Design and Implementation of Machine Learning and Big Data Analytics models for Cloud Computing platforms
Keywords:
large statistics, engine learning, natural linguistic processing, procedure, cybersecurityAbstract
There are concerns regarding the protection of significant digital assets because it is noticeable that cyber attackers are outstripping defenses. AI models need specialized cybersecurity and defense keys in order to lower dangers, enhance information privacy, and enable a secure federated knowledge situation. The growth of “artificial intelligence” has controlled the rise of several new fields, including “machine learning” (ML), “natural language processing” (NLP), CPU vision, and several more. Massive volumes of information are produced in the “Internet of Things” (IoT) age and are acquired from a variety of heterogeneous sources, including “mobile devices”, “sensors”, and “social media”. Big Data faces significant challenges in terms of processing, storage, and analytical capabilities. Firewall security has proven to be insufficient as a result of significant restrictions against external attackers. Given that computer worms and viruses, which are intelligent semi-autonomous agents, are responsible for the majority of network-centric cyberattacks, it has become necessary to combat them with intellectual semi-autonomous mediators that can identify, evaluate, and respond to cyberattacks. Specified that the majority of network-centric cyberattacks are produced by CPU worms and illnesses, which are intelligent semi-autonomous agents, it has become important to combat them with intelligent semi-autonomous agents that can recognise, assess, and respond to cyberattacks.
The study aims to determine the Big Data Analytics and Machine Learning paradigms for usage in cybersecurity and to make use of big data analytics and machine learning.
This study used a case study research methodology. This is because each statistics analytics model for cybersecurity is observed as a unique case that needs to be examined in its own context. Case studies have been used a lot in prior research on cybersecurity. The investigator knows two data analytics models or frameworks through a review of the literature and a study of the 8-person sample. There were eight people interviewed in total. Even if there might not be much data, it is sufficient for the current stages of this investigation. Future studies may look at other publications to discover other data and analytics models that are pertinent to cybersecurity.
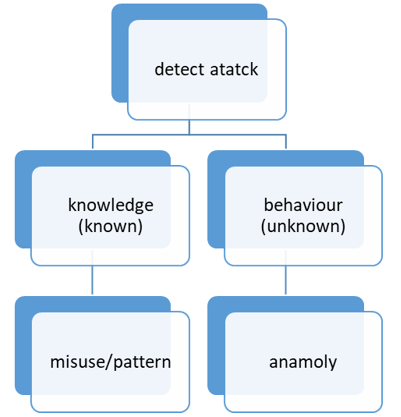
Table 4 illustrates the overall show of our CART procedure in predicting scores on the banks on the training dataset. On the testing data, the precision of the approach was 83.1%. On the test dataset, the approach got a kappa of 88.76% and a reliability of 92.7%. On the training dataset, the SVM figure's overall accuracy for predicting bank health remained at 79.1%. The Kappa statistic and Kappa SD were 67.6% and 0.14, combined. On the testing data, the approach had an efficiency of 92.7% and a kappa of 88.59%. The efficiency of the randomized forest in the training phase was 85.57 %. Large amounts of information are is for connections and trends, leading to the creation of algorithms for these kinds of relationships and patterns. Passive sources of information include laptop data such as IP address, information security certifications, keypad usage, clickstream trends, and WAP data.
Downloads
References
Zeadally, S., Adi, E., Baig, Z., & Khan, I. (2020). Harnessing Artificial Intelligence Capabilities to Improve Cybersecurity. IEEE Access, 8, 1–1. https://doi.org/10.1109/access.2020.2968045
Kong, L. J. (2013). An improved information-security risk assessment algorithm for a hybrid model. International Journal Of Advancements In Computing Technology, 5(2).
Liu, X., Lu, R., Ma, J., Chen, L., & Qin, B. (2016). Privacy-Preserving Patient-Centric Clinical Decision Support System on Naïve Bayesian Classification. IEEE Journal of Biomedical and Health Informatics, 20(2), 655–668. https://doi.org/10.1109/jbhi.2015.2407157
Shah, S. K., Tariq, Z., Lee, J., & Lee, Y. (2021). Event-Driven Deep Learning for Edge Intelligence (EDL-EI). Sensors, 21(18), 6023. https://doi.org/10.3390/s21186023
Gupta, C., Johri, I., Srinivasan, K., Hu, Y.-C., Qaisar, S. M., & Huang, K.-Y. (2022). A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks. Sensors, 22(5), 2017. https://doi.org/10.3390/s22052017
BERMAN, D.S., Buczak, A.L., Chavis, J.S., and Corbett, C.L. (2019). “Survey of Deep Learning Methods for Cyber Security”, Information 2019, 10, 122; doi:10.3390/info10040122
SARKER, I. H., Kayes, A. S. M., Badsha, S., Alqahtani, H., Watters, P., & Ng, A. (2020). Cybersecurity data science: an overview from machine learning perspective. Journal of Big Data. https://doi.org/10.1186/s40537-020-00318-5
BRINGAS, P.B., and Santos, I., (2010). Bayesian Networks for Network Intrusion Detection, Bayesian Network, Ahmed Rebai (Ed.), ISBN: 978-953-307- 124-4, InTech, Available from: http://www. intechopen.com/books/bayesian-network/bayesiannetworks-for-network-intrusion-detection
BLOICE, M. & Holzinger, A., 2018. A Tutorial on Machine Learning and Data Science Tools with Python. Graz, Austria: s.n
2. Wilson, B. M. R., Khazaei, B., & Hirsch, L. (2015, November). Enablers and barriers of cloud adoption among Small and Medium Enterprises in Tamil Nadu. In: 2015 IEEE International Conference on Cloud Computing in Emerging Markets (CCEM) (pp. 140-145). IEEE.
HASHEM, I. A. T., Yaqoob, I., Anuar, N. B., Mokhtar, S., Gani, A., & Ullah Khan, S. (2015). The rise of “big data” on cloud computing: Review and open research issues. In Information Systems. https://doi. org/10.1016/j.is.2014.07.006.
SITI Nurul Mahfuzah, M., Sazilah, S., & Norasiken, B. (2017). An Analysis of Gamification Elements in Online Learning to Enhance Learning Engagement. 6th International Conference on Computing & Informatics.
MENZES, F.S.D., Liska, G.R., Cirillo, M.A. and Vivanco, M.J.F. (2016) Data Classification with Binary Response through the Boosting Algorithm and Logistic Regression. Expert Systems with Applications, 69, 62-73. https://doi.org/10.1016/ j.eswa.2016.08.014
HASSAN, H. (2017). Organisational factors affecting cloud computing adoption in small and medium enterprises (SMEs) in service sector. Procedia Computer Science. https://doi.org/10.1016/j.procs. 2017.11.126
BOU-HARB, E., & Celeda, P. (2018). Survey of Attack Projection, Prediction, and Forecasting in Cyber Security. September. https://doi.org/10.1109/ COMST.2018.2871866
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





