Deep Learning Perspectives to Detecting Intrusions in Wireless Sensor Networks
Keywords:
Deep learning, Anomaly detection, CNN, CNN-LSTM, GRU, RNN, LSTMAbstract
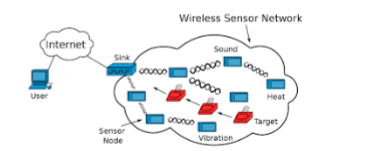
Due to the increasing number of communication protocols being used to send and receive data, security concerns have been raised about the unauthorized access of this data. To address these issues, the development of advanced IDS has been carried out. Deep learning is a type of machine learning that is composed of several neurons. Due to the increasing number of large-scale data sets and the success of deep learning in various fields, researchers have focused on detecting intrusions using deep learning. Due to the increasing number of data transmissions through various communication protocols, there has been a rise in security concerns about the security of these networks. This has prompted researchers to develop advanced IDSs that can detect unauthorized access. Besides having an effective network intrusion detection system(NIDS), continuous improvement is also required to ensure that the security of the network is maintained. Deep learning techniques are commonly used in the detection of network intrusions. It can also perform various tasks, such as analyzing and reporting on data. Due to its success in various fields, researchers have been focusing on developing deep learning techniques for detecting intrusions. This paper aims to review the current state of deep learning-based IDSs and compare with proposed modified algorithms with the previous ones.
Downloads
References
A. Thakkar and R. Lohiya, A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges, vol. 28, no. 4. Springer Netherlands, 2021.
R. Ganeshan, C. S. Kolli, C. M. Kumar, and T. Daniya, “A Systematic Review on Anomaly Based Intrusion Detection System,” IOP Conf. Ser. Mater. Sci. Eng., vol. 981, no. 2, 2020, doi: 10.1088/1757-899X/981/2/022010.
A. Aldweesh, A. Derhab, and A. Z. Emam, “Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues,” Knowledge-Based Syst., vol. 189, p. 105124, 2020, doi: 10.1016/j.knosys.2019.105124.
Z. Wu, J. Wang, L. Hu, Z. Zhang, and H. Wu, “A network intrusion detection method based on semantic Re-encoding and deep learning,” J. Netw. Comput. Appl., vol. 164, no. March, 2020, doi: 10.1016/j.jnca.2020.102688.
A. H. Farooqi, F. A. Khan, J. Wang, and S. Lee, “A novel intrusion detection framework for wireless sensor networks,” Pers. Ubiquitous Comput., vol. 17, no. 5, pp. 907–919, 2013, doi: 10.1007/s00779-012-0529-y.
C. Xu, J. Shen, X. Du, and F. Zhang, “An Intrusion Detection System Using a Deep Neural Network with Gated Recurrent Units,” IEEE Access, vol. 6, pp. 48697–48707, 2018, doi: 10.1109/ACCESS.2018.2867564.
P. Maniriho, E. Niyigaba, Z. Bizimana, V. Twiringiyimana, L. J. Mahoro, and T. Ahmad, “Anomaly-based Intrusion Detection Approach for IoT Networks Using Machine Learning,” CENIM 2020 - Proceeding Int. Conf. Comput. Eng. Network, Intell. Multimed. 2020, no. Cenim 2020, pp. 303–308, 2020, doi: 10.1109/CENIM51130.2020.9297958.
C. Miranda, G. Kaddoum, E. Bou-harb, S. Garg, and K. Kaur, “for Software-Defined Wireless Sensor Networks,” vol. 15, pp. 2602–2615, 2020.
Y. Imrana, Y. Xiang, L. Ali, and Z. Abdul-Rauf, “A bidirectional LSTM deep learning approach for intrusion detection,” Expert Syst. Appl., vol. 185, no. July, p. 115524, 2021, doi: 10.1016/j.eswa.2021.115524.
S. A. Elsaid and N. S. Albatati, “An optimized collaborative intrusion detection system for wireless sensor networks,” Soft Comput., vol. 24, no. 16, pp. 12553–12567, 2020, doi: 10.1007/s00500-020-04695-0.
J. Granjal, J. M. Silva, and N. Lourenço, “Intrusion detection and prevention in CoAP wireless sensor networks using anomaly detection,” Sensors (Switzerland), vol. 18, no. 8, 2018, doi: 10.3390/s18082445.
T. Sood, S. Prakash, S. Sharma, A. Singh, and H. Choubey, “Intrusion Detection System in Wireless Sensor Network Using Conditional Generative Adversarial Network,” Wirel. Pers. Commun., vol. 126, no. 1, pp. 911–931, 2022, doi: 10.1007/s11277-022-09776-x.
S. Sharma and J. Nagar, “Intrusion Detection in Mobile Sensor Networks: A Case Study for Different Intrusion Paths,” Wirel. Pers. Commun., vol. 115, no. 3, pp. 2569–2589, 2020, doi: 10.1007/s11277-020-07697-1.
M. Almiani, A. AbuGhazleh, A. Al-Rahayfeh, S. Atiewi, and A. Razaque, “Deep recurrent neural network for IoT intrusion detection system,” Simul. Model. Pract. Theory, vol. 101, no. November 2019, p. 102031, 2020, doi: 10.1016/j.simpat.2019.102031.
G. Efstathopoulos et al., “Operational data based intrusion detection system for smart grid,” IEEE Int. Work. Comput. Aided Model. Des. Commun. Links Networks, CAMAD, vol. 2019-September, 2019, doi: 10.1109/CAMAD.2019.8858503.
V. Gowdhaman and R. Dhanapal, “An intrusion detection system for wireless sensor networks using deep neural network,” Soft Comput., vol. 0123456789, no. Manoharan, 2021, doi: 10.1007/s00500-021-06473-y.
B. A. Ashwini and S. S. Manivannan, “Supervised Machine Learning Classification Algorithmic Approach for Finding Anomaly Type of Intrusion Detection in Wireless Sensor Network,” Opt. Mem. Neural Networks (Information Opt., vol. 29, no. 3, pp. 244–256, 2020, doi: 10.3103/S1060992X20030029.
S. Pundir, M. Wazid, D. P. Singh, A. K. Das, J. J. P. C. Rodrigues, and Y. Park, “Intrusion Detection Protocols in Wireless Sensor Networks Integrated to Internet of Things Deployment: Survey and Future Challenges,” IEEE Access, vol. 8, pp. 3343–3363, 2020, doi: 10.1109/ACCESS.2019.2962829.
M. Masdari and H. Khezri, “A survey and taxonomy of the fuzzy signature-based Intrusion Detection Systems,” Appl. Soft Comput. J., vol. 92, p. 106301, 2020, doi: 10.1016/j.asoc.2020.106301.
P. Sun et al., “DL-IDS: Extracting features using CNN-LSTM hybrid network for intrusion detection system,” Secur. Commun. Networks, vol. 2020, 2020, doi: 10.1155/2020/8890306.
J. Asharf, N. Moustafa, H. Khurshid, E. Debie, W. Haider, and A. Wahab, “A review of intrusion detection systems using machine and deep learning in internet of things: Challenges, solutions and future directions,” Electron., vol. 9, no. 7, 2020, doi: 10.3390/electronics9071177.
Alaria, S. K. "A.. Raj, V. Sharma, and V. Kumar.“Simulation and Analysis of Hand Gesture Recognition for Indian Sign Language Using CNN”." International Journal on Recent and Innovation Trends in Computing and Communication 10, no. 4 (2022): 10-14.
Rajput, B. S. .; Gangele, A. .; Alaria, S. K. . Numerical Simulation and Assessment of Meta Heuristic Optimization Based Multi Objective Dynamic Job Shop Scheduling System. ijfrcsce 2022, 8, 92-98.
Rajput, B. S. .; Gangele, A. .; Alaria, S. K. .; Raj, A. . Design Simulation and Analysis of Deep Convolutional Neural Network Based Complex Image Classification System. ijfrcsce 2022, 8, 86-91.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Ashwini B. Abhale, Jayaram Reddy A

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





