An Approach to Detect Wormhole Attack in Mobile Ad Hoc Networks Using Direct Trust Based Detection Approach
Keywords:
MANET, Wormhole Attacks, Jellyfish Attack, Routing Protocols, Performance MetricAbstract
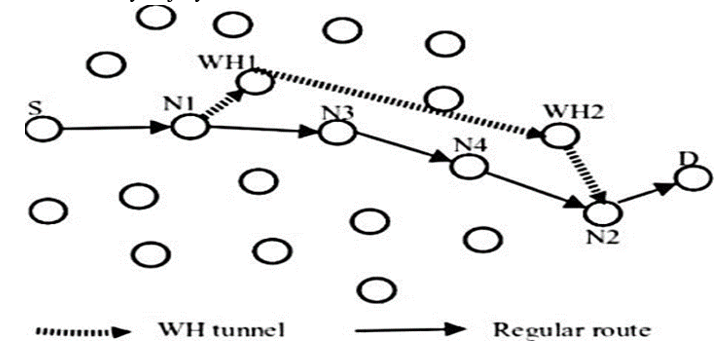
Mobile ad hoc organization is used in numerous applications climate strategic projects or standard gadget organization. The reason toward the rear of the developing acknowledgment of magnets is the simple accessibility of compact gadgets. The versatile Ad Hoc Network isn't simply smooth to introduce yet notes might be presented or eliminated powerfully shape it. Besides, the local area doesn't need a proper foundation. The above expressed make magnet exceptionally reasonable in various bundles however at the expense of raised weakness to Cyber-assaults. The greatest imperative attacks in Manet are wormhole attack and jellyfish assault. The writing needs inside the methods that could endless supply of these assaults simultaneously. In this examination we've proposed a coordinated strategy that is equipped for stagger on both wormhole and jellyfish assault the utilization of indistinguishable boundaries.
Downloads
References
International conference on recent cognizance in wireless communication & image processing “A Review on Performance Evaluation of Routing Protocols in MANET” (December’2014), PUBLISHED IN SPRINGER 2015 EDITION.
Ahmed, Diaa Eldein & Khalifa, Othman, “An Overview of MANETs: Applications, Characteristics, Challenges, and Recent Issues,” International Journal of Engineering and Advanced Technology (IJEAT) ISSN, pp. 2249 – 8958, 2017.
Shruti Thapar and Sudhir Kumar Sharma, “Analysis of Isolation access of Wormhole Attack in Mobile Ad hoc Network using Delay Prediction Technique”, International journal of Advanced Science and Technology (IJAST), ISSN: 2005-4238 IJAST, volume-29 issue-6, 2020, page no.- 9401-9411.
W. A. Aliady and S. A. Al-Ahmadi, "Energy Preserving Secure Measure Against Wormhole Attack in Wireless Sensor Networks," in IEEE Access, vol. 7, pp. 84132-84141, 2019.
Shruti Thapar and Sudhir Kumar Sharma, “Study of Direct Trust Based Detection Algorithm for Prohibiting Jellyfish Attack in MANET”, ILKOGRETIM Online, doi: 10.17051/ ilkoline.2021.04.234, volume 20 issue 4, 2021, page no. -2052-2057.
Azer, M. & El-Kassas, Sherif & El-Soudani, Magdy, “A Full Image of the Wormhole Attacks - Towards Introducing Complex Wormhole Attacks in wireless Ad Hoc Networks,” 2009.
Shruti Thapar, M Venu Gopala Rao, Babita Jain, Rajkumar Kaushik, “A Secure Routing for MANET using Internet of Things”, International Journal of Early Childhood Special Education (INT-JECSE)DOI:10.9756/INTJECSE/V14I5.305 ISSN: 1308-5581 Vol 14, Issue 05 2022, pp. 2957-2965.
V. Krundyshev, M. Kalinin and P. Zegzhda, "Artificial swarm algorithm for VANET protection against routing attacks," 2018 IEEE Industrial Cyber- Physical Systems (ICPS), pp. 795-800, 2018.
Shruti Thapar, M Venu Gopala Rao, Babita Jain, Rohan Sharma , “Research Article on Routing Protocols for MANET: A Review”, International Journal of Early Childhood Special Education (INT-JECSE)DOI:10.9756/INTJECSE/V14I5.305 ISSN: 1308-5581 Vol 14, Issue 05 2022, pp 2939-2949.
S. Sachdeva and P. Kaur, "Detection and analysis of Jellyfish attack in MANETs," 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, pp. 1-5, 2016.
S. Doss et al., "APD-JFAD: Accurate Prevention and Detection of Jelly Fish Attack in MANET," in IEEE Access, vol. 6, pp. 56954-56965, 2018.
J.Dromard, R. Khatoun, L.Khoukhi, “A watchdog extension scheme considering packet loss for a reputation system in wireless mesh network,” In: 20th International Conference on Telecommunications (ICT 2013). Casablanca, Morocco, pp 1–5, 2013.
Capkun S, Buttyán L, and Hubaux JP SECTOR “secure tracking of node encounters in multi-hop wireless networks” In: Proceedings of the 1st ACM workshop on Security of ad hoc and sensor networks
(in association with 10th ACM conference on computer and communications security) Fairfax, VA, United States, 2003.
Dias JA, Rodrigues JJ, Xia F, Mavromoustakis CX, “A cooperative watchdog system to detect misbehavior nodes in vehicular delay-tolerant networks” IEEE Trans Ind Electron, pp. 7929–7937,
2015.
Biswas J, Gupta A, and Singh D WADP, “a wormhole attack detection and prevention technique
in MANET using modified AODV routing protocol” In: Arya KV, Sunil Kumar (Eds) 9th international conference on industrial and information systems (ICIIS2014) IEEE, Piscataway, New Jersey, 2014.
Liu X, Chen S, Song W, “A design and implementation of watchdog based on observer pattern and finite state machine,” In: Proceedings of the 10th IEEE International Conference on
Reliability, Maintainability and Safety (ICRMS ’14), pp 407–411, 2014.
Patel MM, Aggarwal A, “Two phase wormhole detection approach for dynamic wireless sensor networks,” In Proceedings of the IEEE international conference on wireless communications, signal processing and networking (WiSPNET ’16) IEEE,Chennai, India, 2016.
Su MY WARP, “A wormhole-avoidance routing protocol by anomaly detection in mobile ad hoc networks”. Comput Secur, pp. 208–224, 2010.
Aad and J.P. Hubaux, E.W. Knightly, “Impact of Denial of Service Attacks on Ad Hoc Networks,”
IEEE/ACM Transactions on Networking, vol.16, pp.791- 802, Aug.2008.
Wazid, Mohammad & Katal, Avita & Goudar, R.H., “Cluster and super cluster based intrusion detection and prevention techniques for JellyFish Reorder Attack,” Proceedings of 2012 2nd IEEE International Conference on Parallel, Distributed and Grid Computing. Pp. 435-440, 2012
Wazid, M., Katal, A. Goudar, R. H., “Cluster and super cluster based intrusion detection and prevention techniques for JellyFish Reorder Attack,” in Proceedings of 2nd IEEE international conference on parallel, distributed and grid computing , pp. 435– 440, 2012.
M. Kaur, M. Rani and A. Nayyar, "A novel defense mechanism via Genetic Algorithm for counterfeiting and combating Jelly Fish attack in Mobile Ad-Hoc Networks," 5th International Conference -Confluence The Next Generation Information Technology Summit (Confluence), Noida, pp.359-364, 2014.
Jayasingh, Bipin & Swathi, “Novel Metric for Detection of Jellyfish Reorder Attack on Ad Hoc Network,” BVICAM's International Journal of Information Technology, 2010.
Ramesh, A. &Suruliandi, “A Performance analysis of encryption algorithms for Information Security,” pp. 840-844, 2013.
S. K. A. and Abha Jadaun. “Design and Performance Assessment of Light Weight Data Security System for Secure Data Transmission in IoT”, Journal of Network Security, 2021, Vol-9, Issue-1, PP: 29-41.
Pratiksha Mishra and S. K. A. “Design & Performance Assessment of Energy Efficient Routing Protocol Using Improved LEACH”, International Journal of Wireless Network Security, 2021, Vol-7, Issue-1, PP: 17-33.
S. K. A., Prakash Dangi and Pratiksha Mishra. Design and Comparison of LEACH and Improved Centralized LEACH in Wireless Sensor Network. IJRITCC 2021, 9, 34-39.
S. K. A., M. K. M, and P. Singh "A Security Approach to Manage a Smart City's Image Data on Cloud," AI-Centric Smart City Ecosystems: Technologies, Design and Implementation (1st ed.), PP: 68-82, (2022). CRC Press. https://doi.org/10.1201/9781003252542.
S. K. A. "A. Raj, V. Sharma, and V. Kumar.“Simulation and Analysis of Hand Gesture Recognition for Indian Sign Language Using CNN”." International Journal on Recent and Innovation Trends in Computing and Communication 10, no. 4 (2022): 10-14.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





