Machine Learning Approach for Malware Detection and Classification Using Malware Analysis Framework
Keywords:
Malware Detection, API-call, Static and dynamic analysis, malware classification, behavior-based analysisAbstract
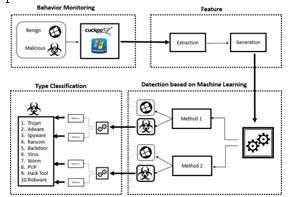
The world's digitalization is currently being threatened by the daily appearance of new and complicated viruses. As a result, the conventional signature-based approaches for malware detection are practically rendered useless. Modern research studies have demonstrated the effectiveness of machine-learning algorithms in terms of malware identification. In this study, we suggested a system to identify and categorize various files (such as exe, pdf, PHP, etc.), and API calls as benign and harmful utilizing two-level classifiers, namely Macro (for malware detection) and Micro (for classification of malware files as a Trojan, Spyware, Adware, etc.). One of the most used data mining (DM) methods is classification. In this research, we describe a classification technique for DM for malware discovery. On the basis of the characteristics and behaviors of each virus, we suggested many categorization approaches to identify malware. The malware traits have been identified using a dynamic analysis technique. Our solution executes sample files in a virtual environment using Cuckoo Sandbox to generate static and dynamic analysis reports. Additionally, utilizing the data produced by the Cuckoo Sandbox, a unique feature selection, and extraction segment has been produced that operates based on static, behavioral, and network analysis. Machine learning models are created utilizing the Weka Framework and training datasets. The experimental findings utilizing the suggested framework demonstrate high rates of detection and classification using various Machine Learning Algorithms.
Downloads
References
Kumar, R., Alenezi, M., Ansari, M. T. J., Gupta, B. K., Agrawal, A., & Khan, R. A. , “Evaluating the impact of malware analysis techniques for securing web applications through a decision-making framework under fuzzy environment”. Int. J. Intell. Eng. Syst, 13(6), 94-109, 2020
Balaji, K. M., & Subbulakshmi, T., “Malware Analysis Using Classification and Clustering Algorithms”, International Journal of e-Collaboration (IJeC),18(1), 1-26,2022
Akhtar, M. S., & Feng, T., “Malware Analysis and Detection Using Machine Learning Algorithms”, Symmetry, 14(11), 2304, 2022.
Hadiprakoso, R. B., Kabetta, H., & Buana, I. K. S, “Hybrid-based malware analysis for effective and efficiency android malware detection”. In 2020 International Conference on Informatics, Multimedia, Cyber and Information System (ICIMCIS), (pp. 8-12). IEEE,2020.
Hwang, C., Hwang, J., Kwak, J., & Lee, T., “Platform-independent malware analysis applicable to windows and Linux environments”, Electronics, 9(5), 793,2020.
Bermejo Higuera, J., Abad Aramburu, C., Bermejo Higuera, J. R., Sicilia Urban, M. A., & Sicilia Montalvo, J. A., “ Systematic approach to malware analysis (SAMA)”, Applied Sciences, 10(4), 1360,2020.
Mehtab, A., Shahid, W. B., Yaqoob, T., Amjad, M. F., Abbas, H., Afzal, H., & Saqib, M. N., “AdDroid: rule-based machine learning framework for android malware analysis. Mobile Networks and Applications”, 25(1), 180-192,2020.
Akhtar, M. S., & Feng, T., “Malware Analysis and Detection Using Machine Learning Algorithms”, Symmetry, 14(11), 2304,2022.
S Aboaoja, F. A., Zainal, A., Ghaleb, F. A., Al-rimy, B. A. S., Eisa, T.A. E., & Elnour, A. A. H., “Malware Detection Issues, Challenges, and Future Directions: A Survey”, Applied Sciences, 12(17), 8482,2022.
Smith, M. R., Johnson, N. T., Ingram, J. B., Carbajal, A. J., Haus, B. I., Domschot, E., .& Kegelmeyer, W. P, “Mind the gap: On bridging the semantic gap between machine learning and malware analysis”, In Proceedings of the 13th ACM Workshop on Artificial Intelligence and Security, (pp. 49-60),2020.
de Vicente Mohino, J. J., Bermejo-Higuera, J., Bermejo Higuera, J. R., Sicilia, J. A., Sánchez Rubio, M., & Martínez Herraiz, J. J. “MMALE a methodology for malware analysis in linux environments”,2021.
Pereberina, A., Kostyushko, A., & Tormasov, A., “An approach to dynamic malware analysis based on system and application code split”, Journal of Computer Virology and Hacking Techniques,1-11,2022.
Almomani, I., Ahmed, M., & El-Shafai, W., “Android malware analysis in a nutshell”, PloS one,17(7), e0270647,2022.
McDole, A., Gupta, M., Abdelsalam, M., Mittal, S., Alazab, M., “Deep Learning Techniques for Behavioral Malware Analysis in Cloud IaaS”, In: Stamp, M., Alazab, M., Shalaginov, A. (eds) Malware Analysis Using Artificial Intelligence and Deep Learning. Springer, Cham, (pp. 269-285), 2021
Jeffrey, N., Tan, Q., & Villar, J. R., “Anomaly Detection of Security Threats to Cyber-Physical Systems: A Study”, In International Workshop on Soft Computing Models in Industrial and Environmental Applications,(pp. 3-12). Springer, Cham,2023
Amer, E., Zelinka, I., & El-Sappagh, S., “A multi-perspective malware detection approach through behavioral fusion of API call sequence”, Computers & Security,110, 102449,2021
Zou, D., Wu, Y., Yang, S., Chauhan, A., Yang, W., Zhong, J., ... & Jin, H., “IntDroid: Android malware detection based on API intimacy analysis”, ACM Transactions on Software Engineering and Methodology (TOSEM), 30(3), 1-32,2021
Schofield, M., Alicioglu, G., Binaco, R., Turner, P., Thatcher, C., Lam, A., & Sun, B, “Convolutional neural network for malware classification based on API call sequence”, In Proceedings of the 8th International Conference on Artificial Intelligence and Applications, (AIAP 2021),2021
Chaganti, R., Ravi, V., & Pham, T. D, “A multi-view feature fusion approach for effective malware classification using Deep Learning”, Journal of Information Security and Applications, 72, 103402,2023
Zhu, H. J., Gu, W., Wang, L. M., Xu, Z. C., & Sheng, V. S., “Android malware detection based on multi-head squeeze-and-excitation residual network”, Expert Systems with Applications, 212, 118705,2023
Hasan, H., Ladani, B. T., & Zamani, B., “MEGDroid: A model-driven event generation framework for dynamic android malware analysis”, Information and Software Technology, 135, 106569,2021
Sraw, J. S., & Kumar, K., “Using static and dynamic malware features to perform malware ascription”, ECS Transactions, 107(1), 3187,2022.
Thakur, D., Singh, J., Dhiman, G., Shabaz, M., & Gera, T., “Identifying major research areas and minor research themes of android malware analysis and detection field using LSA”, Complexity,2021
Al-Dwairi, M., Shatnawi, A. S., Al-Khaleel, O., & Al-Duwairi, B., “Ransomware-Resilient Self-Healing XML Documents. Future Internet”, 14(4), 115,2022.
Rafiq, H., Aslam, N., Ahmed, U., & Lin, J. C. W., “Mitigating Malicious Adversaries Evasion Attacks in Industrial Internet of Things”, IEEE Transactions on Industrial Informatics, 2022
Lebbie, M., Prabhu, S. R., & Agrawal, A. K., “Comparative Analysis of Dynamic Malware Analysis Tools. In Proceedings of the International Conference on Paradigms of Communication”, Computing and Data Sciences, (pp. 359-368). Springer, Singapore,2022
Kartel, A., Novikova, E., & Volosiuk, A., “Analysis of visualization techniques for malware detection”, In 2020 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus) (pp. 337-340), 2020
Liu, S., Feng, P., Wang, S., Sun, K., & Cao, J., “Enhancing malware analysis sandboxes with emulated user behavior”, 2022, Computers & Security, 115, 102613,2020
Yadav, C. S., Singh, J., Yadav, A., Pattanayak, H. S., Kumar, R., Khan, A. A., ... & Alharby, S., “Malware Analysis in IoT & Android Systems with Defensive Mechanism”, Electronics, 11(15), 2354,2022.
Lebbie, M., Prabhu, S. R., & Agrawal, A. K., “Comparative Analysis of Dynamic Malware Analysis Tools”, In Proceedings of the International Conference on Paradigms of Communication, Computing and Data Sciences, (pp. 359-368), Springer, Singapore,2022.
Palša, J., Ádám, N., Hurtuk, J., Chovancová, E., Madoš, B., Chovanec, M., & Kocan, S., “MLMD—A Malware-Detecting Antivirus Tool Based on the XGBoost Machine Learning Algorithm, Applied Sciences, 12(13), 6672,2022
Louk, M. H. L., & Tama, B. A., “Tree-Based Classifier Ensembles for PE Malware Analysis: A Performance Revisit”, Algorithms, 15(9), 332,2022
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





