud Based Big Data Analytics Framework for Face Recognition in Social Networks Using MachineLearning“2015Procedia Computer ScienceA.VinayaVinay S.Shekhara J.Rituparnab TusharAggrawalb K.N. Balasubramanya Murthya S.Natarajanb
“Cloud-Vision: Real-time face recognition using a mobile-cloudlet-cloud acceleration architecture” 2012 8 IEEE SymposiumTolga Soyata; Rajani Muraleedharan; Colin Funai; Minseok Kwon; Wendi HeinzelmaN
Li, C., Wei, W., Li, J. et al. A cloud-based monitoring system via face recognition using Gabor and CS-LBP features. J Supercomput73, 1532–1546 (2017). https://doi.org/10.1007/s11227-016-1840-6
“Privacy Preserving Face Identification in the Cloud through Sparse Representation” Xin Jin Yan Liu, Xiaodong Li, Geng Zhao, Yingya Chen, Kui Guo October 2015
“Privacy preserving security using biometrics in cloud computing” Authors: Santosh Kumar,Sanjay Kumar Singh,Amit Kumar Singh, Shrikant Tiwari, Ravi Shankar Singh Multimedia Tools and Applications Volume 77Issue 9May 2018.
“Cloud-Based Face and Speech Recognition for Access Control Applications”Nathalie Tkauc; Thao Tran; Kevin HernandezDiaz; Fernando Alonso-FernandezIEEE Conference on Communications and Network Security (CNS)
“Multiple face recognition in real-time using cloud computing, Emgu CV and Windows Azure”Diego von Söhsten; Sérgio MuriloInternational Conference on Intelligent Systems Design and Applications (ISDA)
Zhou, S., Xiao, S. 3D face recognition: a survey. Hum. Cent. Comput. Inf. Sci.8, 35 (2018). https://doi.org/10.1186/s13673- 018-0157-2
Wang, W., Lin, H. & Wang, J. CNN based lane detection with instance segmentation in edge-cloud computing. J Cloud Comp9, 27 (2020). https://doi.org/10.1186/s13677-020-00172-z
Liu, J., Wu, J., Sun, L. et al. Image data model optimization method based on cloud computing. J Cloud Comp9, 31 (2020). https://doi.org/10.1186/s13677-020-00178-7
Yin, Y., Lin, J., Sun, N. et al. Method for detection of unsafe actions in power field based on edge computing architecture. J Cloud Comp10, 17 (2021). https://doi.org/10.1186/s13677-021-00234-w
Padilla, R.S., Milton, S.K. & Johnson, L.W. Components of service value in business-to-business Cloud Computing. J Cloud Comp4, 15 (2015). https://doi.org/10.1186/s13677-015-0040-x
Xu, Z., Zhang, Y., Li, H. et al. Dynamic resource provisioning for cyber-physical systems in cloud-fog-edge computing. J Cloud Comp9, 32 (2020). https://doi.org/10.1186/s13677-020-00181-y
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





