Enhancing Cloud Security with AuthPrivacyChain: A Blockchain-based Approach for Access Control and Privacy Protection
Keywords:
Cloud computing, Access control, Privacy protection, Blockchain, Smart contracts Cryptographic techniquesAbstract
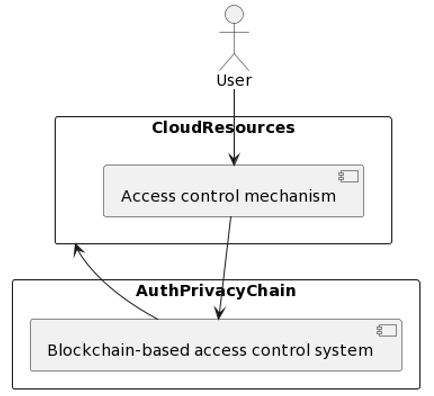
Cloud computing is a popular option for storing and accessing data and applications, but it raises security concerns related to access control and privacy protection. To address these concerns, this paper proposes a novel approach called AuthPrivacyChain, which is a blockchain-based solution for enhancing cloud security. AuthPrivacyChain provides a decentralized, transparent, and tamper-evident access control mechanism that uses smart contracts to define the rules for granting or denying access to cloud resources. The smart contracts are stored in a tamper-evident and immutable manner on the blockchain, which provides transparency and accountability for all access control decisions. The AuthPrivacyChain approach also uses cryptographic techniques, such as digital signatures and encryption, to ensure the privacy and confidentiality of user data. It uses a zero-knowledge proof mechanism to enable users to prove their identity without revealing any sensitive information. The authors evaluate the AuthPrivacyChain approach using a prototype implementation and show that it can provide effective access control and privacy protection for cloud-based resources. The results suggest that AuthPrivacyChain could be a promising solution to enhance cloud security and address security concerns related to cloud computing. Overall, AuthPrivacyChain is a blockchain-based solution that provides decentralized access control and privacy protection for cloud-based resources, using smart contracts, cryptographic techniques, and a distributed ledger to ensure transparency, accountability, and security.
Downloads
References
Zhou, M., Zhang, R., Xie, W., Qian, W., & Zhou, A. (2010, November). Security and privacy in cloud computing: A survey. In 2010 Sixth International Conference on Semantics, Knowledge and Grids (pp. 105-112). IEEE.
Pearson, S., & Benameur, A. (2010, November). Privacy, security and trust issues arising from cloud computing. In 2010 IEEE Second International Conference on Cloud Computing Technology and Science (pp. 693-702). IEEE.
Chen, D., & Zhao, H. (2012, March). Data security and privacy protection issues in cloud computing. In 2012 international conference on computer science and electronics engineering (Vol. 1, pp. 647-651). IEEE.
Tariq, N., Qamar, A., Asim, M., & Khan, F. A. (2020). Blockchain and smart healthcare security: a survey. Procedia Computer Science, 175, 615-620.
Ghorbel, A., Ghorbel, M., & Jmaiel, M. (2021). Accountable privacy preserving attribute-based access control for cloud services enforced using blockchain. International Journal of Information Security, 1-20.
H. Liang, J. Wu, S. Mumtaz, J. Li, X. Lin and M. Wen, "MBID: Micro-blockchain-based geographical dynamic intrusion detection for V2X", IEEE Commun. Mag., vol. 57, no. 10, pp. 77-83, Oct. 2019.
J. Wu, M. Dong, K. Ota, J. Li, W. Yang and M. Wang, "Fog-Computing-Enabled cognitive network function virtualization for an information-centric future Internet", IEEE Commun. Mag., vol. 57, no. 7, pp. 48-54, Jul. 2019.
L. Wang and X. Zhao, "Research on service composition strategy based on blockchain mechanism in cloud computing environment", Appl. Res. Comput. (Chin.), vol. 26, no. 91, pp. 81-86, 2019.
B. Pittl, W. Mach and E. Schikuta, "Bazaar-blockchain: A blockchain for bazaar-based cloud markets", Proc. IEEE Int. Conf. Services Comput. (SCC), pp. 89-96, Jul. 2018.
Y. Zhang, R. Deng, X. Liu and D. Zheng, "Outsourcing service fair payment based on blockchain and its applications in cloud computing", IEEE Trans. Services Comput., Aug. 2018.
J. Li, J. Wu and L. Chen, "Block-secure: Blockchain based scheme for secure P2P cloud storage", Inf. Sci., vol. 465, pp. 219-231, Oct. 2018.
G. Edoardo, A. Leonardo, B. Roberto, L. Federico, M. Andrea and V. Sassone, "Blockchain-based database to ensure data integrity in cloud computing environments", Proc. Italian Conf. Cybersecur., Jan. 2017.
G. Edoardo, A. Leonardo, B. Roberto, L. Federico, M. Andrea and V. Sassone, "Blockchain-based database to ensure data integrity in cloud computing environments", Proc. Italian Conf. Cybersecur., Jan. 2017.
D. K. Tosh, S. Shetty, X. Liang, C. Kamhoua and L. Njilla, "Consensus protocols for blockchain-based data provenance: Challenges and opportunities", Proc. IEEE 8th Annu. Ubiquitous Comput. Electron. Mobile Commun. Conf. (UEMCON), pp. 469-474, Oct. 2017
X. Liang, S. Shetty, D. Tosh, C. Kamhoua, K. Kwiat and L. Njilla, "ProvChain: A blockchain-based data provenance architecture in cloud environment with enhanced privacy and availability", Proc. 17th IEEE/ACM Int. Symp. Cluster Cloud Grid Comput. (CCGRID), pp. 468-477, May 2017.
D. Tosh, S. Shetty, P. Foytik, C. Kamhoua and L. Njilla, "CloudPoS: A proof-of-stake consensus design for blockchain integrated cloud", Proc. IEEE 11th Int. Conf. Cloud Comput. (CLOUD), pp. 302-309, Jul. 2018.
Ouaddah, A., Mousannif, H., Abou Elkalam, A., & Ouahman, A. A. (2017). Access control in the Internet of Things: Big challenges and new opportunities. Computer Networks, 112, 237-262.
Debnath, D., Chettri, S. K., & Dutta, A. K. (2022). Security and privacy issues in internet of things. In ICT Analysis and Applications (pp. 65-74). Springer Singapore.
M, P., & K, D. S. D. (2023). ICN Scheme and Proxy re-encryption for Privacy Data Sharing on the Block Chain. International Journal of Computer Engineering in Research Trends, 10(4), 172–176.
M. R. Arun , M. R. Sheeba , F. Shabina Fred Rishma,(2020). Comparing BlockChain with other Cryptographic Technologies (DAG, Hashgraph, Holochain). International Journal of Computer Engineering in Research Trends, 7(4), 13–19.
Ashesh K Chaudhuri , Mani S Sen (2019). Digital Technologies and Its Scope in Shoplifting Prevention. International Journal of Computer Engineering in Research Trends, 6(10), 1–3.
Ayushi Singh , Gulafsha Shujaat , Isha Singh , Abhishek Tripathi , Divya Thakur (2019). A Survey of Blockchain Technology Security. International Journal of Computer Engineering in Research Trends, 6(4), 299–303.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





