Revocable and Secure Multi-Authority Attribute- Encryption Scheme
Keywords:
Multi-Authority CP-ABE, Access policy, Elliptic curve cryptography, Revocation, Lagrange interpolationAbstract
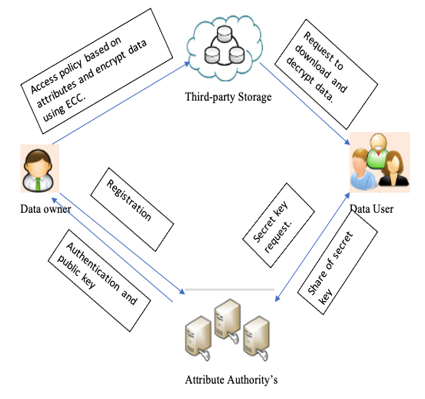
Security is an important factor as nowadays many systems generates and process huge amount of data. This also leads many of us to rely on a third-party service provider for storing sensitive and confidential data. Providing outsourcing means the data owner will encrypt and store the data in a third-party storage system. In this paper, we are proving solutions for two main problems. The first issue is what if the attribute authority itself can access the data because the attributes and secret keys are known by attribute. This issue is called the key escrow problem. For solving it we are proposing a multi-authority system with Elliptic Curve Cryptography. The second issue that we addressed in this paper is the revocation problem, which means when someone leaves the system should be prohibited from accessing subsequent data this is called forward security and as a second case when someone joins the system should be prevented from accessing previous shared date this is called backward security. In this paper, we address both forward and backward security. For solving this problem we are using the concept of the Lagrange interpolation technique for generating and verifying secret keys. Based on this technique secret key will be dynamically altered and used for encryption and due to this can achieve greater security.
Downloads
References
J. Bethencourt, A. S. Ucla, and B. Waters, “Ciphertext-Policy Attribute-Based Encryption.”
B. Waters, “Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization.”
A. Lewko and B. Waters, “Decentralizing Attribute-Based Encryption.”
Z. Liu, J. Xu, Y. Liu, and B. Wang, “Updatable Ciphertext-Policy Attribute-Based Encryption Scheme with Traceability and Revocability,” IEEE Access, vol. 7, pp. 66832–66844, 2019, doi: 10.1109/ACCESS.2019.2918434.
A. Sahai and B. Waters, “Fuzzy Identity-Based Encryption,” pp. 457–473, 2005.
S. Fugkeaw, “A Lightweight Policy Update Scheme for Outsourced Personal Health Records Sharing,” IEEE Access, vol. 9, pp. 54862–54871, 2021, doi: 10.1109/ACCESS.2021.3071150.
Y. Ming, B. He, and C. Wang, “Efficient Revocable Multi-Authority Attribute-Based Encryption for Cloud Storage,” IEEE Access, vol. 9, pp. 42593–42603, 2021, doi: 10.1109/ACCESS.2021.3066212.
J. Li, N. Chen, and Y. Zhang, “Extended file hierarchy access control scheme with attribute-based encryption in cloud computing,” IEEE Trans Emerg Top Comput, vol. 9, no. 2, pp. 983–993, Apr. 2021, doi: 10.1109/TETC.2019.2904637.
L. K. Jie and H. Kamarulhaili, “Polynomial interpolation in the elliptic curve cryptosystem,” J Math Stat, vol. 7, no. 4, pp. 326–331, Jan. 2011, doi: 10.3844/jmssp.2011.326.331.
K. Sudhamani, P. Rama Rao, & R. Vara Prasad. (2016). Secure Auditing and Deduplicating Data in Cloud. International Journal of Computer Engineering In Research Trends, 3(1), 1-5.
B. Applebaum and O. Nir, “Upslices, Downslices, and Secret-Sharing with Complexity of 1.5 n,” 2021.
J. Wei, W. Liu and X. Hu, "Secure and Efficient Attribute-Based Access Control for Multiauthority Cloud Storage," in IEEE Systems Journal, vol. 12, no. 2, pp. 1731-1742, June 2018.
D. Han, N. Pan, and K. C. Li, “A Traceable and Revocable Ciphertext-Policy Attribute-based Encryption Scheme Based on Privacy Protection,” IEEE Trans Dependable Secure Comput, vol. 19, no. 1, pp. 316–327, 2022, doi: 10.1109/TDSC.2020.2977646.
S. Tu, M. Waqas, F. Huang, G. Abbas, and Z. H. Abbas, “A revocable and outsourced multi-authority attribute-based encryption scheme in fog computing,” Computer Networks, vol. 195, Aug. 2021, doi: 10.1016/j.comnet.2021.108196.
Budhhe, A., & Hajare, H. R. (2016). Secure Data Communication Using IDEA for Decentralized Disruption-Tolerant Military Networks. International Journal of Computer Engineering in Research Trends, 3(12), 625-628.
C. Ge, W. Susilo, J. Baek, Z. Liu, J. Xia, and L. Fang, “Revocable Attribute-Based Encryption with Data Integrity in Clouds,” IEEE Trans Dependable Secure Comput, 2021, doi: 10.1109/TDSC.2021.3065999.
Maloth, Bhavsingh, K. Pavan Kumar, G. Nirusha, and C. Vijaya Mohan. "Discrete Keyword Search in Cloud Computing over Attribute Based Encryption." International Journal of Computer Science Engineering & Technology 2, no. 3 (2012).
A. P. R and A. v N Krishna, “An Efficient Nonlinear Access Policy Based On Quadratic Residue For Ciphertext Policy Attribute Based Encryption,” J Theor Appl Inf Technol, vol. 15, no. 21, 2021, [Online]. Available: www.jatit.org
K. Yang and X. Jia, “Expressive, efficient, and revocable data access control for multi-authority cloud storage,” IEEE Trans. Parallel Distrib. Syst., vol. 25, no. 7, pp. 1735–1744, Jul. 2014.
D, B. S. and P, V. K. (2023) “Digital Railway Ticketing Using Ethereum and Smart contracts”, International Journal of Computer Engineering in Research Trends, 10(4), pp. 167–171. doi: 10.22362/ijcertpublications.v10i4.10.
J. Gu, J. Shen, and B. Wang, “A robust and secure multi-authority access control system for cloud storage,” Peer Peer Netw Appl, vol. 14, no. 3, pp. 1488–1499, May 2021, doi: 10.1007/s12083-020-01055-5.
P. S. Challagidad and M. N. Birje, “Efficient Multi-authority Access Control using Attribute-based Encryption in Cloud Storage,” in Procedia Computer Science, 2020, vol. 167, pp. 840–849. doi: 10.1016/j.procs.2020.03.423.
L. Zhang, Y. Ye, and Y. Mu, “Multiauthority Access Control with Anonymous Authentication for Personal Health Record,” IEEE Internet Things J, vol. 8, no. 1, pp. 156–167, Jan. 2021, doi: 10.1109/JIOT.2020.3000775.
G. K. Sandhia and S. V. K. Raja, “Secure sharing of data in cloud using MA-CPABE with elliptic curve cryptography,” J Ambient Intell Humaniz Comput, vol. 13, no. 8, pp. 3893–3902, Aug. 2022, doi: 10.1007/s12652-021-03287-6.
A. Beimel and Y. Ishai, “On the power of nonlinear secret-sharing,” SIAM J Discret Math, vol. 19, no. 1, pp. 258–280, 2005, doi: 10.1137/S0895480102412868.
K. Lee, “Revocable hierarchical identity-based encryption with adaptive security,” Theor Comput Sci, vol. 880, pp. 37–68, Aug. 2021, doi: 10.1016/j.tcs.2021.05.034.
K. Dhal, S. C. Rai, P. K. Pattnaik, and S. Tripathy, “CEMAR: a fine grained access control with revocation mechanism for centralized multi-authority cloud storage,” Journal of Supercomputing, vol. 78, no. 1, pp. 987–1009, Jan. 2022, doi: 10.1007/s11227-021-03908-z.
C. Wang, H. Jin, R. Wei, and K. Zhou, “Revocable, dynamic and decentralized data access control in cloud storage,” Journal of Supercomputing, vol. 78, no. 7, pp. 10063–10087, May 2022, doi: 10.1007/s11227-021-04277-3.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





