Reuse Attack Prevention Through Randomization Traversal Algorithm with the Code Reduction Technique for Operating System Security
Keywords:
Computer Security, Randomization Traversal Algorithm, Preorder, Attack Reuse, detection rateAbstract
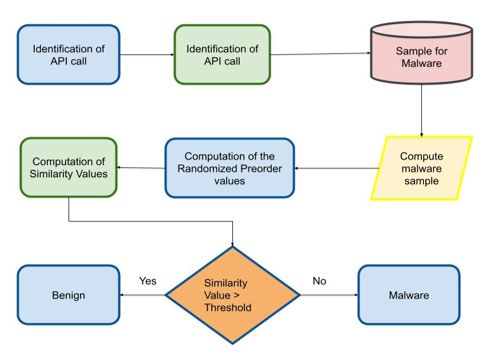
Computer security is considered the important end system for the complete network improvement in the host. Despite of the advancement in end-system security, the network is subjected to different malicious and network attacks in the larger network for the constant threat to data protection for data privacy and integrity. Security risk management comprises of two issues in the security of the larger network environment with the secured system environment. The code reuse attack is a severe threat in the computer network environment due to alteration in the complete network. This paper proposed a Preorder Randomization Traversal Algorithm (PreorderRTA) for the prevention of code reuse attacks. With the proposed PreorderRTA comprises randomized features for the generation of the keys in the computer network. The developed model concentrated on code reuse attack detection and prevention. The proposed PreorderRTA model achieves a higher detection rate for the rootkit, worms and Viruses in the system compared with the existing technique. The proposed PreorderRTA achieves the detection rate of 99.34% while the existing approaches achieves below 90%.
Downloads
References
Mishra, S., & Polychronakis, M. (2021, April). SGXPecial: Specializing SGX Interfaces against Code Reuse Attacks. In Proceedings of the 14th European Workshop on Systems Security (pp. 48-54).
Lin, K., Xia, H., Zhang, K., & Tu, B. (2021, September). AddrArmor: An Address-based Runtime Code-reuse Attack Mitigation for Shared Objects at the Binary-level. In 2021 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom) (pp. 117-124). IEEE.
Wang, J., Zhang, Z., Ma, B., Yao, Y., & Ji, X. (2021, May). Research on SSTI attack defense technology based on instruction set randomization. In 2021 2nd International Conference on Artificial Intelligence and Information Systems (pp. 1-5).
Nikolaev, R., Nadeem, H., Stone, C., & Ravindran, B. (2022, February). Adelie: continuous address space layout re-randomization for Linux drivers. In Proceedings of the 27th ACM International Conference on Architectural Support for Programming Languages and Operating Systems (pp. 483-498).
Potteiger, B., Cai, F., Zhang, Z., & Koutsoukos, X. (2022). Data space randomization for securing cyber-physical systems. International Journal of Information Security, 21(3), 597-610.
Schloegel, M., Blazytko, T., Basler, J., Hemmer, F., & Holz, T. (2021, October). Towards Automating Code-Reuse Attacks Using Synthesized Gadget Chains. In European Symposium on Research in Computer Security (pp. 218-239). Springer, Cham.
Novković, B. (2021). A Taxonomy of Defenses against Memory Corruption Attacks. In 2021 44th International Convention on Information, Communication and Electronic Technology (MIPRO) (pp. 1196-1201). IEEE.
Yoon, H., & Lee, M. (2022). SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory. Applied Sciences, 12(15), 7655.
Shrivastava, R. K., Singh, S. P., Hasan, M. K., Islam, S., Abdullah, S., & Aman, A. H. M. (2022). Securing Internet of Things devices against code tampering attacks using Return Oriented Programming. Computer Communications, 193, 38-46.
Xu, S., & Wang, Y. (2022). Defending against Return-Oriented Programming attacks based on return instruction using static analysis and binary patch techniques. Science of Computer Programming, 217, 102768.
Ying, H., Zhou, H., Degani, A., & Sacks, R. (2022). A two‐stage recursive ray tracing algorithm to automatically identify external building objects in building information models. Computer‐Aided Civil and Infrastructure Engineering, 37(8), 991-1009.
Huang, X., Yan, F., Zhang, L., & Wang, K. (2021). Honeygadget: A deception based approach for detecting code reuse attacks. Information Systems Frontiers, 23(2), 269-283.
Lee, S., Kang, H., Jang, J., & Kang, B. B. (2021). Savior: Thwarting stack-based memory safety violations by randomizing stack layout. IEEE Transactions on Dependable and Secure Computing.
Zuo, Z., Fang, Y., Huang, Q., Liao, Y., Wang, Y., & Wang, C. (2021, October). Derivation and Formal Proof of Binary Tree Depth Non-Recursive Algorithm. In 2021 5th International Conference on Communication and Information Systems (ICCIS) (pp. 191-196). IEEE.
Zhang, C., Bonifati, A., Kapp, H., Haprian, V. I., & Lozi, J. P. (2022). A Reachability Index for Recursive Label-Concatenated Graph Queries. arXiv preprint arXiv:2203.08606.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Prashant Johri, Madhavi Dhingra, Dilli Babu M., Bipin Sule, Arvind Kumar Pandey, Ankita Vitthal Karale

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





