An Initial Study of Cyber Security for Web Services in Malaysian Organizations
Keywords:
Cyber security, information Technology, Malaysia, web servicesAbstract
In the recent and next years, Malaysian enterprises have seen an increase in the development of information technology (IT). This is a result of the Malaysian government actively promoting IT usage throughout all companies in Malaysia, whether they are in the public or private sectors. Utilizing IT including web services will increase an organization's production and quality. Therefore, they require a well-planned implementation of the IT infrastructure and tools. Using web services will ensure that its operations are successful in supporting long-term business ambitions. Besides that, the cyber security play important role to ensure that the web services and IT infrastructures execute well along the organization’s business successful. So, is these digital environments in Malaysian organizations safe it is not a Malaysian IT culture and didn’t have enough and tough knowledge of cyber security. However, how to promote cyber security to Malaysian organizations for web services? So, promotion can be done by using the web services itself by putting more knowledge and study on the secure usage of IT facilities in Malaysian organizations.
Downloads
References
Definition for Common Security Terms, http://www.mycert.org.my/html [1 MARCH 2020]
Davis, G.B. and Olson, M.H. (1985) Management Information System: Conceptual Foundations, Structure and Development (2nd edn), McGraw-Hill.
Firkhan Ali, H. A., Maziah Na’aman, “Vulnerability Assessment on the Network Security“ in NCSTIE 2006: Proceedings of the International Conference on Science and Technology 2006. PWTC, UiTM Pulau Pinang.
Galliers, R. and Sutherland (1991) Information System Management and Strategy Formulation: The ‘Stages of Growth’ Model Revisited, Journal of Information Systems, Vol 1 No 2 pp. 89-114.
Firkhan Ali, H. A etl. , “Development Of Dual-Factor Authentication For Web Based Application Using SMS”, Proceedings of the ICITS 2008, Kusadasi, Turkey, 2008.
Firkhan Ali, H. A etl., “Development of Vulnerability and Security Reporting System for Computer System and Networking” in SITIA 2008: Proceedings of the Seminar In The Intelligent Applications 2008, Surabaya, Indonesia, 2008.
Guomin Yang, Duncan S. Wong, Huaxiong Wang dan Xiaotie Deng (2006). “Formal Analysis and Systematic Construction of Two-factor Authentication Scheme.” City University of Hong Kong, China.
MyCERT About Us’, http://www.mycert.org.my/html [1 MARCH 2020]
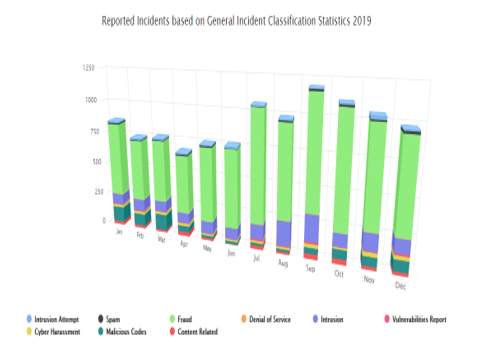
Incident Statistic (2017-2019), http://www.mycert.org.my/html [1 MARCH 2020]
Wendy, R. (1997) Strategic Management and Information Systems (2nd edn), Prentice Hall.
Lederer, A.L and Gardiner, V. (1992) The Process of Strategic Information System Planning, Journal of Strategic Information System Planning, Vol 1No 2 Mar pp. 76-83
Hatch, B., Lee, J. and Kurtz G. (2001) Hacking Linux Exposed: Linux Security and Solutions, Osborne/McGraw-Hill.
Scambray, J., Mcclure, S. and Kurtz G. (2001) Hacking Exposed: Network Security and Solutions, Osborne/McGraw-Hill.
Richard A. Kemmerer et al., (2002), Intrusion Detection: A Brief History and Overview, SECURITY & PRIVACY–2002, Reliable Software Group, Computer Science Department, University of California Santa Barbara.
Norton, P and Stockman, M. (1999) Peter Norton’s Network Security Fundamentals, SAMS Publishing.
Wenke Lee et al., (2000), A Framework for Constructing Features and Models for Intrusion Detection Systems, ACM Transactions on Information and System Security (TISSEC), Volume 3 Issue 4, ACM Press.
Williams, B.K., Sawyer, S.C. and Hutchinson, S.E. (1995) Using Information technology, Richard D. Irwin, Inc.
Ward, J. and Griffiths, P. (1996) Strategic Planning for Information Systems (2nd edn), Wiley.
Zacker, C. (2001) Networking: The Complete Reference, Osborne/McGraw-Hill.
Tipton, H.F. and Krause, M. (2000) Information Security Management Handbook (4th Edition), Auerbach Publications.
Security FAQs’, http://www.mycert.org.my/html [1 MARCH 2020]
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





