Analysis of Intrusions into Computer Systems using Honeypots
Keywords:
Honeypot, TPot, Web Security, Attacks, Cyber-criminalsAbstract
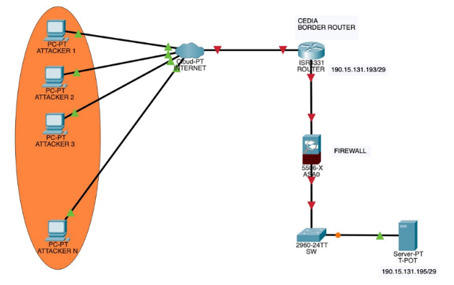
Among the different tools and techniques to detect, monitor and analyze the behavior of cybercriminals in a controlled environment is the use of Honeypots. This computer security technique consists of creating a trap or decoy that pretends to be a valuable target for cybercriminals, such as, for example, important data, applications or web servers, among others. Once the attacker enters this environment, it records all the activities and behaviors performed by them, this in turn, allows the detection and proactive response to future attacks. Likewise, they allow to reduce false positives and identify vulnerabilities of the systems. On the other hand, the implementation of these tools implies a potential risk, because they can be used by attackers to obtain information about the defenses of the institution or organization and, even more, if it is not installed correctly, leaving the system and sensitive data exposed. In this sense, there are many high and low interaction Honeypots, such as, for example, Honeyd, Dioneda, Capture-HPC, KFSensor, INetSim. Cowrie, Honeytrap, Amun, Glastopf, Contop, among others. Finally, T-Pot Honeypot is considered as a set of computers (All in one) containing both high and low interaction Honeypots, with a unique ability to customize and manage honeypots, that is, it is a powerful and effective tool in the fight against attackers and computer security threats. In addition, it allows the obtaining of behavioral data of cybercriminals to later determine patterns that allow improving Web Security.
Downloads
References
C. Martínez Santander, S. G. Yoo, and H. O. Moreno, “Analysis of traditional web security solutions and proposal of a web attacks cognitive patterns classifier architecture,” in Communications in Computer and Information Science, 2018, pp. 186–198. doi: 10.1007/978-3-030-00940-3_14.
M. Marydas and J. N. Varshapriya, “A Cloud based Honeynet System for Attack Detection using Machine Learning Techniques,” International Research Journal of Engineering and Technology, vol. 330, no. July, pp. 330–335, 2019.
C. I. Rene and J. Abdullah, “Malicious Code Intrusion Detection using Machine Learning And Indicators of Compromise,” Ijcsis, vol. 15, no. September, pp. 160–171, 2017, [Online]. Available: http://www.academia.edu/download/55691451/Journal_of_Computer_Science_IJCSIS_September_2017_Full_Volume.pdf#page=173
J. Martinez, “The evolution from Traditional to Intelligent Web Security : Systematic Literature Review,” 2020.
R. G. T. Thilagam, “A Review on the Effectiveness of Machine Learning and Deep Learning Algorithms for Cyber Security,” Archives of Computational Methods in Engineering, no. 0123456789, 2020, doi: 10.1007/s11831-020-09478-2.
S. Mazumdar and J. Wang, Guide to Vulnerability Analysis for Computer Networks and Systems, no. September. 2018. doi: 10.1007/978-3-319-92624-7.
I. H. Sarker, A. S. M. Kayes, S. Badsha, H. Alqahtani, P. Watters, and A. Ng, “Cybersecurity data science: an overview from machine learning perspective,” J Big Data, vol. 7, no. 1, 2020, doi: 10.1186/s40537-020-00318-5.
G. E. Rodríguez, J. G. Torres, P. Flores, and D. E. Benavides, “Cross-site scripting (XSS) attacks and mitigation: A survey,” Computer Networks, vol. 166, p. 106960, 2020, doi: 10.1016/j.comnet.2019.106960.
R. Hofstede, M. Jonker, A. Sperotto, and A. Pras, “Flow-Based Web Application Brute-Force Attack and Compromise Detection,” Journal of Network and Systems Management, vol. 25, no. 4, pp. 735–758, Oct. 2017, doi: 10.1007/s10922-017-9421-4.
Itu, “Global Cybersecurity Index 2020 Measuring commitment to cybersecurity Acknowledgements.”
Telecommunications Regulation and Control Agency, "EC-2022-031_RANSOMWARE-ELBIE_V1," Quito, 2022.
Ministry of Telecommunications and Information Society, "CIBERSEGURIDAD DEL ECUADOR," 2022. Accessed: Apr. 24, 2023. [Online]. Available: https://asobanca.org.ec/wp-content/uploads/2022/08/ESTRATEGIA-NACIONAL-DE-CIBERSEGURIDAD-DEL-ECUADOR-2022481.pdf
Flores I. and Quintana J., "SYSTEM OF DETECTION OF COMPUTER ATTACKS TO ENTERPRISE DATA NETWORKS SUPPORTED IN HONEYPOTS," Repositorio Universidad de Cartagena, pp. 1–95, 2018.
C. Huang, J. Han, X. Zhang, and J. Liu, “Automatic identification of honeypot server using machine learning techniques,” Security and Communication Networks, vol. 2019, 2019, doi: 10.1155/2019/2627608.
Dimitrios Pliatsios, Panagiotis Sarigiannidis, Thanasis Liati fis, Konstantinos Rompolos, and Ilias Siniosoglou, “A Novel and Interactive Industrial Control System Honeypot for Critical Smart Grid Infrastructure,” in IEEE COMMUNICATIONS SOCIETY, INSTITUTR OF ELECRICAL AND ELECTRONICS ENGENEERS, 2019, pp. 1–6.
Ridho Maulana Ari fianto, Parman Sukarno, and Erwid Musthofa Jadied, “An SSH Honeypot Architecture Using Port Knocking and Intrusion Detection System,” in 2018 6th International Conference on Information and Communication Technology (ICoICT), 2018, pp. 409–415.
W. Ruiz Martínez, "Analysis of Machine Learning techniques applied to computer cybersecurity to improve the detection of intrusions and anomalous behaviors on the Web."
L. Dirección et al. , "CUADERNOS DE LA GUARDIA CIVIL," REVISTA DE SEGURIDAD PÚBLICA 3a ÉPOCA EDITOR-IN-CHIEF EDITOR-IN-CHIEF EDITORIAL BOARD, [Online]. Available: http://publicacionesoficiales.boe.es/
M. R. Ogiela and L. Ogiela, “Security of Cognitive Information Systems,” Springer, 2013, pp. 427–433.
R. Greenstadt and J. Beal, “Cognitive security for personal devices,” ACM, 2008, pp. 27–30.
W. Kinsner, “Towards cognitive security systems,” in 2012 IEEE 11th International Conference on Cognitive Informatics and Cognitive Computing, IEEE, Aug. 2012, pp. 539–539. doi: 10.1109/ICCI-CC.2012.6311207.
M. N. Hoda, I. Bharati Vidyapeeth’s Institute of Computer Applications and Management (New Delhi, Institute of Electrical and Electronics Engineers. Delhi Section, and I. International Conference on Computing for Sustainable Global Development (3rd : 2016 : New Delhi, “Honeypot-Based Intrusion Detection System: A Performance Analysis,” Honeypot-Based Intrusion Detection System: A Performance Analysis, vol. 16, no. 18, pp. 3947–3951, 2016.
N. Eliot, D. Kendall, and M. Brockway, “A flexible laboratory environment supporting honeypot deployment for teaching real-world cybersecurity skills,” IEEE Access, vol. 6, pp. 34884–34895, Jun. 2018, doi: 10.1109/ACCESS.2018.2850839.
X. Jiang, D. Xu, and Y.-M. Wang, “Collapsar: A VM-Based Honeyfarm and Reverse Honeyfarm Architecture for Network Attack Capture and Detention.”
V. Nicomette et al. , “Set-up and deployment of a high-interaction honeypot: experiment and lessons learned Set-up and deployment of a high-interaction honeypot: experiment and lessons learned Set-up and deployment of a high-interaction honeypot: Experiment and lessons learned,” Journal in Computer Virology, vol. 7, no. 2, 2011, doi: 10.1007/s11416-010-0144-2ï.
Iqra Khan, Hanif Durad, and Masoom Alam, Data Analytics Layer For high-interaction Honeypots. 2019.
I. M. M. Matin and B. Rahardjo, “Malware Detection Using Honeypot and Machine Learning,” 2019 7th International Conference on Cyber and IT Service Management, CITSM 2019, 2019, doi: 10.1109/CITSM47753.2019.8965419.
B. Alhan, S. Gönen, G. Karacayilmaz, M. A. Barişkan, and E. N. Yilmaz, “Real-Time Cyber Attack Detection Over HoneyPi Using Machine Learning,” Tehnicki Vjesnik, vol. 29, no. 4, pp. 1394–1401, 2022, doi: 10.17559/TV-20210523121614.
S. Lee, A. Abdullah, N. Z. Jhanjhi, and S. H. Kok, “Honeypot Coupled Machine Learning Model for Botnet Detection and Classification in IoT Smart Factory – An Investigation,” MATEC Web of Conferences, vol. 335, p. 04003, 2021, doi: 10.1051/matecconf/202133504003.
G. K. Sadasivam, C. Hota, and B. Anand, “Detection of Severe SSH Attacks Using Honeypot Servers and Machine Learning Techniques,” Software Networking, vol. 2017, no. 1, pp. 79–100, 2017, doi: 10.13052/jsn2445-9739.2017.005.
V. Mehta, P. Bahadur, M. Kapoor, P. Singh, and S. Rajpoot, “Threat prediction using honeypot and machine learning,” 2015 1st International Conference on Futuristic Trends in Computational Analysis and Knowledge Management, ABLAZE 2015, pp. 278–282, 2015, doi: 10.1109/ABLAZE.2015.7155011.
R. Vishwakarma and A. K. Jain, “A honeypot with machine learning based detection framework for defending IoT based botnet DDoS attacks,” Proceedings of the International Conference on Trends in Electronics and Informatics, ICOEI 2019, no. Icoei, pp. 1019–1024, 2019, doi: 10.1109/ICOEI.2019.8862720.
S. Son and Y. Kwon, “Performance of ELK Stack and Commercial System in Security Log Analysis,” in IEEE 13th Malaysia International Conference on Communications (MICC), The Puteri pacific and Johor Bahru, Eds., Malaysia, 2017, pp. 187–190.
F. Abdou, M. L. Salihi, and M. F. Nanne, “Toward a Secure ELK Stack.” [Online]. Available: https://sites.google.com/site/ijcsis/
T. Prakash, M. Kakkar, and K. Patel, “Geo-Identification of Web Users through Logs using ELK Stack,” in 2016 6th International conference- cloud system and Big Data Engineering, IEEE, 2016, pp. 606–610.
L. Chen, J. Liu, M. Xian, and H. Wang, “Docker container log collection and analysis system based on ELK,” in Proceedings - 2020 International Conference on Computer Information and Big Data Applications, CIBDA 2020, Institute of Electrical and Electronics Engineers Inc., Apr. 2020, pp. 317–320. doi: 10.1109/CIBDA50819.2020.00078.
S. Back, J. Laprade, L. Shehadeh, and M. Kim, “Youth hackers and adult hackers in south korea: An application of cybercriminal profiling,” in Proceedings - 4th IEEE European Symposium on Security and Privacy Workshops, EUROS and PW 2019, Institute of Electrical and Electronics Engineers Inc., Jun. 2019, pp. 410–413. doi: 10.1109/EuroSPW.2019.00052.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





