A Novel Approach to Blockchain and Deep Learning in the field of Steganography
Keywords:
Steganography, Deep Learning, Blockchain, confidentiality, cyber securityAbstract
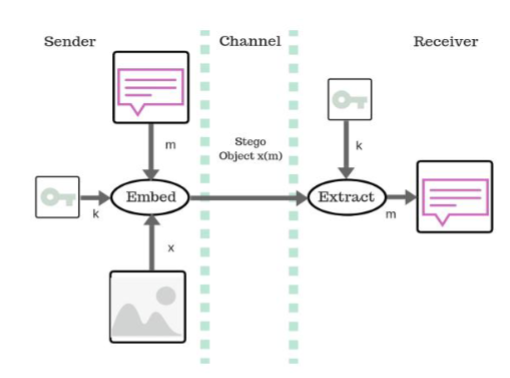
Our daily lives have been changed by electronic technology. To maintain cybersecurity, secure and reliable connection is necessary, to improve the robustness and effectiveness of these techniques Securing a large amount of data is a major challenge during the communication of data over the network. Confidentiality and integrity play an important role while transferring the data in the field of health, defence, and conference meetings. As a result, this study suggests using Blockchain and Deep Learning in addition to innovative steganography. Along with this the hash function is used to hide the secret data which provides high entrenching capability and high eminence data input images. Stego images along with hash function generating datasets, along with Blockchain technology are used to improve the efficiency of securing the data during communication over network. In the proposed model the deep learning algorithms adds the more security to the data that is stored in the Blockchain. The data extracted using deep learning is stored in the Blockchain which is free from null values, and duplicate values. Thus the proposed model helps in achieving securing the data in more efficient way by avoiding third party to hack the data.
Downloads
References
Zheng, Zibin, Shaoan Xie, Hongning Dai, Xiangping Chen, and Huaimin Wang. "An overview of blockchain technology: Architecture, consensus, and future trends." In 2017 IEEE international congress on big data (BigData congress), pp. 557-564. Ieee, 2017.
Prayagi, Harsh, Tushar Srivastava, Gyanendra Ojha, and Sunil Chaurasia. "Information Hiding in an Image File: Steganography." IJCSIT) International Journal of Computer Science and Information Technologies 3, no. 3 (2012): 4216-4217.
Evans, J. A. S. "Histiaeus and Aristagoras: Notes on the Ionian Revolt." The American Journal of Philology 84, no. 2 (1963): 113-128.
Sumathi, C. P., T. Santanam, and G. Umamaheswari. "A study of various steganographic techniques used for information hiding." arXiv preprint arXiv:1401.5561 (2014).
Agarwal, Namita, Amit Kumar Singh, and Pradeep Kumar Singh. "Survey of robust and imperceptible watermarking." Multimedia Tools and Applications 78, no. 7 (2019): 8603-8633.
Hamamreh, Rushdi A., and Mohammed A. Jamoos. "Hash algorithm for data integrity based on matrix combination." In The 14th International Arab Conference on Information Technology (ACIT'2013). 2014.
Hill, Brenn, Samanyu Chopra, and Paul Valencourt. Blockchain Quick Reference: A guide to exploring decentralized blockchain application development. Packt Publishing Ltd, 2018.
Hyla, Tomasz, and Jerzy Pejaś. "Long-term verification of signatures based on a blockchain." Computers & Electrical Engineering 81 (2020): 106523.
Mohammed, Mohssen, Muhammad Badruddin Khan, and Eihab Bashier Mohammed Bashier. Machine learning: algorithms and applications. Crc Press, 2016.
Laskov, Pavel, Patrick Düssel, Christin Schäfer, and Konrad Rieck. "Learning intrusion detection: supervised or unsupervised?." In International Conference on Image Analysis and Processing, pp. 50-57. Springer, Berlin, Heidelberg, 2005.
Shinde, Rucha, Shruti Patil, Ketan Kotecha, Vidyasagar Potdar, Ganeshsree Selvachandran, and Ajith Abraham."Securing AI-based Healthcare Systems using Blockchain Technology: A State-of-the-Art Systematic Literature Review and Future Research Directions." arXiv preprint arXiv:2206.04793 (2022).
Hameed, Rana Sami, Bin Hj Ahmad Abd Rahim, Mustafa Muneeb Taher, And Siti Salasiah Mokri. "A Literature Review Of Various Steganography Methods." Journal of Theoretical and Applied Information Technology 100, no. 5 (2022).
Das, Indrajit, Shalini Singh, Sonali Gupta, Amogh Banerjee, Md Golam Mohiuddin, and Shubham Tiwary. "Design and implementation of secure ATM system using machine learning and crypto–stego methodology." SN Applied Sciences 1, no. 9 (2019): 1-14.
Boughaci, Dalila, and Hanane Douah. "A Variable Neighborhood Search-Based Method with Learning for Image Steganography." In Sustainable Development and Social Responsibility—Volume 2, pp. 7-18. Springer, Cham, 2020.
Kadhim, Inas Jawad, Prashan Premaratne, Peter James Vial, and Brendan Halloran. "Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research." Neurocomputing 335 (2019): 299-326.
Sahu, Aditya Kumar, and Monalisa Sahu. "Digital image steganography and steganalysis: A journey of the past three decades." Open Computer Science 10, no. 1 (2020): 296-342.
Płachta, Mikołaj, Marek Krzemień, Krzysztof Szczypiorski, and Artur Janicki. "Detection of Image Steganography Using Deep Learning and Ensemble Classifiers." Electronics 11, no. 10 (2022): 1565.
Ong, Eng-Jon, Syed Sameed Husain, Mikel Bober-Irizar, and Miroslaw Bober. "Deep architectures and ensembles for semantic video classification." IEEE Transactions on Circuits and Systems for Video Technology 29, no. 12 (2018): 3568-3582.
Kilincer, Ilhan Firat, Fatih Ertam, and Abdulkadir Sengur. "Machine learning methods for cyber security intrusion detection: Datasets and comparative study." Computer Networks 188 (2021): 107840.
Mohsin, Ali H., A. A. Zaidan, B. B. Zaidan, K. I. Mohammed, Osamah Shihab Albahri, Ahmed Shihab Albahri, and M. A. Alsalem. "PSO–Blockchain-based image steganography: towards a new method to secure updating and sharing COVID-19 data in decentralised hospitals intelligence architecture." Multimedia tools and applications 80, no. 9 (2021): 14137-14161.
Dey, Somdip. "Securing majority-attack in blockchain using machine learning and algorithmic game theory: A proof of work." In 2018 10th computer science and electronic engineering (CEEC), pp. 7-10. IEEE, 2018.
Bhattacharyya, Souvik. "A survey of steganography and steganalysis technique in image, text, audio and video as cover carrier." Journal of global research in computer science 2, no. 4 (2011).
Perez, Andres, Valentina Sanguineti, Pietro Morerio, and Vittorio Murino. "Audio-visual model distillation using acoustic images." In Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision, pp. 2854-2863. 2020.
Badr, Sherif M., Goada Ismaial, and Ashgan H. Khalil. "A review on steganalysis techniques: from image format point of view." International Journal of Computer Applications 102, no. 4 (2014).
Kraetzer, Christian, and Jana Dittmann. "Pros and cons of mel-cepstrum based audio steganalysis using SVM classification." In International Workshop on Information Hiding, pp. 359-377. Springer, Berlin, Heidelberg, 2007.
Sarkar, Proton, Sudipta Kumar Ghosal, and Madhulina Sarkar. "Stego-chain: A framework to mine encoded stego-block in a decentralized network." Journal of King Saud University-Computer and Information Sciences (2020).
Sundaram, B. Barani, Sudhanshu Maurya, P. Karthika, and P. Vidhya Saraswathi. "Enhanced the Data Hiding in Geometrical image using stego-Crypto techniques with machine laerning." In 2021 6th International Conference on Inventive Computation Technologies (ICICT), pp. 1141-1144. IEEE, 2021.
Sun, Yuanyuan, Jiajia Liu, Jiadai Wang, Yurui Cao, and Nei Kato. "When machine learning meets privacy in 6G: A survey." IEEE Communications Surveys & Tutorials 22, no. 4 (2020): 2694-2724.
Takaoğlu, Mustafa, Adem Özyavaş, Naim Ajlouni, Ali Alshahrani, and Basil Alkasasbeh. "A Novel and Robust Hybrid Blockchain and Steganography Scheme." Applied Sciences 11, no. 22 (2021): 10698.
Madhura, K., and R. Mahalakshmi. "Designing an optimized confidential-data management system using preeminent access-control and block-chain." International Journal of Intelligent Computing and Cybernetics (2022).
Madhura, K., and R. Mahalakshmi. "Survey on Technologies, Benefits, Challenges and Future Suggestions to Improvise the Data Security of Confidential Academic Records in India." In 2021 9th International Conference on Cyber and IT Service Management (CITSM), pp. 1-9. IEEE, 2021.
Manjula, H. M., and S. P. AnandaRaj. "Ayurvedic Diagnosis using Machine Learning Techniques to examine the diseases by extracting the data stored in AyurDataMart." In 2021 3rd International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), pp. 239-244. IEEE, 2021.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Ayushi Chaudhary, Ashish Sharma, Neeraj Gupta

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
All papers should be submitted electronically. All submitted manuscripts must be original work that is not under submission at another journal or under consideration for publication in another form, such as a monograph or chapter of a book. Authors of submitted papers are obligated not to submit their paper for publication elsewhere until an editorial decision is rendered on their submission. Further, authors of accepted papers are prohibited from publishing the results in other publications that appear before the paper is published in the Journal unless they receive approval for doing so from the Editor-In-Chief.
IJISAE open access articles are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. This license lets the audience to give appropriate credit, provide a link to the license, and indicate if changes were made and if they remix, transform, or build upon the material, they must distribute contributions under the same license as the original.





