Enhanced Security and User Friendliness of Generated Shares Using Combination of Block Based Progressive Visual Secret Sharing Scheme and Pixel Value Differencing
Keywords:
User friendly share, meaningful share, Progressive Visual Secret Sharing (PVSS) scheme, Block based Progressive Visual Secret Sharing (BPVSS) scheme, visual cryptography, Pixel Value Differencing (PVDAbstract
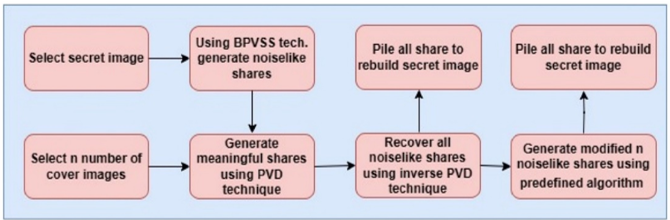
In order to securely transfer confidential photos among participants, visual secret sharing (VSS) techniques are often used. Traditional VSS methods, however, have drawbacks in terms of security and usability. The suggested research has been investigating ways to provide meaningful shares that are user-friendly in order to solve these limitations. One approach combines a least significant bit (LSB)-based mechanism with a block-based progressive visual secret sharing system. The user experience might be negatively impacted by the poor visual quality of shares produced using this technique.
This research seeks to improve user-friendly shares' visual attractiveness by offering a unique way to address the issue of poor visual quality in user-friendly shares. The recommended solution combines the pixel value differencing method with a block-based progressive visual secret sharing system. By using this strategy, the shares' visual quality is considerably enhanced, producing a result that is more visually pleasing and satisfying for the participants.
The performance of suggested system is assessed using standard performance measure metrics. The recommended technique outperforms other ways in comparison to the findings, which were compared and contrasted.
Downloads
References
M. Naor and A. Shamir, “Visual cryptography,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 950, pp. 1–12, 1994, doi: 10.1007/BFB0053419.
W. P. Fang and J. C. Lin, “Progressive viewing and sharing of sensitive images,” Pattern Recognit. Image Anal., vol. 16, no. 4, pp. 632–636, 2006, doi: 10.1134/S1054661806040080.
W. P. Fang, “Friendly progressive visual secret sharing,” Pattern Recognit., vol. 41, no. 4, pp. 1410–1414, 2008, doi: 10.1016/j.patcog.2007.09.004.
R. Wang, “Region Incrementing Visual Cryptography,” IEEE Signal Process. Lett., vol. 16, no. 8, pp. 659–662, 2009, doi: 10.1109/LSP.2009.2021334.
S.-K. Chen, “Friendly progressive visual secret sharing using generalized random grids,” Opt. Eng., vol. 48, no. 11, p. 117001, 2009, doi: 10.1117/1.3262345.
Y. C. Hou and Z. Y. Quan, “Progressive visual cryptography with unexpanded shares,” IEEE Trans. Circuits Syst. Video Technol., vol. 21, no. 11, pp. 1760–1764, 2011, doi: 10.1109/TCSVT.2011.2106291.
A. Mohanasundaram and S. K. Aruna, “International Journal of Intelligent Networks Improved Henon Chaotic Map-based Progressive Block-based visual cryptography strategy for securing sensitive data in a cloud EHR system,” Int. J. Intell. Networks, vol. 3, no. August, pp. 109–112, 2022, doi: 10.1016/j.ijin.2022.08.004.
R. Z. Wang, Y. K. Lee, S. Y. Huang, and T. L. Chia, “Multilevel visual secret sharing,” Second Int. Conf. Innov. Comput. Inf. Control. ICICIC 2007, pp. 283–286, 2007, doi: 10.1109/ICICIC.2007.401.
Y. C. Hou, Z. Y. Quan, C. F. Tsai, and A. Y. Tseng, “Block-based progressive visual secret sharing,” Inf. Sci. (Ny)., vol. 233, pp. 290–304, 2013, doi: 10.1016/j.ins.2013.01.006.
N. C. Mhala, R. Jamal, and A. R. Pais, “Randomised visual secret sharing scheme for grey-scale and colour images,” IET Image Process., vol. 12, no. 3, pp. 422–431, 2018, doi: 10.1049/iet-ipr.2017.0759.
V. V. Panchbhai and S. W. Varade, “Hybrid Approach to Enhance Security and Friendliness of Visual Secret Sharing Scheme,” Int. Conf. Emerg. Trends Eng. Technol. ICETET, vol. 2022-April, 2022, doi: 10.1109/ICETET-SIP-2254415.2022.9791815.
F. S. Abas and R. Arulmurugan, “Radix Trie improved Nahrain chaotic map-based image encryption model for effective image encryption process,” Int. J. Intell. Networks, vol. 3, no. August, pp. 102–108, 2022, doi: 10.1016/j.ijin.2022.08.002.
F. Thabit, O. Can, S. Alhomdy, G. H. Al-Gaphari, and S. Jagtap, “A Novel Effective Lightweight Homomorphic Cryptographic Algorithm for data security in cloud computing,” Int. J. Intell. Networks, vol. 3, no. July 2021, pp. 16–30, 2022, doi: 10.1016/j.ijin.2022.04.001.
C. P. Sumathi, T. Santanam, and G. Umamaheswari, “A Study of Various Steganographic Techniques Used for Information Hiding,” Int. J. Comput. Sci. Eng. Surv., vol. 4, no. 6, pp. 9–25, 2013, doi: 10.5121/ijcses.2013.4602.
N. Kaur and S. Behal, “A Survey on various types of Steganography and Analysis of Hiding Techniques,” Int. J. Eng. Trends Technol., vol. 11, no. 8, pp. 388–392, 2014, doi: 10.14445/22315381/ijett-v11p276.
I. J. Kadhim, P. Premaratne, P. J. Vial, and B. Halloran, “Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research,” Neurocomputing, vol. 335, pp. 299–326, 2019, doi: 10.1016/j.neucom.2018.06.075.
J. K. Mandal and S. Ghatak, “Secret image / message transmission through meaningful shares using (2, 2) visual cryptography (SITMSVC),” Int. Conf. Recent Trends Inf. Technol. ICRTIT 2011, pp. 263–268, 2011, doi: 10.1109/ICRTIT.2011.5972344.
K. S. Seethalakshmi, B. A. Usha, and K. N. Sangeetha, “Security enhancement in image steganography using neural networks and visual cryptography,” 2016 Int. Conf. Comput. Syst. Inf. Technol. Sustain. Solut. CSITSS 2016, pp. 396–403, 2016, doi: 10.1109/CSITSS.2016.7779393.
S. H. Murad, A. M. Gody, and T. M. Barakat, “Enhanced Security of Symmetric Encryption Using Combination of Steganography with Visual Cryptography,” Int. J. Eng. Trends Technol., vol. 65, no. 3, pp. 149–154, 2018, doi: 10.14445/22315381/ijett-v65p227.
M. A. Islam, M. A. A. K. Riad, and T. S. Pias, “Enhancing Security of Image Steganography Using Visual Cryptography,” Int. Conf. Robot. Electr. Signal Process. Tech., pp. 694–698, 2021, doi: 10.1109/ICREST51555.2021.9331225.
S. Chavan and Y. B. Gurav, “Lossless Tagged Visual Cryptography Scheme Using Bit Plane Slicing for Image Processing,” Proc. Int. Conf. Inven. Res. Comput. Appl. ICIRCA 2018, no. Icirca, pp. 1168–1172, 2018, doi: 10.1109/ICIRCA.2018.8596778.
S. Roy and P. Venkateswaran, “Online payment system using steganography and visual cryptography,” in 2014 IEEE Students’ Conference on Electrical, Electronics and Computer Science, 2014, pp. 1–5, doi: 10.1109/SCEECS.2014.6804449.
V. Lokeswara and T. Anusha, “Combine Use of Steganography and Visual Cryptography for Online Payment System,” Int. J. Comput. Appl., vol. 124, no. 6, pp. 7–11, 2015, doi: 10.5120/ijca2015905494.
S. S. More, A. Mudrale, and S. Raut, “Secure Transaction System using Collective Approach of Steganography and Visual Cryptography,” 2018 Int. Conf. Smart City Emerg. Technol. ICSCET 2018, pp. 1–6, 2018, doi: 10.1109/ICSCET.2018.8537262.
M. Mostaghim and R. Boostani, “CVC: Chaotic visual cryptography to enhance steganography,” 2014 11th Int. ISC Conf. Inf. Secur. Cryptology, Isc. 2014, pp. 44–48, 2014, doi: 10.1109/ISCISC.2014.6994020.
Y. K. Meghrajani and H. S. Mazumdar, “Hiding secret message using visual cryptography in steganography,” 12th IEEE Int. Conf. Electron. Energy, Environ. Commun. Comput. Control (E3-C3), INDICON 2015, pp. 1–5, 2016, doi: 10.1109/INDICON.2015.7443677.
A. K. Shukla, A. Singh, B. Singh, and A. Kumar, “A Secure and High-Capacity Data-Hiding Method Using Compression, Encryption and Optimized Pixel Value Differencing,” IEEE Access, vol. 6, pp. 51130–51139, 2018, doi: 10.1109/ACCESS.2018.2868192.
“The USC-SIPI Image Database.” https://sipi.usc.edu/database/database.php?volume= misc? (accessed May 20, 2020).
Gonzalez and Woods, “DIP3/e—Book Images Downloads,” ImageProcessingPlace.com. https://www.imageprocessingplace.com/DIP-3E/dip3e_book_images_downloads.htm (accessed Jul. 05, 2021).
J. Li and J. Z. Wang, “Automatic linguistic indexing of pictures by a statistical modeling approach,” IEEE Trans. Pattern Anal. Mach. Intell., vol. 25, no. 9, pp. 1075–1088, 2003, doi: 10.1109/TPAMI.2003.1227984.
V. V. Panchbhai and S. W. Varade, “A Review on Visual Secret Sharing Schemes for Binary, Gray & Color Image,” Biosci. Biotechnol. Res. Commun., vol. 13, no. 14, pp. 268–272, 2020, doi: 10.21786/bbrc/13.14/63.
N. Ahmed, H. M. Shahzad Asif, and G. Saleem, “A Benchmark for Performance Evaluation and Security Assessment of Image Encryption Schemes,” Int. J. Comput. Netw. Inf. Secur., vol. 8, no. 12, pp. 28–29, 2016, doi: 10.5815/ijcnis.2016.12.03.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





