A Novel Approach for Intrusion Detection System Using Equalized Multi-Routing Protocol in MANET
Keywords:
MANET, Intrusion Detection System, Trust table, TRF, F-CNB, CH, EMRP, Fitness measure, detection rateAbstract
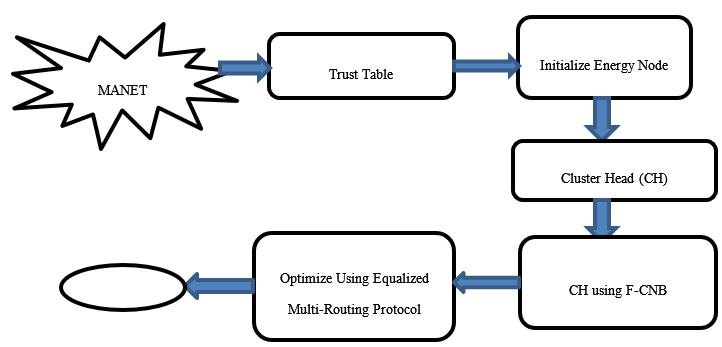
In recent years, a Mobile Ad Hoc Network (MANET) has emerged as a Wireless Communication Network (WCN) consisting of several highly mobile nodes moving in various commands. It uses an Intrusion Detection System (IDS), a monitoring parameter, to detect network-related activity by alerting the service operations centre. Since MANET has no infrastructure, nodes can connect randomly. Ad hoc networks, however, are more vulnerable than wired environments; this vulnerability also affects the MANET characteristics. However, protecting MANETs against malicious nodes randomly integrated into the network is a significant challenge. To solve this problem, the first stage of malicious nodes can be rejected using a Trust Table (TT) to bring healthy communication to the network. Furthermore, we verify the performance of IDS based on direct Trust, indirect Trust, and error, using the Trust Routing Factor (TRF) method. Second, we use an Initialized Energy Node (IEN) method to find out whether the remaining energy range of the communication nodes in the network is at the minimum or maximum energy ratio and energy consumption. Next, we use Cluster Head (CH) can be selected Using Fuzzy Clustering Naive Bayes (fuzzy CNB) strategies to solve the problems of MANET's energy degradation and transmission delay. Finally, we proposed an optimal selection based on a new Equalised Multi-Routing Protocol (EMRP) method to generate multiple paths from the source to the destination node using maximum Fitness Measure (FM). The simulation result in the EMRP method can obtain maximum energy, efficiency, detection rate, and minimum delay in the presence of an attack.
Downloads
References
Mahin, S. H., Taranum, F., Fatima, L. N., and Khan, K. U. R (2019). Detection and interception of black hole attack with justification using anomaly-based intrusion detection system in MANETs International Journal of Recent Technology and Engineering, vol. 8, no. 2 Special Issue 11, pp. 2392–2398.
Vishnu Balan, E., Priyan, M. K., Gokulnath C and Vsha Devi, G (2015). Fuzzy Based Intrusion Detection Systems in MANET science direct elsevier Procedia Computer Science, vol. 50, pp. 109-114.
Opinder Singh, Jatinder Singh and Ravinder Singh (2017). Multi-level trust based intelligence intrusion detection system to detect the malicious nodes using elliptic curve cryptography in MANET Cluster Computing, pp. 1-13.
Veeraiah, N and Krishna, B. T (2020). An approach for optimal-secure multipath routing and intrusion detection in MANET in Evolutionary Intelligence, Berlin, Germany:Springer, pp. 1-15.
Sivanesh, S and Dhulipala V.R.S (2021). Analytical Termination of Malicious Nodes (ATOM): An Intrusion Detection System for Detecting Black Hole Attack in Mobile Ad Hoc Networks. Wireless Personal Communications, 1-14.
Makani, Ruchi and Reddy B.V.R (2022). Trust-based-tuning of Bayesian-watchdog intrusion detection for fast and improved detection of black hole attacks in mobile ad hoc networks. International Journal of Advanced Intelligence Paradigms, 21(1-2), 53-71.
Raj, Paul, A.A and Mozhi J.K.K (2021). Real-Time Multi Level Behavioral Analysis Model for Efficient Intrusion Detection in Manet. Malaya Journal of Matematik, S1, 140-144.
Kowsigan, M., Rajeshkumar, J., Baranidharan, B., Prasath, N., Nalini, S and Venkatachalam K. A (2021). novel intrusion detection system to alleviate the black hole attacks to improve the security and performance of the MANET. Wireless Personal Communications, 1-21.
Pandey, P and Barve, A (2019). An Energy-Efficient Intrusion Detection System for MANET Data Engineering and Applications.
Marchang, N., Datta, R and S. K. Das, S. K (2017) A Novel Approach for Efficient Usage of Intrusion Detection System in Mobile Ad Hoc Networks in IEEE Transactions on Vehicular Technology, vol. 66, no. 2, and pp. 1684-1695.
Mahendra Prasad, Sachin Tripathi, Keshav Dahal (2023). An intelligent intrusion detection and performance reliability evaluation mechanism in mobile ad-hoc networks, Engineering Applications of Artificial Intelligence, Volume 119, 105760, ISSN 0952-1976.
Prasad, M., Tripathi, S and Dahal, K. A (2023). probability estimation-based feature reduction and Bayesian rough set approach for intrusion detection in the mobile ad-hoc network. Appl Intell 53, 7169–7185.
Gopalakrishnan Subburayalu, Hemanand Duraivelu, Arun Prasath Raveendran, Rajesh Arunachalam, Deepika Kongara and Chitra Thangavel (2021). Cluster Based Malicious Node Detection System for Mobile Ad-Hoc Network Using ANFIS Classifier, Journal of Applied Security Research.
Gopalakrishnan, S and Kumar, P (2016). Performance Analysis of Malicious Node Detection and Elimination Using Clustering Approach on MANET. Circuits and Systems, 7, 748-758.
D. Hemanand, G., Reddy, S. S., Babu, K. R., Balmuri, T., Chitra, and S. Gopalakrishnan (2022). “An Intelligent Intrusion Detection and Classification System using CSGO-LSVM Model for Wireless Sensor Networks (WSNs)”, Int J Intell Syst Appl Eng, vol. 10, no. (3), pp. 285–293.
Arul Selvan M., Selvakumar, S (2019). Malicious node identification using quantitative intrusion detection techniques in manet. Cluster Comput 22(3):7069–7077.
Sivanesh, S., Sarma Dhulipala, V. R (2020) Accurate and cognitive intrusion detection system (acids): a novel black hole detection mechanism in mobile ad hoc networks. Mobile Networks and Applications, 1–9.
Bouhaddi, M., Radjef, M.S, Adi, K (2018). an efficient intrusion detection in resource-constrained mobile ad-hoc networks. Comput Secur 76:156–177.
Bharathisindhu, P., Selva Brunda, S (2019). An improved model based on genetic algorithm for detecting intrusion in mobile ad hoc network. Clust Comput 22(1):265–275
Bala, K., Jothi, S., Chandrasekar, A (2019). an enhanced intrusion detection system for mobile ad-hoc network based on traffic analysis. Clust Comput 22(6):15205–15212.
Islabudeen, M., Kavitha Devi, M.K (2020). a smart approach for intrusion detection and prevention system in mobile ad hoc networks against security attacks. Wirel Pers Commun 112(1):193–224.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





