A Novel and Dynamic S-Box for Improving the Security of Audio and Video for Various Crypto - Applications
Keywords:
Dynamic DES, Non-Linearity, Balance, S-boxes, Linear Cryptanalysis, Differential CryptanalysisAbstract
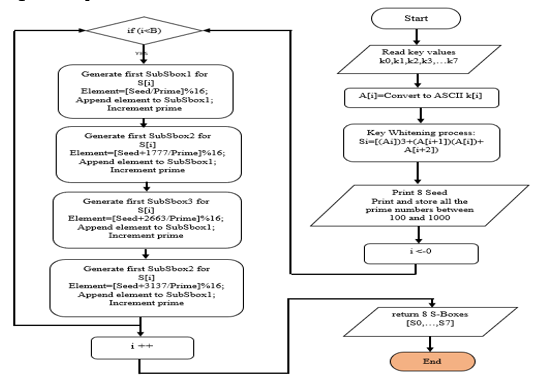
The primary objective of cryptography is to protect information from various types of security breaches. To enhance their resilience, most cryptographic techniques modify parameters such as key size, number of iterations, and incorporation of S-boxes. The only non-linear component of a substitution-permutation network is the S-box. The contents of S-boxes used in the conventional method remain constant and never undergo any changes, thus making them static. The proposed system incorporates Dynamic S-boxes, where the contents of the S-boxes change based on the key used. The values for the 8 S-boxes are created by converting the keys into their matching ASCII values. It has been discovered that the output of dynamic DES when used with audio and video data is more secure than static DES. When evaluating factors such as non-linearity, balance, implementation requirements in terms of time and memory, and the ability to resist linear and differential cryptanalysis, Dynamic S-boxes demonstrate superior performance.
Downloads
References
Hellman, Martin E. "I.des will be totally insecure within ten years'." IEEE spectrum 16.7 (1979): 32-40.
Alani, Mohammed M. "DES96-improved DES security." 2010 7th International Multi-Conference on Systems, Signals and Devices. IEEE, 2010.
Manikandan, G., et al. "A modified crypto scheme for enhancing data security." Journal of Theoretical and applied information Technology 35.2 (2012): 149-154.
Shah Kruti, R., and Bhavika Gambhava. "New approach of data encryption standard algorithm." International Journal of Soft Computing and Engineering (IJSCE) ISSN (2012): 2231-2307.
Arya, Govind Prasad, et al. "A cipher design with automatic key generation using the combination of substitution and transposition techniques and basic arithmetic and logic operations." The SIJ Transactions on Computer Science Engineering & its Applications (CSEA) 1.1 (2013): 21-24.
Wong, Duncan S., Hector Ho Fuentes, and Agnes Hui Chan. "The performance measurement of cryptographic primitives on palm devices." Seventeenth Annual Computer Security Applications Conference. IEEE, 2001.
Rivest, Ronald L., Adi Shamir, and Leonard Adleman. "A method for obtaining digital signatures and public-key cryptosystems." Communications of the ACM 21.2 (1978): 120-126.
Juremi, Julia, Ramlan Mahmod, and Salasiah Sulaiman. "A proposal for improving AES S-box with rotation and key-dependent." Proceedings Title: 2012 International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec). IEEE, 2012.
Al-Muhammed, Muhammed Jassem. "Light but Effective Encryption Technique based on Dynamic Substitution and Effective Masking." International Journal of Advanced Computer Science and Applications 9 (2018).
Singh, Sombir, Sunil K. Maakar, and Dr Sudesh Kumar. "Enhancing the security of DES algorithm using transposition cryptography techniques." International Journal of Advanced Research in Computer Science and Software Engineering 3.6 (2013): 464-471.
Gupta, Nimmi. "Implementation of optimized des encryption algorithm upto 4 round on spartan 3." International Journal of Computer Technology and Electronics Engineering (IJCTEE) 2.1 (2012): 82-86.
Patel, Payal, Kruti Shah, and Khushbu Shah. "Enhancement Of Des Algorithm With Multi State Logic." International Journal of Research in Computer Science 4.3 (2014): 13.
Albassalli, A. M. B., and A-MA Wahdan. "Genetic algorithm cryptanalysis of a feistel type block cipher." International Conference on Electrical, Electronic and Computer Engineering, 2004. ICEEC'04.. IEEE, 2004.
Sharma, Arvind Kumar, and Hitesh Sharma. "New Approach To Des With Enhanced Key Management And Encryption/Decryption System (Des Ultimate)." International Journal of Advances in Engineering & Technology 8.3 (2015): 368.
Krishnamurthy, G. N., and V. Ramaswamy. "Making AES stronger: AES with key dependent S-box." IJCSNS International Journal of Computer Science and Network Security 8.9 (2008): 388-398.
Mahmoud, Eman Mohammed, et al. "Enhancing channel coding using AES block cipher." International Journal of Computer Applications 61.6 (2013).
Zahid, Amjad Hussain, Eesa Al-Solami, and Musheer Ahmad. "A novel modular approach-based substitution-box design for image encryption." IEEE Access 8 (2020): 150326-150340.
Patil, S. D. ., & Deore, P. J. . (2023). Machine Learning Approach for Comparative Analysis of De-Noising Techniques in Ultrasound Images of Ovarian Tumors. International Journal on Recent and Innovation Trends in Computing and Communication, 11(2s), 230–236. https://doi.org/10.17762/ijritcc.v11i2s.6087
Oukili, Soufiane, and Seddik Bri. "High speed efficient advanced encryption standard implementation." 2017 International Symposium on Networks, Computers and Communications (ISNCC). IEEE, 2017.
Alabaichi, Ashwak, and Adnan Ibrahem Salih. "Enhance security of advance encryption standard algorithm based on key-dependent S-box." 2015 Fifth International Conference on Digital Information Processing and Communications (ICDIPC). IEEE, 2015.
Altaleb, Anas, et al. "An algorithm for the construction of substitution box for block ciphers based on projective general linear group." AIP Advances 7.3 (2017): 035116.
Anees, Amir, and Zeeshan Ahmed. "A technique for designing substitution box based on van der pol oscillator." Wireless Personal Communications 82.3 (2015): 1497-1503.
Akande, Oluwatobi Noah, et al. "A Dynamic Round Triple Data Encryption Standard Cryptographic Technique for Data Security." International Conference on Computational Science and Its Applications. Springer, Cham, 2020.
Ullah, Atta, Sajjad Shaukat Jamal, and Tariq Shah. "A novel scheme for image encryption using substitution box and chaotic system." Nonlinear Dynamics 91.1 (2018): 359-370.
Siddiqui, Nasir, et al. "A Novel Algebraic Technique for Design of Computational Substitution-Boxes Using Action of Matrices on Galois Field." IEEE Access 8 (2020): 197630-197643.
Khan, Fadia Ali, et al. "A new technique for designing 8× 8 substitution box for image encryption applications." 2017 9th Computer Science and Electronic Engineering (CEEC). IEEE, 2017.
Nilima, S., and Arora Nitin. "Randamization Technique for Desiging of Substitution Box in Data Encryption Standard Algorithm." International Journal of Mathematical Sciences and Computing 5.3 (2019): 27-36.
Adhie, Roy Pramono, et al. "Implementation cryptography data encryption standard (DES) and triple data encryption standard (3DES) method in communication system based near field communication (NFC)." Journal of Physics: Conference Series. Vol. 954. No. 1. IOP Publishing, 2018.
Akhtar, Tanveer, Nizamud Din, and Jamal Uddin. "Substitution box design based on chaotic maps and cuckoo search algorithm." 2019 International conference on advanced communication technologies and networking (CommNet). IEEE, 2019.
Dr. Bhushan Bandre. (2013). Design and Analysis of Low Power Energy Efficient Braun Multiplier. International Journal of New Practices in Management and Engineering, 2(01), 08 - 16. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/12
Khan, Fadia Ali, et al. "A novel substitution box for encryption based on Lorenz equations." 2017 International Conference on Circuits, System and Simulation (ICCSS). IEEE, 2017.
Arshad, Sadiqa, and Majid Khan. "New extension of data encryption standard over 128-bit key for digital images." Neural Computing and Applications (2021): 1-14.
Siddiqui, Nasir, et al. "A highly nonlinear substitution-box (S-box) design using action of modular group on a projective line over a finite field." Plos one 15.11 (2020): e0241890.
Khan, Muhammad Fahad, Adeel Ahmed, and Khalid Saleem. "A novel cryptographic substitution box design using Gaussian distribution." IEEE Access 7 (2019): 15999-16007.
Mr. Rahul Sharma. (2013). Modified Golomb-Rice Algorithm for Color Image Compression. International Journal of New Practices in Management and Engineering, 2(01), 17 - 21. Retrieved from http://ijnpme.org/index.php/IJNPME/article/view/13
Riaz, Fozia, and Nasir Siddiqui. "Design of an Efficient Cryptographic Substitution Box by using Improved Chaotic Range with the Golden Ratio." International Journal of Computer Science and Information Security (IJCSIS) 18.1 (2020).
Rahaman, Ziaur, et al. "A novel structure of advance encryption standard with 3-dimensional dynamic S-Box and key generation matrix." arXiv preprint arXiv:2005.00157 (2020).
Alghafis, Abdullah, Noor Munir, and Majid Khan. "An encryption scheme based on chaotic Rabinovich-Fabrikant system and S 8 confusion component." Multimedia Tools and Applications 80.5 (2021): 7967-7985.
Ahmad, Musheer, et al. "Particle swarm optimization based highly nonlinear substitution-boxes generation for security applications." IEEE Access 8 (2020): 116132-116147.
Seghier, Athmane, Jianxin Li, and Da Zhi Sun. "Advanced encryption standard based on key dependent S‐Box cube." IET Information Security 13.6 (2019): 552-558.
Akande, Oluwatobi Noah, et al. "A Dynamic Round Triple Data Encryption Standard Cryptographic Technique for Data Security." International Conference on Computational Science and Its Applications. Springer, Cham, 2020.
Özkaynak, Fatih, and Mukhlis I. Muhamad. "Alternative substitutional box structures for DES." 2018 6th International Symposium on Digital Forensic and Security (ISDFS). IEEE, 2018
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





