Data Mining Techniques for Cloud Privacy Preservation
Keywords:
security, cloud computing, data mining, phishingAbstract
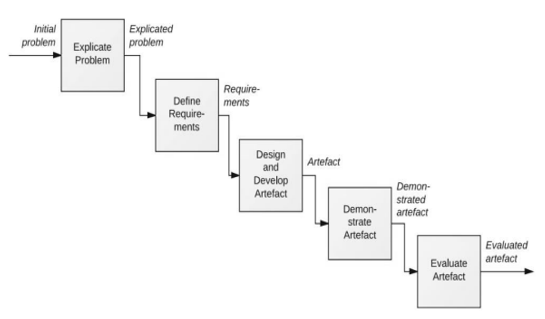
A high standard of phishing prevention became essential when it came to Internet phishing. As a result of sophisticated phishing attacks, a new mitigation challenge was created. Internet phishing has recently raised serious security and financial issues for people and businesses around. There has been a significant financial loss associated with internet services that provide a variety of communication channels, including electronic commerce, online banking, research, and online trading, as well as those that exploit both software and human weaknesses. The aim of the study is to identify the extent of works and their limitations for cloud security, to design and develop the solution for cloud security, and to evaluate the model.
We propose this new model mining model, which consists of two main bases: preprocessing and classification. the accuracy obtained in this study for malware analysis is quite high, with the highest accuracy being 95.2%.
The results of the Intrusion features, Features of Models, Malware Detection Graphs for the data, Attacks Identified from different countries for the data, Machine learning Based Model Implementation, and Accuracy of analysis were analyzed and data were obtained. Deploying sensors or agents on cloud-based systems and apps is often the first step in the data collection process for malware investigation in the cloud. Network-based intrusion detection systems (NIDS) or intrusion prevention systems are a popular way to collect data. An important paradigm that delivers the results for the grouping of requests is the application of SVM to the problem of assault detection.
Downloads
References
Aggarwal G, Bawa M, Ganesan P (2005) Two can keep a secret: a distributed architecture for secure database services. CIDR
Agrawal R, Srikant R (2000) Privacy-preserving data mining. In: Proceedings of the 2000 ACM SIGMOD international conference on management of data—SIGMOD ’00, vol 29, no 2. pp 439–450. http://doi.org/10.1145/342009.335438
Aggarwal CC, Yu PS (2008) A general survey of privacy-preserving data mining models and algorithms. In: Privacy preserving data mining, Chap 2. Springer, New York, pp 11–52. http://doi.org/10.1007/978-0-387-48533
Arunadevi M, Anuradha R. Privacy preserving outsourcing for frequent itemset mining. Int J Innov Res Comp Commun Eng. 2014;2(1):3867–3873.
Baotou T (2010) Research on privacy preserving classification data mining based on random perturbation Xiaolin Zhang Hongjing Bi. 1–6
Belwal R, Varshney J, Khan S (2013) Hiding sensitive association rules efficiently by introducing new variable hiding counter. In: IEEE international conference on service operations and logistics, and informatics, 2008, IEEE/SOLI 2008, vol 1, pp 130–134. doi:10.1109/SOLI.2008.4686377
Chan J, Keng J (2013) Privacy protection in outsourced association rule mining using distributed servers and its privacy notions, pp 1–5
Ciriani V, Vimercati SDC, Foresti S, Samarati P. Privacy-preserving data mining. New York: Springer; 2008. k-anonymous data mining: a survey; pp. 105–136.
Dehkordi MNM, Badie K, Zadeh AKA. A novel method for privacy preserving in association rule mining based on genetic algorithms. J Softw. 2009;4(6):555–562. doi: 10.4304/jsw.4.6.555-562.
Deivanai P, Nayahi J, Kavitha V (2011) A hybrid data anonymization integrated with suppression for preserving privacy in mining multi party data. In: IEEE international conference on recent trends in information technology (ICRTIT)
Dev H, Sen T, Basak M, Ali ME (2012) An approach to protect the privacy of cloud data from data mining based attacks. In: IEEE 2012 SC companion high performance computing, networking, storage and analysis (SCC)
Ding X, Yu Q, Li J, Liu J, Jin H (2013) Distributed anonymization for multiple data providers in a cloud system. In: Database systems for advanced applications. Springer, Berlin, Heidelberg
Domadiya NH, Rao UP (2013) Hiding sensitive association rules to maintain privacy and data quality in database. In: IEEE 3rd international on advance computing conference (IACC), pp 1306–1310
Dong R, Kresman R (2009) Indirect disclosures in data mining. In: Fourth international conference on frontier of computer science and technology, FCST’09
Friedman A, Wolff R, Schuster A. Providing k-anonymity in data mining. VLDB J. 2008;17(4):789–804. doi: 10.1007/s00778-006-0039-5.
Giannotti F, Lakshmanan LVS, Monreale A, Pedreschi D, Wang H. Privacy-preserving mining of association rules from outsourced transaction databases. IEEE Syst J. 2013;7(3):385–395. doi: 10.1109/JSYST.2012.2221854.
Gkoulalas-Divanis A, Verykios VS. Exact knowledge hiding through database extension. IEEE Trans Knowl Data Eng. 2009;21(5):699–713. doi: 10.1109/TKDE.2008.199.
Harnsamut N, Natwichai J (2008) A novel heuristic algorithm for privacy preserving of associative classification. In: PRICAI 2008: trends in artificial intelligence. Springer, Berlin, Heidelberg, pp 273–283
He Y, Siddharth B, Jeffrey FN (2011) Preventing equivalence attacks in updated, anonymized data. In: IEEE 27th international conference on data engineering (ICDE)
Ibrahim A, Jin H, Yassin AA, Zou D (2012) Towards privacy preserving mining over distributed cloud databases. In: IEEE second international conference on cloud and green computing (CGC)
Inan A, Saygin Y (2010) Privacy preserving spatio-temporal clustering on horizontally partitioned data. In: Lecture Notes in Computer Science (including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 6202 LNAI. pp 187–198. http://doi.org/10.1007/978-3-642-16392-0_11
Islam MZ, Brankovic L. Privacy preserving data mining: a noise addition framework using a novel clustering technique. Knowl Based Syst. 2011;24(8):1214–1223. doi: 10.1016/j.knosys.2011.05.011.
Jain YYK, Yadav VKVVK, Panday GGS. An efficient association rule hiding algorithm for privacy preserving data mining. Int J Comp Sci Eng. 2011;3(7):2792–2798.
Kamakshi P (2012) Automatic detection of sensitive attribute in PPDM. In: IEEE international conference on computational intelligence & computing research (ICCIC)
Kamakshi P, Babu AV (2010) Preserving privacy and sharing the data in distributed environment using cryptographic technique on perturbed data 2(4)
Kantarcıoglu M, Vaidya J (2003) Privacy preserving naive bayes classifier for horizontally partitioned data. In: IEEE ICDM workshop on privacy preserving data mining, pp 3–9. http://www.cis.syr.edu/~wedu/ppdm2003/papers/1.pdf
Karim R, Rashid M, Jeong B, Choi H (2012) In: Transactional Databases. pp 303–319
Chandrakar, I., & Hulipalled, V. R. (2020). Techniques for Preserving Privacy in Data Mining for Cloud Storage: A Survey. Advances in Intelligent Systems and Computing, 452–461. https://doi.org/10.1007/978-981-15-6353-9_42
Phan, Trung & Toan, Truong & Van Tuyen, Dang & Huong, Truong & Thanh, Nguyen. (2016). OpenFlowSIA: An optimized protection scheme for software-defined networks from flooding attacks. 13-18. 10.1109/CCE.2016.7562606.
Kaaniche, N., & Laurent, M. (2017). Data security and privacy preservation in cloud storage environments based on cryptographic mechanisms. Computer Communications, 111, 120-141. https://doi.org/10.1016/j.comcom.2017.07.006
Purohit, R., & Bhargava, D. (2017). An illustration to secured way of data mining using privacy preserving data mining. Journal of Statistics and Management Systems, 20(4), 637-645.
Kreso, I., Kapo, A., & Turulja, L. (2021). Data mining privacy preserving: Research agenda. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 11(1), e1392.
Binbusayyis, A., & Vaiyapuri, T. (2020). Comprehensive analysis and recommendation of feature evaluation measures for intrusion detection. Heliyon, 6(7). https://doi.org/10.1016/j.heliyon.2020.e04262
Elhadi, Ammar & Maarof, Mohd & Barry, Bazara. (2013). Improving the Detection of Malware Behaviour Using Simplified Data Dependent API Call Graph. International Journal of Security and Its Applications. 7. 29-42. 10.14257/ijsia.2013.7.5.03.
Florian, E., Sgarbossa, F., & Zennaro, I. (2021). Machine learning-based predictive maintenance: A cost-oriented model for implementation. International Journal of Production Economics, 236, 108114. https://doi.org/10.1016/j.ijpe.2021.108114
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





