Robust and Secured Data Hiding Methodology over Digital Images using Deep Learning Enabled Steganographic Norms
Keywords:
Data Hiding, Steganography, Data Embedding, Information Hiding, Digital Watermarking, MultisourceAbstract
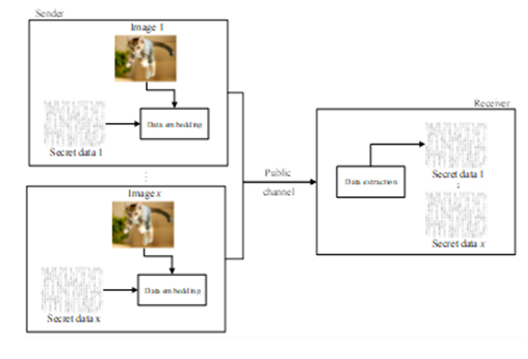
Steganography, as opposed to cryptography, is an art form for concealing information in a way that does not draw attention. Since ancient times, people have used this method to communicate and conceal sensitive information from strangers or hackers. Multimedia information is widely utilised as a result of the quick growth of computer networks, and digital media security has received a lot of attention. The facts of the case will be distorted by the manipulated photo used as forensic evidence, and social media photos that have been maliciously altered may harm the persons involved. Information-based digital image self-recovery concealing is used to assure the veracity and integrity of digital media. We suggest a multisource data-hiding system (MDHS), which extracts hidden information on the recipient's side and produces content that is jointly decided by the hidden information sent by all senders. Based on deep learning, this research draws a general conclusion on visual information hiding. Additionally, the suggested approach has the potential to enable lossless data recovery in the event of damage using the dynamic range adjustment technique. Modern information masking techniques based on deep learning are examined and shown. Simulation findings show that the suggested approach outperforms existing cutting-edge strategies in terms of payload and imperceptibility.
Downloads
References
A. G. Devi, A. Thota, G. Nithya, S. Majji, A. Gopatoti and L. Dhavamani, "Advancement of Digital Image Steganography using Deep Convolutional Neural Networks," 2022 International Interdisciplinary Humanitarian Conference for Sustainability (IIHC), Bengaluru, India, 2022, pp. 250-254, doi: 10.1109/IIHC55949.2022.10060230.
A. Kotkar, S. Khadapkar, A. Gupta and S. Jangale, "Multiple layered Security using combination of Cryptography with Rotational, Flipping Steganography and Message Authentication," 2022 IEEE International Conference on Data Science and Information System (ICDSIS), Hassan, India, 2022, pp. 1-5, doi: 10.1109/ICDSIS55133.2022.9915922.
J. Singh and M. Singla, "A Novel Method of high-Capacity Steganography Technique in Double Precision Images," 2021 International Conference on Computational Performance Evaluation (ComPE), Shillong, India, 2021, pp. 780-784, doi: 10.1109/ComPE53109.2021.9751905.
L. Lyubchyk, G. Grinberg, O. Dunaievska and M. Lubchick, "Recurrent Estimation of Hidden Markov Model Transition Probabilities from Aggregate Data," 2019 9th International Conference on Advanced Computer Information Technologies (ACIT), Ceske Budejovice, Czech Republic, 2019, pp. 64-67, doi: 10.1109/ACITT.2019.8779890.
S. Ali and N. Bouguila, "Maximum A Posteriori Approximation of Dirichlet and Beta-Liouville Hidden Markov Models for Proportional Sequential Data Modeling," 2020 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Toronto, ON, Canada, 2020, pp. 4081-4087, doi: 10.1109/SMC42975.2020.9283011.
T. Chadza, K. G. Kyriakopoulos and S. Lambotharan, "Contemporary Sequential Network Attacks Prediction using Hidden Markov Model," 2019 17th International Conference on Privacy, Security and Trust (PST), Fredericton, NB, Canada, 2019, pp. 1-3, doi: 10.1109/PST47121.2019.8949035.
E. H. Rachmawanto, D. R. I. M. Setiadi, C. A. Sari, P. N. Andono, O. Farooq and N. Pradita, "Spread Embedding Technique in LSB Image Steganography based on Chaos Theory," 2019 International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 2019, pp. 1-6, doi: 10.1109/ISEMANTIC.2019.8884266.
J. Deng, M. Tang, Y. Wang and Z. Wang, "LSB Color Image Embedding Steganography Based on Cyclic Chaos," 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 2019, pp. 1798-1802, doi: 10.1109/ICCC47050.2019.9064335.
H. Arora, G. K. Soni, R. K. Kushwaha and P. Prasoon, "Digital Image Security Based on the Hybrid Model of Image Hiding and Encryption," 2021 6th International Conference on Communication and Electronics Systems (ICCES), Coimbatre, India, 2021, pp. 1153-1157, doi: 10.1109/ICCES51350.2021.9488973.
M. Ueda and S. Imaizumi, "A Reversible Data Hiding Scheme for Printing with Special Color Inks Using Digital Halftoning," 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 2019, pp. 1135-1138, doi: 10.1109/GCCE46687.2019.9015581.
H. Arora, P. Kumar Sharma, K. Mitanshi and A. Choursia, "Enhanced Security of Digital Picture and Text Information with Hybride Model of Hiding and Encryption Techniques," 2022 International Conference on Sustainable Computing and Data Communication Systems (ICSCDS), Erode, India, 2022, pp. 1238-1241, doi: 10.1109/ICSCDS53736.2022.9760822.
N. J. de La Croix, C. C. Islamy and T. Ahmad, "Reversible Data Hiding using Pixel-Value-Ordering and Difference Expansion in Digital Images," 2022 IEEE International Conference on Communication, Networks and Satellite (COMNETSAT), Solo, Indonesia, 2022, pp. 33-38, doi: 10.1109/COMNETSAT56033.2022.9994516.
S. Kukreja and G. Kasana, "A Secure Reversible Data Hiding Scheme for Digital Images using Random Grid Visual Secret Sharing," 2019 Amity International Conference on Artificial Intelligence (AICAI), Dubai, United Arab Emirates, 2019, pp. 864-869, doi: 10.1109/AICAI.2019.8701360.
K. Luo, W. Gao and R. Yuan, "A Study of Reversible Data Hiding Technology with an Authentication Function," 2022 4th International Conference on Artificial Intelligence and Advanced Manufacturing (AIAM), Hamburg, Germany, 2022, pp. 52-57, doi: 10.1109/AIAM57466.2022.00018.
V. M. Manikandan and P. Renjith, "An Efficient Overflow Handling Technique for Histogram Shifting based Reversible Data Hiding," 2020 International Conference on Innovative Trends in Information Technology (ICITIIT), Kottayam, India, 2020, pp. 1-6, doi: 10.1109/ICITIIT49094.2020.9071553.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





