Intelligent Secure and Malicious-Free Route Management Strategy for IoT-based Wireless Sensor Networks
Keywords:
ICARS, IoT Security, Secure routing, MRA, Wireless sensor networksAbstract
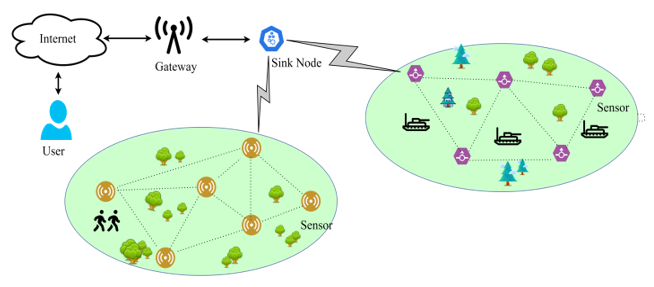
Advancements in smart-network technologies enabled the Internet of Things to expand globally. IoT-based Wireless sensor networks play an essential role in collecting and aggregating data in applications like military and health care, where security and power efficiency are significant challenges. Due to vulnerable attacks on several nodes or devices, IoT-based WSN becomes an uncertain environment. This paper aims to offer a fault tolerant, robust, and secure packet forwarding scheme that incorporates more intelligent features and powerful algorithms to eliminate DoS attacks. Initially, routing is performed, with the optimal path determined by recovering malicious nodes detected in an IOT-based WSN environment using the proposed algorithm ICARS- Intelligent Channel aware Reputation scheme based on generation of Resolver Node and Intelligent Route Request and Route Response methods. Next to that, encryption is used to ensure safe transmission. This paper proposes a Modified Rijndael Algorithm (MRA) for secured authentication. By integrating ICARS with MRA, this proposed strategy removes the attacking situation and makes the system more resistant to DoS attacks. The result section proved that the proposed approach increases the throughput, decreases the retransmission ratio, increases energy efficiency, decreases end-to-end delay, and increases Packet Delivery Ratio.
Downloads
References
Fang W., Zhang W., Chen W., Liu J., Ni Y., Yang Y. MSCR: Multidimensional secure clustered routing scheme in hierarchical wireless sensor networks. EURASIP Journal on Wireless Communications and Networking. 2021. 2021:1-20.
Sirajuddin M., Kumar B.S. Efficient and Secured Route Management Scheme Against Security Attacks in Wireless Sensor Networks. In2021 Second International Conference on Electronics and Sustainable Communication Systems (ICESC). 2021. 1045-1051. IEEE.
Alotaibi M., Improved blowfish algorithm-based secure routing technique in IoT-based WSN. IEEE Access. 2021. 9:159187-97.
Adnan M., Yang L., Ahmad T., Tao Y. An unequally clustered multi-hop routing protocol based on fuzzy logic for wireless sensor networks. IEEE Access. 2021. 9:38531-45.
Talukdar M.I., Hassan R., Hossen M.S., Ahmad K., Qamar F., Ahmed A.S. Performance improvements of AODV by black hole attack detection using IDS and digital signature. Wireless Communications and Mobile Computing. 2021. 2021:1-3.
Payton E., Khubchandani J., Thompson A., Price J.H. Parents’ expectations of high schools in firearm violence prevention. Journal of community health. 2017. 42:1118-26.
Gousia Thahniyath., Jayaprasad M. Secure and load balanced routing model for wireless sensor networks. Journal of King Saud University-Computer and information sciences. 2023. 35(7); DOI:https://doi.org/10.1016/j.jksuci.2020.10.012.
Rathee M., Kumar S., Gandomi A.H., Dilip K., Balusamy B., Patan R. Ant colony optimization based quality of service aware energy balancing secure routing algorithm for wireless sensor networks. IEEE Transactions on Engineering Management. 2019. 68(1):170-82.
Selvi M., Thangaramya K., Ganapathy S., Kulothungan K., Khannah Nehemiah H., Kannan A. An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wireless Personal Communications. 2019. 105:1475-90.
Chandre P.R., Mahalle P.N., Shinde G.R. Machine learning based novel approach for intrusion detection and prevention system: A tool based verification. In2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN). 2018. 135-140. IEEE.
Sunitha R., Chandrikab J., Evolutionary computing assisted wireless sensor network mining for qos-centric and energy-efficient routing protocol. International Journal of Engineering. 2020. 33(5):791-7.
Rana, P. ., Sharma, V. ., & Kumar Gupta, P. . (2023). Lung Disease Classification using Dense Alex Net Framework with Contrast Normalisation and Five-Fold Geometric Transformation. International Journal on Recent and Innovation Trends in Computing and Communication, 11(2), 94–105. https://doi.org/10.17762/ijritcc.v11i2.6133
Karthick S., Devi E.S., Nagarajan R.V. Trust-distrust protocol for the secure routing in wireless sensor networks. In2017 International conference on algorithms, methodology, models and applications in emerging technologies (ICAMMAET). 2017. 1-5. IEEE.
Jinhui X., Yang T., Feiyue Y., Leina P., Juan X., Yao H. Intrusion detection system for hybrid DoS attacks using energy trust in wireless sensor networks. Procedia computer science. 2018. 131:1188-95.
Deebak B.D., Al-Turjman F. A hybrid secure routing and monitoring mechanism in IoT-based wireless sensor networks. Ad Hoc Networks. 2020. 97:102022.
Seyyedabbasi A., Kiani F. MAP-ACO: An efficient protocol for multi-agent pathfinding in real-time WSN and decentralized IoT systems. Microprocessors and Microsystems. 2020. 79:103325.
Prakash S., Saroj V. A review of wireless charging nodes in wireless sensor networks. Data Science and Big Data Analytics: ACM-WIR 2018. 2018. 177-88.
Amin A., Liu X.H., Saleem M.A., Henna S., Islam T.U., Khan I., Uthansakul P., Qurashi M.Z., Mirjavadi S.S., Forsat M. Collaborative wireless power transfer in wireless rechargeable sensor networks. Wireless Communications and Mobile Computing. 2020. 2020.
Jasper J. A secure routing scheme to mitigate attack in wireless adhoc sensor network. Computers & Security. 2021 Apr 1;103:102197.
Faris, W. F. . (2020). Cataract Eye Detection Using Deep Learning Based Feature Extraction with Classification. Research Journal of Computer Systems and Engineering, 1(2), 20:25. Retrieved from https://technicaljournals.org/RJCSE/index.php/journal/article/view/7
Lai Y., Tong L., Liu J., Wang Y., Tang T., Zhao Z., Qin H. Identifying malicious nodes in wireless sensor networks based on correlation detection. Computers & Security. 2022. 113:102540.
Heinzelman W.B., Chandrakasan A.P., Balakrishnan H. An application-specific protocol architecture for wireless microsensor networks. IEEE Transactions on wireless communications. 2002. 1(4):660-70.
Raju B.B., Krishna A., Mishra G. Implementation of an efficient dynamic AES algorithm using ARM based SoC. In2017 4th IEEE Uttar Pradesh Section International Conference on Electrical, Computer and Electronics (UPCON) 2017 Oct 26 (pp. 39-43). IEEE
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





