A Hybrid Model for Real-Time Docker Container Threat Detection and Vulnerability Analysis
Keywords:
Docker, Container, Threat, Cloud, VulnerabilityAbstract
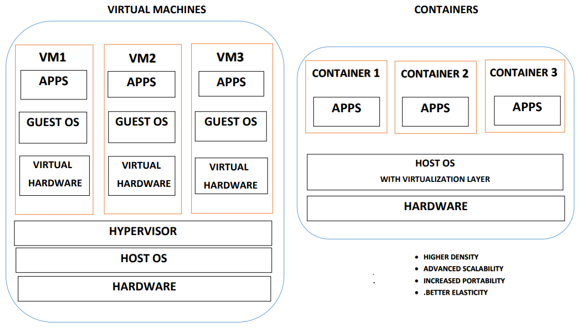
Computer attacks are becoming more sophisticated and difficult to detect, the large volume of information in security records generated by network devices, servers and applications does not allow an adequate analysis due to the complexity of the data produced, and this leads to not taking measures timely in the event of gaps or security incidents. In spite of the fact that containers are widely accepted as a standardized way of deploying micro services and play a vital role in emerging areas of cloud computing such as service meshes. A survey has revealed that container security is the common concern and barrier to adoption for most organizations. This paper aims to conduct a review of the existing literature on container security and solutions. The time that elapses between the occurrences of an incident until its discovery should be as short as possible in order to determine the scope of the incident and compromised systems in a timely and efficient manner. The main objective of this paper is to deploy a solution using open source tools in a Docker container based environment to allow analysis of security anomalies. Therefore, relevant information must be collected, processed, and presented through dashboard displays in order to identify or detect security incidents in real time in a timely manner.
Downloads
References
Jiang, Y., Liu, W., Shi, X., Qiang, W. (2021). Optimizing the copy-on-write mechanism of Docker by dynamic prefetching. Tsinghua Science and Technology, 26(3), 266–274.
Kwon, S., Lee, J.-H. (2020). Divds: Docker image vulnerability diagnostic system. IEEE Access, 8, 42666–42673.
Zhao, N., Tarasov, V., Albahar, H., Anwar, A., Rupprecht, L., et al. (2021). Large-scale analysis of docker images and performance implications for container storage systems. IEEE Transactions on Parallel and Distributed Systems, 32(4), 918–930.
Xie, Y., Jin, M., Zou, Z., Xu, G., Feng, D., et al. (2020). Real-time prediction of docker container resource load based on a hybrid model of arima and triple exponential smoothing. IEEE Transactions on Cloud Computing, 1–1.
Jin, H., Wang, Y., Wang, Q., Liu, J., Wang, S., et al. (2019). Architecture modelling and task scheduling of an integrated parallel cnc system in docker containers based on colored petri nets. IEEE Access, 7, 47535–47549.
Divya, V., Sri, R. L. (2021). Docker-based intelligent fall detection using edge-fog cloud infrastructure. IEEE Internet of Things Journal, 8(10), 8133–8144.
Melo, L., Wiese, I., d.Amorim, M. (2021). Using docker to assist q amp;a forum users. IEEE Transactions on Software Engineering, 47(11), 2563–2574.
Sollfrank, M., Loch, F., Denteneer, S., Vogel-Heuser, B. (2021). Evaluating docker for lightweight virtualization of distributed and time-sensitive applications in industrial automation. IEEE Transactions on Industrial Informatics, 17(5), 3566–3576.
Ma, L., Yi, S., Carter, N., Li, Q. (2019). Efficient live migration of edge services leveraging container layered storage. IEEE Transactions on Mobile Computing, 18(9), 2020–2033.
Zou, Z., Xie, Y., Huang, K., Xu, G., Feng, D., et al. (2019). A docker container anomaly monitoring system based on optimized isolation forest. IEEE Transactions on Cloud Computing, 1–1.
Lu, Z., Xu, J., Wu, Y., Wang, T., Huang, T. (2019). An empirical case study on the temporary file smell in dockerfiles. IEEE Access, 7, 63650–63659.
Sami, H., Mourad, A., El-Hajj, W. (2020). Vehicular-obus-as-on-demand-fogs: Resource and context aware deployment of containerized micro-services. IEEE/ACM Transactions on Networking, 28(2), 778–790.
Diekmann, C., Naab, J., Korsten, A., Carle, G. (2019). Agile network access control in the container age. IEEE Transactions on Network and Service Management, 16(1), 41–55.
Sairam, R., Bhunia, S. S., Thangavelu, V., Gurusamy, M. (2019). Netra: Enhancing iot security using nfv-based edge traffic analysis. IEEE Sensors Journal, 19(12), 4660–4671.
Wu, Y., Zhang, Y., Wang, T., Wang, H. (2020). Characterizing the occurrence of dockerfile smells in open-source software: An empirical study. IEEE Access, 8, 34127–34139.
Bellavista, P., Corradi, A., Foschini, L., Scotece, D. (2019). Differentiated service/data migration for edge services leveraging container characteristics. IEEE Access, 7, 139746–139758.
Mahmud, R., Toosi, A. N. (2021). Con-pi: A distributed container-based edge and fog computing framework. IEEE Internet of Things Journal, 1–1.
Kim, T., Al-Tarazi, M., Lin, J.-W., Choi, W. (2021). Optimal container migration for mobile edge computing: Algorithm, system design and implementation. IEEE Access, 1–1.
Cai, L., Qi, Y., Wei, W., Li, J. (2019). Improving resource usages of containers through auto-tuning container resource parameters. IEEE Access, 7, 108530–108541.
Tsung, C.-K., Hsieh, H.-Y., Yang, C.-T. (2019). An implementation of scalable high throughput data platform for logging semiconductor testing results. IEEE Access, 7, 26497–26506.
Cinque, M., Della Corte, R., Pecchia, A. (2019). Microservices monitoring with event logs and black box execution tracing. IEEE Transactions on Services Computing, 1–1.
Jimenez, L. L., Schelen, O. (2020). Hydra: Decentralized location-aware orchestration of containerized applications. IEEE Transactions on Cloud Computing, 1–1.
Karn, R. R., Kudva, P., Huang, H., Suneja, S., Elfadel, I. M. (2021). Cryptomining detection in container clouds using system calls and explainable machine learning. IEEE Transactions on Parallel and Distributed Systems, 32(3), 674–691.
Nakata, R., Otsuka, A. (2021). Cyexec*: A high-performance container-based cyber range with scenario randomization. IEEE Access, 9, 109095–109114.
Ramanathan, S., Kondepu, K., Razo, M., Tacca, M., Valcarenghi, L., et al. (2021). Live migration of virtual machine and container based mobile core network components: A comprehensive study. IEEE Access, 9, 105082–105100.
Karn, R. R., Kudva, P., Elfadel, I. A. M. (2019). Dynamic autoselection and autotuning of machine learning models for cloud network analytics. IEEE Transactions on Parallel and Distributed Systems, 30(5), 1052–1064.
Epiphaniou, G., Pillai, P., Bottarelli, M., Al-Khateeb, H., Hammoudesh, M., et al. (2020). Electronic regulation of data sharing and processing using smart ledger technologies for supply-chain security. IEEE Transactions on Engineering Management, 67(4), 1059–1073.
Sultan, S., Ahmad, I., Dimitriou, T. (2019). Container security: Issues, challenges, and the road ahead. IEEE Access, 7, 52976–52996.
Xu, R., Jin, W., Kim, D. (2021). Enhanced service framework based on microservice management and client support provider for efficient user experiment in edge computing environment. IEEE Access, 9, 110683–110694.
Souquet, L., Talbi, E. G., Nakib, A. (2020). Fractal decomposition approach for continuous multiobjective optimization problems. IEEE Access, 8, 167604–167619.
Sami, H., Mourad, A. (2020). Dynamic on-demand fog formation offering on-the-fly iot service deployment. IEEE Transactions on Network and Service Management, 17(2), 1026–1039.
Cui, H., Zhou, Y., Wang, C., Wang, X., Du, Y., et al. (2021). Ppsb: An open and flexible platform for privacy-preserving safe browsing. IEEE Transactions on Dependable and Secure Computing, 18(4), 1762–1778.
Kafle, V. P., Muktadir, A. H. A. (2020). Intelligent and agile control of edge resources for latencysensitive iot services. IEEE Access, 8, 207991–208002.
Kim, A., Park, M., Lee, D. H. (2020). Ai-ids: Application of deep learning to real-time web intrusion detection. IEEE Access, 8, 70245–70261.
Cai, B., Li, K., Laiping, Z., Zhang, R. (2020). Less provisioning: A hybrid resource scaling engine for long-running services with tail latency guarantees. IEEE Transactions on Cloud Computing, 1–1.
Vedant Bhatt, Harvinder Singh Diwan, S. K. A., Yashika Saini (2021), Empowering ML Work-Flow with DevOps within Micro Service Architecture and Deploying A Hybrid-Multi Cloud, Maintaining CI/CD Pipeline: An Open Shift Orchestration of ML-OPS. International Journal of Contemporary Architecture The New ARCH, e-ISSN: 2198-7688, Vol. 8 No. 2 (2021): Vol. 8 No. 2.
Ashutosh Kumar & S. K. A. (2018). Implementation of new Cryptographic Encryption Approach for Trust as a Service (TAAS) in Cloud Environment. International Journal of Computer Application (2250-1797) Issue 8 Volume 4, https://dx.doi.org/10.26808/rs.ca.i8v4.03
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





