Intrusion Detection by Stacked Deep Ensemble Model with Entropy and Correlation Feature Set
Keywords:
Intrusion Detection, Stacked Deep Ensemble Model, Data normalization, Improved correlation based feature, Deep Belief Network (DBN), Deep Maxout Network, Customized Convolutional Neural Network (CCNN)Abstract
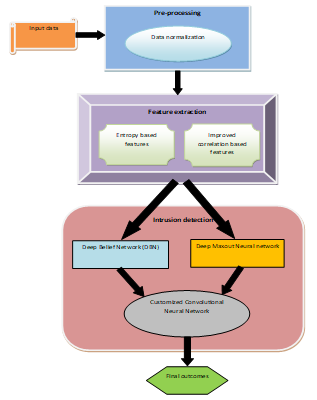
Nowadays, in order to improve the routine activities, interoperability and interconnectivity of computing systems are extensively used. In addition, it creates a way to vulnerabilities that are far beyond the reach of human control. Due to the vulnerabilities, data transfer must include cyber-security measures. Secure connectivity demands improvements to security mechanisms to counter emerging security risks and security systems to mitigate the threats. This paper proposes Intrusion Detection by Stacked Deep Ensemble Model (IDSDEM) which has three working stages. Initially, in the pre-processing stage, data normalization process is conducted to reduce the data redundancy and increases the consistency of data for further process. Afterwards feature extraction stage takes place where the features such as entropy based as well as improved correlation based features were extracted. Finally, intrusion detection is conducted where a stacked deep ensemble model which includes the classifiers like Deep Belief Network (DBN), Deep Maxout Network and Customized Convolutional Neural Network (CCNN) is employed to provide effective intrusion detection. The outcomes demonstrated that the developed IDSDEM can offer superior performance with respect to detection accuracy, precision and other measures.
Downloads
References
Liu, G., Zhao, H., Fan, F., Liu, G., Xu, Q. and Nazir, S., “An Enhanced Intrusion Detection Model Based on Improved kNN in WSNs”. Sensors, 22(4), p.1407, (2022).
Maheswari, M. and Karthika, R.A., “A novel QoS based secure unequal clustering protocol with intrusion detection system in wireless sensor networks”. Wireless Personal Communications, 118(2), pp.1535-1557, (2021).
Gowdhaman, V. and Dhanapal, R., “An intrusion detection system for wireless sensor networks using deep neural network”. Soft Computing, 26(23), pp.13059-13067, (2022).
Elsaid, S.A. and Albatati, N.S., “An optimized collaborative intrusion detection system for wireless sensor networks”. Soft Computing, 24(16), pp.12553-12567, (2020).
Mohapatra, H., Rath, S., Panda, S. and Kumar, R., “Handling of man-in-the-middle attack in wsn through intrusion detection system”. International journal, 8(5), pp.1503-1510, (2020).
Safaldin, M., Otair, M. and Abualigah, L., “Improved binary gray wolf optimizer and SVM for intrusion detection system in wireless sensor networks”. Journal of ambient intelligence and humanized computing, 12(2), pp.1559-1576, (2021).
Zhang, W., Han, D., Li, K.C. and Massetto, F.I., “Wireless sensor network intrusion detection system based on MK-ELM”. Soft Computing, 24(16), pp.12361-12374, (2020).
Gavel, S., Raghuvanshi, A.S. and Tiwari, S., “A novel density estimation based intrusion detection technique with Pearson’s divergence for wireless sensor networks”. ISA transactions, 111, pp.180-191, (2021).
Godala, S. and Vaddella, R.P.V., “A study on intrusion detection system in wireless sensor networks”. International Journal of Communication Networks and Information Security, 12(1), pp.127-141, (2020).
Baraneetharan, E., “Role of machine learning algorithms intrusion detection in WSNs: a survey”. Journal of Information Technology, 2(03), pp.161-173, (2020).
Gite, P., Chouhan, K., Krishna, K.M., Nayak, C.K., Soni, M. and Shrivastava, A., “ML Based Intrusion Detection Scheme for various types of attacks in a WSN using C4. 5 and CART classifiers”. Materials Today: Proceedings, (2021).
Singh, A., Nagar, J., Sharma, S. and Kotiyal, V., “A Gaussian process regression approach to predict the k-barrier coverage probability for intrusion detection in wireless sensor networks”. Expert Systems with Applications, 172, p.114603, (2021).
Aldweesh, A., Derhab, A. and Emam, A.Z., 2020. Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowledge-Based Systems, 189, p.105124.
Sinha, S. and Paul, A., “Neuro-fuzzy based intrusion detection system for wireless sensor network”. Wireless Personal Communications, 114(1), pp.835-851, (2020).
Nancy, P., Muthurajkumar, S., Ganapathy, S., Santhosh Kumar, S.V.N., Selvi, M. and Arputharaj, K., “Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks”. IET Communications, 14(5), pp.888-895, (2020).
Almomani, I. and Alromi, A., “Integrating software engineering processes in the development of efficient intrusion detection systems in wireless sensor networks. Sensors, 20(5)”, p.1375, (2020).
Amaran, S. and Mohan, R.M., “Intrusion detection system using optimal support vector machine for wireless sensor networks”. In 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS) (pp. 1100-1104). IEEE, (2021).
Kaur, N. and Rattan, P., “A critical review of intrusion detection systems in WSN: challenges & future directions”. Annals of the Romanian Society for Cell Biology, pp.3020-3028, (2021).
Alruhaily, N.M. and Ibrahim, D.M., “A multi-layer machine learning-based intrusion detection system for wireless sensor networks”. International Journal of Advanced Computer Science and Applications, 12(4), pp.281-288, (2021).
Umarani, C. and Kannan, S., “Intrusion detection system using hybrid tissue growing algorithm for wireless sensor network”. Peer-to-Peer Networking and Applications, 13(3), pp.752-761, (2020).
Otoum, S., Kantarci, B. and Mouftah, H.T., “A novel ensemble method for advanced intrusion detection in wireless sensor networks”. In Icc 2020-2020 ieee international conference on communications (icc) (pp. 1-6). IEEE, (2020).
Jiang, S., Zhao, J. and Xu, X., “SLGBM: An intrusion detection mechanism for wireless sensor networks in smart environments”. IEEE Access, 8, pp.169548-169558, (2020).
Alsahli, M.S., Almasri, M.M., Al-Akhras, M., Al-Issa, A.I. and Alawairdhi, M., “Evaluation of machine learning algorithms for intrusion detection system in WSN”. International Journal of Advanced Computer Science and Applications, 12(5), (2021).
Alwan, M.H., Hammadi, Y.I., Mahmood, O.A., Muthanna, A. and Koucheryavy, A., “High Density Sensor Networks Intrusion Detection System for Anomaly Intruders Using the Slime Mould Algorithm”. Electronics, 11(20), p.3332, (2022).
Abhale, A.B. and Manivannan, S.S., “Supervised machine learning classification algorithmic approach for finding anomaly type of intrusion detection in wireless sensor network”. Optical Memory and Neural Networks, 29(3), pp.244-256, (2020).
Aljanabi, M., Ismail, M.A. and Ali, A.H., “Intrusion detection systems, issues, challenges, and needs”. International Journal of Computational Intelligence Systems, 14(1), pp.560-571, (2021).
https://en.wikipedia.org/wiki/Database_normalization
https://www.javatpoint.com/entropy-in-machine-learning
https://www.google.com/search?q=pearson+correlation+formula&rlz=1C1CHBF
Zhao, L., Wang, Z., Wang, X. and Liu, Q., “Driver drowsiness detection using facial dynamic fusion information and a DBN”. IET Intelligent Transport Systems, 12(2), pp.127-133, (2018).
Cai, M., Shi, Y. and Liu, J., “Deep maxout neural networks for speech recognition”. In 2013 IEEE Workshop on Automatic Speech Recognition and Understanding (pp. 291-296). IEEE, (2013).
Davanam, G., Kumar, T. P., & Kumar, M. S. (2021). Efficient energy management for reducing cross layer attacks in cognitive radio networks. Journal of Green Engineering, 11, 1412-1426.
Kumar, M. S., Siddardha, B., Reddy, A. H., Reddy, C. V. S., Shaik, A. B., & Ganesh, D. (2022). APPLYING THE MODULAR ENCRYPTION STANDARD TO MOBILE CLOUD COMPUTING TO IMPROVE THE SAFETY OF HEALTH DATA. Journal of Pharmaceutical Negative Results, 1911-1917.
P. Sai Kiran, "Power aware virtual machine placement in IaaS cloud using discrete firefly algorithm." Applied Nanoscience (2022): 1-9.
Pavan Kumar, T.,(2021). Novel Defense Framework for Cross-layer Attacks in Cognitive Radio Networks. In International Conference on Intelligent and Smart Computing in Data Analytics (pp. 23-33). Springer, Singapore.
Neelima, P., & Kumar, M. S. (2017, April). A memetic algorithm for multi objective vehicle routing problem with time windows. In 2017 IEEE International Conference on Electrical, Instrumentation and Communication Engineering (ICEICE) (pp. 1-8). IEEE.
P. Sai Kiran, and M. S Kumar. "Resource aware virtual machine placement in IaaS cloud using bio-inspired firefly algorithm." Journal of Green Engineering 10 (2020): 9315-9327.
Thummala Pavan Kumar, "Optimised Levenshtein centroid cross‐layer defence for multi‐hop cognitive radio networks." IET Communications 15.2 (2021): 245-256.
Bari, A.H. and Gavrilova, M.L., “Novel Multi-layer Perceptron Architecture for Gait Recognition” (2019).
Guo, P., Xue, Z., Mtema, Z., Yeates, K., Ginsburg, O., Demarco, M., Long, L.R., Schiffman, M. and Antani, S., “Ensemble deep learning for cervix image selection toward improving reliability in automated cervical precancer screening”. Diagnostics, 10(7), p.451, (2020).
Almomani, I., Al-Kasasbeh, B. and Al-Akhras, M., 2016. WSN-DS: A dataset for intrusion detection systems in wireless sensor networks. Journal of Sensors, 2016.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





