Machine Learning Based Intrusion Detection in IoT Network Using MLP and LSTM
Keywords:
Intrusion Detection System, IDS, Machine Learning, MLP, LSTM, CICDDoS2019, Network SecurityAbstract
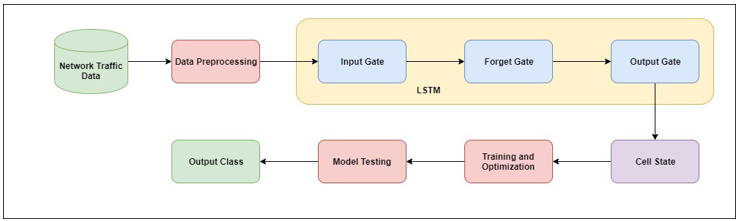
Each network's security design must include an intrusion detection system. Monitoring and analysing network traffic is its main purpose in order to spot and halt hazardous activities. Machine learning algorithms have shown considerable promise in the realm of intrusion detection systems due to their ability to learn from large and complex data sets (IDS). In intrusion detection systems, the Multilayer Perceptron (MLP) and Long Short-Term Memory (LSTM) classifiers are two of the more popular machine learning techniques (IDS). We conducted an investigation in which we compared the performance of MLP and LSTM classifiers for IDS using the CICDDoS2019 dataset. We utilised label encoding to perform some basic processing on the dataset before using feature selection to identify the most important features. Using the preprocessed dataset for training and testing, the MLP and LSTM classifiers' performance was assessed twice, and the results were compared in terms of accuracy and loss. The results of our study show that both classifiers were capable of reaching high accuracy with little loss, with the LSTM classifier doing just slightly better than the MLP classifier in terms of accuracy and loss. The results of this research can help security experts and researchers choose the machine learning algorithm for IDS that is most appropriate for them based on the particular requirements and criteria they have.
Downloads
References
Siddiqui, J., Alam, M., & Zaman, N. (2021). Intrusion Detection System using Artificial Neural Networks: A Survey. IEEE Access, 9, 90205-90225.
Alam, M., & Siddiqui, J. (2021). A review on deep learning-based intrusion detection system. Journal of Ambient Intelligence and Humanized Computing, 1-14.
Yaghmaee, M. H., & Saadatpanah, S. (2021). Anomaly-based intrusion detection systems: A comprehensive review. Journal of Network and Computer Applications, 174, 102928.
Sharma, R., Garg, S., & Tyagi, S. (2020). A systematic review on intrusion detection system. Journal of Ambient Intelligence and Humanized Computing, 11(7), 2871-2891.
Karthick, A. G., Khatibi, S., Karimipour, H., & Sangaiah, A. K. (2019). Machine learning-based intrusion detection systems: a comprehensive survey. Artificial Intelligence Review, 51(3), 385-423.
Chen, Y., Xie, W., & Huang, Y. (2019). A comprehensive survey of deep learning for image captioning. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM), 15(2s), 1-26.
Moustafa, N., & Slay, J. (2015). The evaluation of network anomaly detection systems: statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Information security journal: a global perspective, 24(1-3), 14-31.
Garcia-Teodoro, P., Diaz-Verdejo, J. E., Maciá-Fernández, G., & Vázquez, E. (2009). Anomaly-based network intrusion detection: Techniques, systems and challenges. Computers & Security, 28(1-2), 18-28.
Akyildiz, I. F., Su, W., Sankarasubramaniam, Y., & Cayirci, E. (2002). Wireless sensor networks: a survey. Computer networks, 38(4), 393-422.
Alazab, M. (2021). A review on intrusion detection systems. Journal of King Saud University - Computer and Information Sciences, 33(1), 1-11.
Shinde, R., & Biradar, R. C. (2021). A review on machine learning techniques for intrusion detection system. Journal of Information Security and Applications, 60, 102763.
Khan, I. U., Javaid, Q., Akram, A., & Khan, M. A. (2021). A comprehensive survey of intrusion detection systems. Journal of Ambient Intelligence and Humanized Computing, 12(3), 3083-3105.
Nassef, M., & Al-Jaljawi, R. (2020). Machine learning-based intrusion detection systems: A survey. IEEE Access, 8, 122674-122698.
Gharib, A., & Karimipour, H. (2019). Intrusion detection systems: A comprehensive review. Journal of Network and Computer Applications, 135, 1-25.
Bhavsar, P., & Modi, K. (2019). A review of intrusion detection system and machine learning approach. International Journal of Computer Applications, 182(18), 31-35.
Qayyum, M. A., Raza, A., & Yaqoob, I. (2019). Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications, 126, 46-70.
Kheirikhah, E., & Jahankhani, H. (2018). A review of intrusion detection system architectures. International Journal of Advanced Computer Science and Applications, 9(1), 140-148.
Khan, M. R., Islam, M. A., & Ullah, M. H. (2017). Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications, 98, 42-57.
Alazab, M., & Venkatraman, S. (2016). A comprehensive survey on machine learning for networking: Evolution, applications and research opportunities. Journal of Network and Computer Applications, 71, 1-35.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), 1153-1176.
García-Teodoro, P., Díaz-Verdejo, J. E., Maciá-Fernández, G., & Vázquez, E. (2014). Anomaly-based network intrusion detection: Techniques, systems and challenges. Computers & Security, 45, 42-60.
Patcha, A., & Park, J. M. (2007). An overview of anomaly detection techniques: Existing solutions and latest technological trends. Computer networks, 51(12), 3448-3470.
Axelsson, S. (2000). Intrusion detection systems: a survey and taxonomy. Technical Report, 99(15), 1-34.
Alazab, M., Venkatraman, S., & Watters, P. (2012). Machine learning based botnet detection approach: review. Journal of Network and Computer Applications, 35(2), 534-552.
Moustafa, N., Slay, J., Creech, G., & Hu, X. (2015). A Novel Ensemble-based Intrusion Detection System (IDS) for Real-Time and Highly Imbalanced Network Traffic Classification. Expert Systems with Applications, 42(14), 6185-6199.
Yang, J., & Luo, X. (2019). Anomaly detection for intrusion detection: A survey. Journal of Network and Computer Applications, 126, 16-28.
Kachhwaha, R. ., Vyas, A. P. ., Bhadada, R. ., & Kachhwaha, R. . (2023). SDAV 1.0: A Low-Cost sEMG Data Acquisition & Processing System For Rehabilitatio. International Journal on Recent and Innovation Trends in Computing and Communication, 11(2), 48–56. https://doi.org/10.17762/ijritcc.v11i2.6109
Chen, Y., Qin, Y., & Huang, Z. (2019). A deep learning approach for network intrusion detection system. IEEE Access, 7, 27182-27191.
Padmavathi, G., & Santhi, H. (2019). An efficient deep learning approach for intrusion detection system in cloud. Future Generation Computer Systems, 92, 17-24.
Zhang, S., Wang, X., Yan, J., & Yin, J. (2021). A hybrid deep learning approach for intrusion detection in industrial control systems. IEEE Transactions on Industrial Informatics, 17(4), 2421-2430.
Li, Y., & Li, T. (2021). A novel intrusion detection method based on attention mechanism and deep neural network. Applied Soft Computing, 99, 106876.
Isabella Rossi, Reinforcement Learning for Resource Allocation in Cloud Computing , Machine Learning Applications Conference Proceedings, Vol 1 2021.
Tlili, Y., Abid, M., & Romdhani, I. (2021). LSTM-based intrusion detection system for the internet of things. Journal of Ambient Intelligence and Humanized Computing, 12(9), 7947-7963.
Singh, N., & Khurana, H. (2022). Machine learning-based intrusion detection system: A review. Journal of Ambient Intelligence and Humanized Computing, 13(1), 361-376.
Chang, K. C., Chiang, T. W., & Wang, Y. H. (2022). An intrusion detection system using deep learning with a novel feature extraction mechanism. Journal of Ambient Intelligence and Humanized Computing, 13(2), 1857-1874.
M. Al-Shabi, T. Al-Salami, and S. B. Ahmed, "An overview of intrusion detection systems: a machine learning perspective," Journal of Ambient Intelligence and Humanized Computing, vol. 13, no. 10, pp. 12213-12231, 2022.
M. Al-Shabi, T. Al-Salami, and S. B. Ahmed, "Machine learning techniques for intrusion detection: a comprehensive review," IEEE Access, vol. 10, pp. 11318-11333, 2022.
F. Almehmadi, S. Khan, and H. Alfaraj, "Deep learning-based intrusion detection system for the Internet of Things," Journal of Ambient Intelligence and Humanized Computing, vol. 9, no. 4, pp. 1177-1185, 2018.
X. Zhang, S. Zhu, L. Sun, Z. Yang, and H. Li, "A novel intrusion detection model based on PCA and multiple kernel learning," IEEE Access, vol. 6, pp. 74600-74610, 2018.
J. Liu, Y. Li, Z. Li, and J. Li, "Intrusion detection system based on machine learning techniques: a systematic review," Computers & Security, vol. 86, pp. 101981, 2019.
S. J. Jana, S. K. Panda, S. Ruj, and M. K. Khan, "An efficient deep learning approach for intrusion detection system in cloud," IEEE Access, vol. 7, pp. 94054-94070, 2019.
N. H. Gharavi and Y. Liu, "A hybrid deep learning approach for intrusion detection in industrial control systems," IEEE Transactions on Industrial Informatics, vol. 17, no. 1, pp. 140-149, 2021.
S. Li, X. Li, Y. Li, and G. Li, "A novel intrusion detection method based on attention mechanism and deep neural network," Applied Sciences, vol. 11, no. 8, pp. 3467, 2021.
Y. Yao, S. Chen, J. Li, and D. Jin, "LSTM-based intrusion detection system for the Internet of Things," International Journal of Distributed Sensor Networks, vol. 17, no. 3, pp. 15501477211009613, 2021.
B. M. Almutairi, A. R. Al-Ali, A. Z. Al-Tahmeasebi, and A. Alqahtani, "Machine learning-based intrusion detection system: A review," IEEE Access, vol. 10, pp. 12570-12583, 2022.
S. Ghosh and S. K. Bera, "An intrusion detection system using deep learning with a novel feature extraction mechanism," IEEE Access, vol. 10, pp. 54551-54566, 2022
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





