Real-Time User-Service Centric Historical Trust Model Based Access Restriction in Collaborative Systems with Blockchain Public Auditing in Cloud
Keywords:
Cloud System, Collaborative Systems, Data Security, Access Restriction, Public Auditing, USHTM-BPA, UCTS, SCTS, FLBPAAbstract
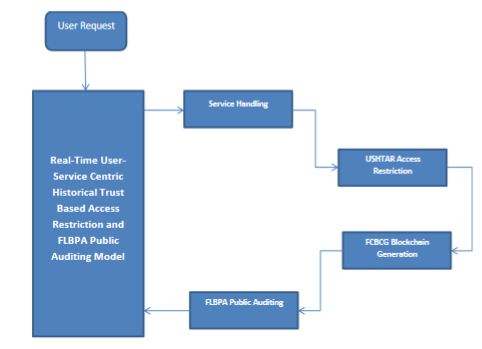
The recent collaborative systems works over the cloud environment which is being encouraged by various service providers in reality. The organizations maintain numerous data in cloud which has been accessed and shared by various users of the environment. The service provider has the responsibility in maintaining the originality of the data and maintaining the security of the data. To enforce both of them, various access restriction and public auditing schemes are available. Number of approaches uses different features of user as well as service. However they suffer to achieve expected performance in data security and public auditing. To handle this issue, a novel real-time User-Service Centric Historical Trust Model with Blockchain Public Auditing (USHTM-BPA) is presented in this article. The method computes User Centric Trust Score (UCTS) and Computes Service Centric Trust Score (SCTS) to measure Trust Weight for the user towards secure access restriction. Further, the method adapts Feature Level Blockchain Public Auditing (FLBPA) which measures feature centric trusted access score (FCTAS) in restricting illegal access to improve data security in public auditing. The proposed method improves the performance of public auditing in collaborative systems and improves data security in cloud.
Downloads
References
H. Amintoosi et al., "Secure and Authenticated Data Access and Sharing Model for Smart Wearable Systems," in IEEE Internet of Things Journal, vol. 9, no. 7, pp. 5368-5379, 1 April1, 2022, doi: 10.1109/JIOT.2021.3109274.
H. R. Hasan, K. Salah, R. Jayaraman, I. Yaqoob, M. Omar and S. Ellahham, "Blockchain-Enabled Telehealth Services Using Smart Contracts," in IEEE Access, vol. 9, pp. 151944-151959, 2021, doi: 10.1109/ACCESS.2021.3126025.
C. Hahn, H. Kwon, D. Kim and J. Hur, "Enabling Fast Public Auditing and Data Dynamics in Cloud Services," in IEEE Transactions on Services Computing, vol. 15, no. 4, pp. 2047-2059, 1 July-Aug. 2022, doi: 10.1109/TSC.2020.3030947.
P. Huang, K. Fan, H. Yang, K. Zhang, H. Li and Y. Yang, "A Collaborative Auditing Blockchain for Trustworthy Data Integrity in Cloud Storage System," in IEEE Access, vol. 8, pp. 94780-94794, 2020, doi: 10.1109/ACCESS.2020.2993606.
X. Yang, X. Pei, M. Wang, T. Li and C. Wang, "Multi-Replica and Multi-Cloud Data Public Audit Scheme Based on Blockchain," in IEEE Access, vol. 8, pp. 144809-144822, 2020, doi: 10.1109/ACCESS.2020.3014510.
Y. Zhang, J. Yu, R. Hao, C. Wang and K. Ren, "Enabling Efficient User Revocation in Identity-Based Cloud Storage Auditing for Shared Big Data," in IEEE Transactions on Dependable and Secure Computing, vol. 17, no. 3, pp. 608-619, 1 May-June 2020, doi: 10.1109/TDSC.2018.2829880.
Zhitao Guan, Achieving Secure Search over Encrypted Data for e-Commerce: A Blockchain Approach, ACM Transactions on Internet TechnologyVol. 21, No. 1, 2021.
Xiaolong Xu, Concurrent Practical Byzantine Fault Tolerance for Integration of Blockchain and Supply Chain, ACM Transactions on Internet TechnologyVol. 21, No. 1, 2021.
Juhno Kim, Intelligent Mediator-based Enhanced Smart Contract for Privacy Protection, ACM Transactions on Internet Technology Volume 21Issue 1February 2021 .
Jidian Yang et al., “A Trusted Routing Scheme Using Blockchain and Reinforcement Learning for Wireless Sensor Networks”, Sensors, Vol.19, pp.1-19, 2019.
Wei She, Blockchain Trust Model for Malicious Node Detection in Wireless Sensor Networks, Research Gate, 2019.
Qi Liu, Research on trust mechanism of cooperation innovation with big data processing based on blockchain, Springer Link (WCN), 2019.
Chen Y, A Blockchain-Based Collocation Storage Architecture for Data Security Process Platform of WSN, IEEE (CSCWD), 2018.
S. Mudepalli, et. Al "An efficient data retrieval approach using blowfish encryption on cloud ciphertext retrieval in cloud computing," IEEE (ICICCS), pp. 267-271, 2017.
R. Nivedhaa and J. J. Justus, "A Secure Erasure Cloud Storage System Using advanced Encryption Standard Algorithm and Proxy Re-Encryption," IEEE (ICCSP), pp. 0755-0759, 2018.
M. Bouchaala, et.al "Revocable Sliced CipherText Policy Attribute Based Encryption Scheme in Cloud Computing," IEEE (IWCMC), pp. 1860-1865, 2019.
V. R. Prabha and P. Latha, "Fuzzy trust protocol for malicious node detection in wireless sensor networks", Wireless Pers. Commun., vol. 94, no. 4, pp. 2549-2559, 2017.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 N. Vel Murugesh Kumar, D. Naveen Raju, Gopirajan PV, P. Subhashini

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





