Wireless Sensor Network Security with the Probability Based Neighbourhood Estimation
Keywords:
Wireless Sensor Network, Probability, Neighbourhood value, threshold valueAbstract
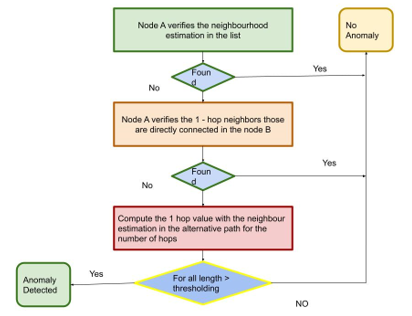
Wireless Sensor Network (WSN) is considered as the ad hic network environment in the resource-limited devices for the energy, storage, bandwidth, and computation. In WSN environment security is a significant contribution for more computation and power in the nodes. Sensor node comprises of the hostile environment for the remote management of network topology. The captured node exhibits the fundamental characteristics in the security of the WSN. The security constraints in the WSN derives significant attention towards the vast range of application for traffic monitoring in the network. Another challenge in the WSN is the mobility of the sensor nodes in which nodes are located far away between the nodes each other with the one-hop neighbors. In this paper proposed a Probability Neighbourhood Estimation (PNE) model for improved security in the WSN environment. The proposed PNE mode estimates the neighborhood estimation of the node. With the computation of the threshold value in the neighboring nodes, the probability features of the nodes are computed. The performance of the proposed PNE model is comparatively examined with the existing Pworm and RTT based approach. The analysis of the results expressed that the proposed PNE model achieves the effective performance for the throughput and PDF value of 0.99 which is a significantly higher value than the 0.91 and 0.98. The analysis expressed that the proposed model~6 – 7% than the existing models..
Downloads
References
Cao, C., Tang, Y., Huang, D., Gan, W., & Zhang, C. (2021). IIBE: an improved identity-based encryption algorithm for WSN security. Security and Communication Networks, 2021.
Singh, S., & Saini, H. S. (2021). Learning-based security technique for selective forwarding attack in clustered WSN. Wireless Personal Communications, 118(1), 789-814.
Qichen, W. (2022, April). Research progress on wireless sensor network (WSN) security technology. In Journal of Physics: Conference Series (Vol. 2256, No. 1, p. 012043). IOP Publishing.
Ávila, K., Sanmartin, P., Jabba, D., & Gómez, J. (2021). An analytical survey of attack scenario parameters on the techniques of attack mitigation in WSN. Wireless Personal Communications, 1-32.
Ramasamy, K., Anisi, M. H., & Jindal, A. (2021). E2DA: Energy efficient data aggregation and end-to-end security in 3D reconfigurable WSN. IEEE Transactions on Green Communications and Networking, 6(2), 787-798.
Majumdar, P., Mitra, S., & Bhattacharya, D. (2021). IoT for promoting agriculture 4.0: a review from the perspective of weather monitoring, yield prediction, security of WSN protocols, and hardware cost analysis. Journal of Biosystems Engineering, 1-22.
Hema Kumar, M., Mohanraj, V., Suresh, Y., Senthilkumar, J., & Nagalalli, G. (2021). Trust aware localized routing and class based dynamic block chain encryption scheme for improved security in WSN. Journal of Ambient Intelligence and Humanized Computing, 12(5), 5287-5295.
Sumalatha, M. S., & Nandalal, V. (2021). An intelligent cross layer security based fuzzy trust calculation mechanism (CLS-FTCM) for securing wireless sensor network (WSN). Journal of Ambient Intelligence and Humanized Computing, 12(5), 4559-4573.
Aljadani, N., & Gazdar, T. (2022). A Novel Security Architecture for WSN-Based Applications in Smart Grid. Smart Cities, 5(2), 633-649.
Soni, G., & Chandravanshi, K. (2021, August). Security scheme to identify malicious maneuver of flooding attack for WSN in 6G. In 2021 8th International Conference on Signal Processing and Integrated Networks (SPIN) (pp. 124-129). IEEE.
Kwon, D. K., Yu, S. J., Lee, J. Y., Son, S. H., & Park, Y. H. (2021). WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors, 21(3), 936.
Jayatunga, E. H., Ranaweera, P. S., & Balapuwaduge, I. A. M. (2021). Blockchain advances and security practices in WSN, CRN, SDN, opportunistic mobile networks, delay tolerant networks. In Revolutionary Applications of Blockchain-Enabled Privacy and Access Control (pp. 1-34). IGI Global.
Butt, T. M., Riaz, R., Chakraborty, C., Rizvi, S. S., & Paul, A. (2021). Cogent and energy efficient authentication protocol for wsn in iot. Comput. Mater. Contin, 68, 1877-1898.
Rhim, H., Tamine, K., Abassi, R., Sauveron, D., & Guemara, S. (2021, March). Enhancing security using digital signature in an efficient Network Coding-enabled WSN. In 2021 18th International Multi-Conference on Systems, Signals & Devices (SSD) (pp. 70-78). IEEE.
Gulganwa, P., & Jain, S. (2022). EES-WCA: energy efficient and secure weighted clustering for WSN using machine learning approach. International Journal of Information Technology, 14(1), 135-144.
Bakshi, G., & Sahu, H. WSN Security: Intrusion Detection Approaches Using Machine Learning. In Computational Intelligence for Wireless Sensor Networks (pp. 151-174). Chapman and Hall/CRC.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Nachaat Mohamed, K. Sampath Kumar, Sanskriti Sharma, R. Dinesh Kumar, Shiv Mehta, Isa Mishra

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





