A Secure Multi-Path Communication through Dynamic Path Identifiers to Prevent Denial-of-Service Flooding Attacks
Keywords:
Denial of Service, Flooding Attack, Weighted Adaptive Model, SecurityAbstract
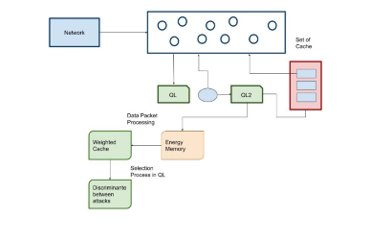
Denial of service is characterized by the explicit attempt of the attackers to prevent legitimate user services. With the distributed denial-of-service multiple machines are deployed machines in the network. The denial of service affects the packet stream with the key resources rendering the legitimate clients to provide the ultimate access to the arbitrary damage. In DDoS environment the attacks are distributed with the largescale attempt the malicious users for the enormous number of network packets. The proposed model uses the weighted adaptive cache clustering (WACC) model for the denial of service flooding attacks in the network. The proposed WACC model uses the adaptive model in the estimation of the attack scenario in the network. The proposed WACC model exhibits the reduced False positive Rate, throughput and response rate. The proposed WACC model achieves the maximal delay of 35.41 ms while the conventional TEV achieves the maximal packet delay of 38.15ms and EMC provides the 42.69ms. The estimation expressed that the proposed WACC model achieves a higher throughput value of 88.35%. The analysis concluded that the proposed WACC model achieves improved performance for the prevention of denial-of-services flooding attacks.
Downloads
References
Kurian, S., & Ramasamy, L. (2021). Securing Service Discovery from Denial of Service Attack in Mobile Ad Hoc Network (MANET). International Journal of Computer Networks and Applications, 8(5), 619-633.
Islam, M. N. U., Fahmin, A., Hossain, M., & Atiquzzaman, M. (2021). Denial-of-service attacks on wireless sensor network and defense techniques. Wireless Personal Communications, 116(3), 1993-2021.
Xu, Y., Deng, G., Zhang, T., Qiu, H., & Bao, Y. (2021). Novel denial-of-service attacks against cloud-based multi-robot systems. Information Sciences, 576, 329-344.
Radain, D., Almalki, S., Alsaadi, H., & Salama, S. (2021, March). A Review on Defense Mechanisms Against Distributed Denial of Service (DDoS) Attacks on Cloud Computing. In 2021 International Conference of Women in Data Science at Taif University (WiDSTaif) (pp. 1-6). IEEE.
Thangavel, S., & Kannan, S. (2022). Detection and trace back of low and high volume of distributed denial‐of‐service attack based on statistical measures. Concurrency and Computation: Practice and Experience, 34(8), e5428.
Tripathi, N., & Hubballi, N. (2021). Application layer denial-of-service attacks and defense mechanisms: a survey. ACM Computing Surveys (CSUR), 54(4), 1-33.
Alamiedy, T. A., Anbar, M. F., Belaton, B., Kabla, A. H., & Khudayer, B. H. (2021, August). Ensemble Feature Selection Approach for Detecting Denial of Service Attacks in RPL Networks. In International Conference on Advances in Cyber Security (pp. 340-360). Springer, Singapore.
Gupta, B. B., Chaudhary, P., Chang, X., & Nedjah, N. (2022). Smart defense against distributed Denial of service attack in IoT networks using supervised learning classifiers. Computers & Electrical Engineering, 98, 107726.
Syed, N. F., Baig, Z., Ibrahim, A., & Valli, C. (2020). Denial of service attack detection through machine learning for the IoT. Journal of Information and Telecommunication, 4(4), 482-503.
Muhammad, A. W., Foozy, C. F. M., & Azhari, A. (2020). Machine Learning-Based Distributed Denial of Service Attack Detection on Intrusion Detection System Regarding to Feature Selection. International Journal of Artificial Intelligence Research, 4(1), 1-8.
Gohil, M., & Kumar, S. (2020, December). Evaluation of classification algorithms for distributed denial of service attack detection. In 2020 IEEE Third International Conference on Artificial Intelligence and Knowledge Engineering (AIKE) (pp. 138-141). IEEE.
Alhaidari, F. A., & Alrehan, A. M. (2021). A simulation work for generating a novel dataset to detect distributed denial of service attacks on Vehicular Ad hoc NETwork systems. International Journal of Distributed Sensor Networks, 17(3), 15501477211000287.
Mihoub, A., Fredj, O. B., Cheikhrouhou, O., Derhab, A., & Krichen, M. (2022). Denial of service attack detection and mitigation for internet of things using looking-back-enabled machine learning techniques. Computers & Electrical Engineering, 98, 107716.
Aljuhani, A. (2021). Machine learning approaches for combating distributed denial of service attacks in modern networking environments. IEEE Access, 9, 42236-42264.
Kuadey, N. A. E., Maale, G. T., Kwantwi, T., Sun, G., & Liu, G. (2021). DeepSecure: Detection of Distributed Denial of Service Attacks on 5G Network Slicing—Deep Learning Approach. IEEE Wireless Communications Letters, 11(3), 488-492.
Maranhão, J. P. A., da Costa, J. P. C., Javidi, E., de Andrade, C. A. B., & de Sousa Jr, R. T. (2021). Tensor based framework for Distributed Denial of Service attack detection. Journal of Network and Computer Applications, 174, 102894.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Ashok Kumar Yadav , Vijaya Bhaskar Ch. , Nagaraju M., J. Emerson Raja, Sachin S. Pund, Alka Kumari

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





