Decision Tree Based Data Pruning with the Estimation of Oversampling Attributes for the Secure Communication in IOT
Keywords:
Security, Attacks, Internet of Things (IoT), Pruning, Decision Tree, Oversampling ModelAbstract
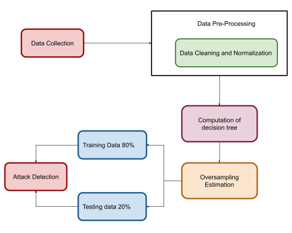
Internet of Things (IoT) exhibits a significant role to evaluate the error or supply shortage. The IoT demand for the security and authentication of the devices is considered as the most priority for software developments. As the IoT communication comprises of an interconnected environment for the both digital and physical scenarios. The IoT environment exhibits anything and anywhere services to the communication medium. In those scenarios, security is considered as the major concern to protect the data resources from unauthorized resources for the appropriate security and privacy. This paper proposed a decision tree-based pruning scheme for the IoT attributes. The proposed decision tree based pruning for the security attributes are defined as the decision tree pruning (DTP). The proposed DTP model comprises of the minority oversampling model for the estimation of the attack features. With the developed DTP model, the attack datasets were pre-processed and evaluated for the different attack environments in to consideration. The DTP processed data were applied over the conventional machine learning-based model for the computation attacks in the network. The simulation results expressed that proposed DTP model achieves the accuracy value of 98% which is ~3% higher than the conventional classifier techniques.
Downloads
References
Shaukat, K., Alam, T. M., Hameed, I. A., Khan, W. A., Abbas, N., & Luo, S. (2021, September). A review on security challenges in internet of things (IoT). In 2021 26th International Conference on Automation and Computing (ICAC) (pp. 1-6). IEEE.
Yu, Z., Song, L., Jiang, L., & Sharafi, O. K. (2021). Systematic literature review on the security challenges of blockchain in IoT-based smart cities. Kybernetes.
Thoutam, V. (2021). Unique Security Challenges Of Iot Devices And Spectrum Of Security Considerations. Journal of Artificial Intelligence, Machine Learning and Neural Network (JAIMLNN) ISSN: 2799-1172, 1(02), 1-7.
Touqeer, H., Zaman, S., Amin, R., Hussain, M., Al-Turjman, F., & Bilal, M. (2021). Smart home security: challenges, issues and solutions at different IoT layers. The Journal of Supercomputing, 77(12), 14053-14089.
Marshal, R., Gobinath, K., & Rao, V. V. (2021, April). Proactive Measures to Mitigate Cyber Security Challenges in IoT based Smart Healthcare Networks. In 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS) (pp. 1-4). IEEE.
Raghuvanshi, A., Singh, U. K., Shuaib, M., & Alam, S. (2021). An investigation of various applications and related security challenges of Internet of things. Materials Today: Proceedings.
Malhotra, P., Singh, Y., Anand, P., Bangotra, D. K., Singh, P. K., & Hong, W. C. (2021). Internet of things: Evolution, concerns and security challenges. Sensors, 21(5), 1809.
Karale, A. (2021). The challenges of IoT addressing security, ethics, privacy, and laws. Internet of Things, 15, 100420.
Mishra, N., & Pandya, S. (2021). Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access, 9, 59353-59377.
Mohanty, J., Mishra, S., Patra, S., Pati, B., & Panigrahi, C. R. (2021). IoT security, challenges, and solutions: a review. Progress in Advanced Computing and Intelligent Engineering, 493-504.
Balogh, S., Gallo, O., Ploszek, R., Špaček, P., & Zajac, P. (2021). IoT Security Challenges: Cloud and Blockchain, Postquantum Cryptography, and Evolutionary Techniques. Electronics, 10(21), 2647.
Azrour, M., Mabrouki, J., Guezzaz, A., & Kanwal, A. (2021). Internet of things security: challenges and key issues. Security and Communication Networks, 2021.
Ali, R. F., Muneer, A., Dominic, P. D. D., Taib, S. M., & Ghaleb, E. A. (2021, August). Internet of Things (IoT) Security Challenges and Solutions: A Systematic Literature Review. In International Conference on Advances in Cyber Security (pp. 128-154). Springer, Singapore.
Gupta, H., & Sharma, S. (2021, June). Security Challenges in Adopting Internet of Things for Smart Network. In 2021 10th IEEE International Conference on Communication Systems and Network Technologies (CSNT) (pp. 761-765). IEEE.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





