Comparison of Performance of Boneh-Shaw Finger Printing Codes with Tardos Under Randomized Bits Collusion Attacks
Keywords:
Boneh-Shaw fingerprinting codes, Tardos-Codes, Randomised Bits Collusion Attacks, Piracy ProtectionAbstract
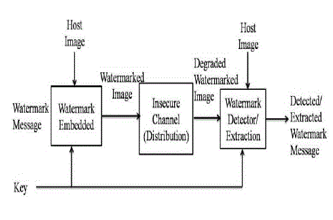
Fingerprinting codes are needed for the protection of copyright issues of digital media. Before distributing digital media these codes are embedded in it. These codes are unique for each digital media. When illegal copies of these digital media are made they are identified by unique fingerprinting code inserted in them. In this way, culprits making illegal copies are identified. But these fingerprinting codes are subject to collusion attacks. In Collusion attacks, culprit users conspire together to instigate attacks against fingerprint codes. The culprit users cartelise and does the modification in the fingerprinting code of the digital media . The fingerprinting codes are changed in such a way so that an innocent user is found the culprit. Thus, these attacks are bottlenecks in protecting the digital rights of digital media. This research compares results of Boneh-Shaw fingerprinting codes with tardos code while launching Randomized bits Collusion attacks on both the codes.
Downloads
References
Dan Boneh and James Shaw .Collusion-Secure ingerprinting for Digital Data. IEEE Transactions on Information Theory, Vol. 44, N0. 5, September 1998.
G.Tardos(2003) ,Optimal Probablistic Fingerprint Codes,Proceedings of the 35th Annual ACM Symposium on Theory of Computing 2003
Tripathi Alok,Pandey Rajiv , Analysis of Boneh-Shaw Finger Printing Codes under Majority Value Collusion Attacks International Journal of Computer Applications (0975 – 8887) Volume 167 – No.3, June 2017.
Analysis of Boneh - Shaw Finger Printing Codes under randomized bits collusion attack. International Journals of Computer Science and Information Security Pittsburgh. PA-USA (ISSN1947500) May 2017 Edition.
Analysis of Boneh - Shaw Finger Printing Codes under majority value collusion attack. International Journals of Computer Applications IJCA June 2017 Edition, Foundation of Computer Science New York USA. ISSN-0975-8887.
Evaluating Performance of Boneh-Shaw Finger Printing Codes under Minority Value Collusion Attacks. The 12th International Conference on Computational Intelligence and Communication Networks (CICN 2020)- IEEE-Conference Bhimtal-25-26 Sep 2020.
Simulating Tardos Finger Printing Codes under Randomized Bits Collusion Attacks. ICCCIS-2021, International Conference on Computing,Communication, and Intelligent Systems 19th-20th February, 2021 Greater Noida, India
Alaria, S. K. "A.. Raj, V. Sharma, and V. Kumar.“Simulation and Analysis of Hand Gesture Recognition for Indian Sign Language Using CNN”." International Journal on Recent and Innovation Trends in Computing and Communication 10, no. 4 (2022): 10-14.
S. K. A. “An Improved Algorithm for Faster Multi Keyword Search in Structured Organization”, International Journal on Future Revolution in Computer Science & Communication Engineering Vol-5, issue- 5 (2019), 19–23.
S. K. A. “Improving the Performance of Heterogeneous Hadoop Clusters Using Map Reduce”. IJRITCC 2019, 7, 11-17.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Alok Tripathi, Rajiv Pandey, Amarjeet Singh

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





